Malware Analysis – evasion – 47bd2deca914a1687586f1532cd17c20
Score: 9 MALWARE FAMILY: evasionTAGS:evasion, persistence, ransomware, spyware, stealerMD5: 47bd2deca914a1687586f1532cd17c20SHA1: 4c698a81f7cd469276808c6f8244c9ccabc5291fANALYSIS DATE: 2023-06-23T17:13:58ZTTPS: T1490, T1031, T1562, T1489, T1082, T1005, T1081,...





![[TRYHACKME] - Void Execution Challenge 8 void_execution](https://www.redpacketsecurity.com/wp-content/uploads/2025/09/void_execution-150x150.png)















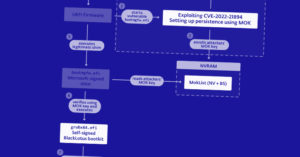
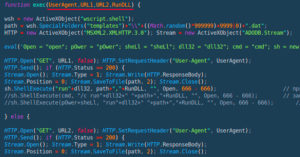
![Cobalt Stike Beacon Detected - 47[.]241[.]225[.]61:443 29 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)

![[PEAR] - Ransomware Victim: Gerson & Schwartz Accident & Injury Lawyers 42 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
