Ransomware Gang Behind Threats To Fred Hutch Cancer Patients

The Hunters International ransomware gang claimed to be behind a cyberattack on the Fred Hutchinson Cancer Center (Fred Hutch) that resulted in patients receiving personalized extortion threats.
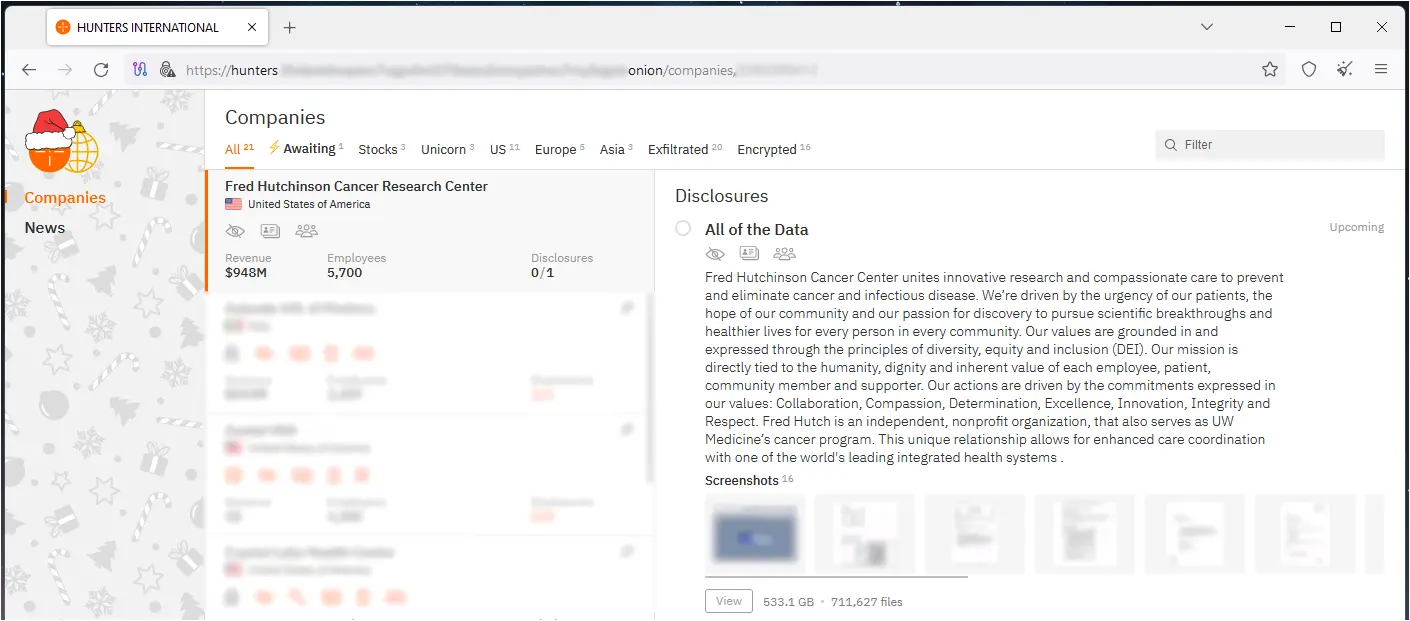
Fred Hutch is a Seattle-based cancer research and patient care and treatment center operating a network of more than ten clinical sites in the region.
At the start of the month, the hospital disclosed a cybersecurity incident that occurred on November 19, 2023, involving unauthorized access to its networks.
The health organization quarantined the impacted servers, took its clinical network offline to prevent the spread of the threat, and notified the federal law enforcement authorities of the attack.
The investigation conducted with the help of a leading forensic expert has not produced evidence that the attackers stole patient data, according to the notice on Fred Hutch’s website. However, investigations on that front haven’t been completed yet.
Today, the ransomware group Hunters International has added Fred Hutchinson to their extortion portal on the dark web, threatening the healthcare organization with leaking 533.1GB of data allegedly stolen from its networks.
The threat actors have only published thumbnails of select documents they claim to have exfiltrated from Fred Hutch’s networks, so the blackmail is still underway.
Patients threatened
Last week, it was reported that the threat actors responsible for the attack on Fred Hutch were emailing patients individually, threatening them with public disclosure of their sensitive data.
As reported by the Seattle Times, the attackers emailed many patients stating they have the names, Social Security numbers, phone numbers, medical history, lab results, and insurance history of over 800,000 patients.
“If you are reading this, your data has been stolen and will soon be sold to various data brokers and black markets to be used in fraud and other criminal activities,” reads the emails seen by the Seattle Times.
These emails reportedly contained recipients’ personal information as proof, including a patient’s address, phone number, and medical record number, and a link to a site where they could pay $50 to prevent the data from being sold.
Fred Hutch issued a warning about the email messages and notified law enforcement. Also, they told patients who received the emails not to pay the threat actors and instead block the sender and delete the email.
Calling or emailing customers, contractors, and partners of a breached organization to pressure the victim is not new to ransomware. However, it is not common for threat actors to offer exposed individuals a way to prevent their data from being released.
Hunters International is a fairly new Ransomware-as-a-Service (RaaS) operation that is believed to be a rebrand of the Hive ransomware operation due to similarities in the encryptor’s code.
However, Hunters International has denied any connection to Hive, saying that they purchased the software and website from the defunct ransomware operation.
The threat actors target companies of all sizes, with ransom demands seen by BleepingComputer ranging between hundreds of thousands to millions of dollars.
Last week, the threat group claimed an attack against Austal USA, a prominent shipbuilding contractor for the U.S. government.
