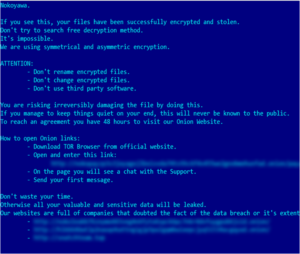
Fortinet FortiNAC information disclosure | CVE-2022-43951
NAME__________Fortinet FortiNAC information disclosurePlatforms Affected:Risk Level:5.3Exploitability:UnprovenConsequences:Obtain Information DESCRIPTION__________Fortinet FortiNAC could allow a remote attacker to obtain sensitive information. By sending...





![[TRYHACKME] - Void Execution Challenge 8 void_execution](https://www.redpacketsecurity.com/wp-content/uploads/2025/09/void_execution-150x150.png)

















![[eBook] A Step-by-Step Guide to Cyber Risk Assessment 40 cye](https://www.redpacketsecurity.com/wp-content/uploads/2023/04/cye-300x157.png)
![LockBit 3.0 Ransomware Victim: gregoire[.]fr 41 image-11](https://www.redpacketsecurity.com/wp-content/uploads/2022/06/image-11-300x142.png)
![[RHYSIDA] - Ransomware Victim: Invacare 42 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)


