Ransomware updates & 1-day exploits


Introduction
In our crimeware reporting service, we analyze the latest crime-related trends we come across. Last month, we again posted a lot on ransomware, but we also covered other subjects, such as 1-day exploits. In this blogpost, we provide excerpts from these reports.
For questions or more information about our crimeware reporting service, please contact [email protected].
RedAlert / N13V: yet another multiplatform ransomware variant
RedAlert (aka N13V) is the latest in the multiplatform ransomware trend we described here and here. The difference this time, though, is that it is not written in a cross-platform language but in C — at least the Linux version that we could get our hands on, was. It does, however, explicitly support ESXi environments. For example, it has the command-line option “-w”, which stops running VMs, and it also searches for VMWare-based VMs as can be seen from the screenshots below.
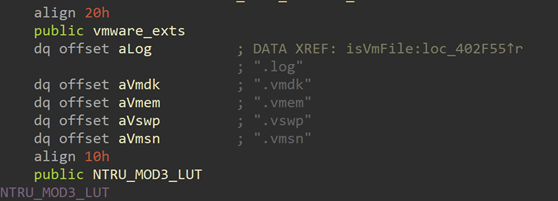

Note the specific VMWare-related strings the malware looks for
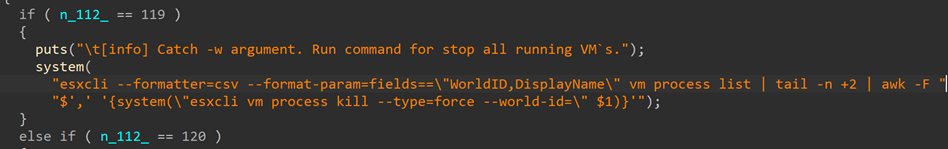

Stopping VMs
Interestingly, the group mentions on their onion website that a decryptor is available on all platforms. Unfortunately, we could not get our hands on the other versions, so we don’t know whether the decryptor is written in a cross-platform language or not.
Another aspect that sets RedAlert apart from other ransomware groups is that they only accept payments in Monero. From a criminal point of view, the advantage is that payments cannot be traced. The problem, however, is that Monero is not accepted in every country or by every exchange, making a ransom payment more difficult for the victim.
Since the group is relatively young, we couldn’t find out a lot about the victimology, but RedAlert stands out as an interesting example of a group that managed to adjust their code written in C to different platforms.
Monster: Ransomware with a GUI
In July, our Darknet monitoring system detected yet another new cross-platform ransomware variant: Monster. There are a couple of peculiar properties about Monster. First, unlike other new ransomware families that are written in modern cross-platform languages (e.g. Rust, Go), Monster is written in Delphi. Second, the malware has a GUI.
This latter property is especially peculiar, as we do not remember seeing this before. There are good reasons for this, because, why would one go through the effort of implementing this when most ransomware attacks are executed using the command line in an automated way during a targeted attack? The ransomware authors must have realized this as well, since they included the GUI as an optional command-line parameter.
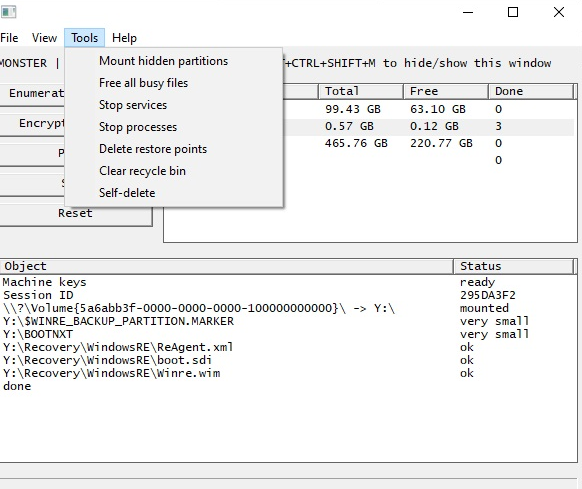

GUI used by Monster
The rest of the ransomware is fairly typical. RSA + AES are used, and multiple threads help to speed up the encryption and decryption process.
In terms of victimology, we found a couple of victims located all over the world (Singapore, Indonesia, Bolivia).
CVE-2022-24521: private 1-day exploits used for attacking Windows 7-11
Cybercriminals have the capabilities to create so-called 1-day exploits within a matter of day(s) after the vulnerability is reported or fixed. This is the reason why many security professionals urge system admins and users to install security patches as soon as possible.
One such example is CVE-2022-24521, an arbitrary pointer dereference in the Common Log File System (CLFS) driver, which has a long history of vulnerabilities. CVE-2022-24521 allows an attacker to gain system privileges on the infected device and is exploited in different ways by various actors. Although this time, it must be said it took the criminals a little bit longer than usual to develop an exploit: two weeks after the vulnerability was disclosed. We did, however, find an exploit with a PE-timestamp dated about one week after the patch was released, indicating that a working exploit might have been available even earlier. In total, we found two different exploits, both having several versions. In both cases, the developers sell exploits privately and do not share them on GitHub or other online platforms.
What is particularly interesting about these exploits is that they support a variety of Windows versions. This is something we usually see in commercial exploits. But the exploits have more in common: the two share a lot of debug messages. Because of these debug messages and the overall design of one of the exploits, we were able to link it to the other exploit for a much older vulnerability in the CLFS driver. In fact, we can say that the older exploit was reused for the newer vulnerability.
Finally, it is worth mentioning that one of the exploits was used in the wild during an attack on a large retailer in the APAC region.
Conclusion
In this blogpost, we stepped away — even though just slightly — from solely covering ransomware. Although ransomware is still one of the biggest threats to organizations, one should realize how these attacks actually take place. Quite often criminals use exploits for which patches are already available, simply because the affected organizations do not have an optimal patching policy.
Proper threat intelligence can help organizations to protect themselves against these types of threats, despite a non-ideal policy. For example, as we highlighted in this blogpost, criminals sometimes reuse older exploit code for newer vulnerabilities. Properly written Yara rules help to catch these newer exploits. Also, discussing TTPs and what is currently popular amongst ransomware groups helps organizations to make better-informed decisions on how to protect their environments.
For any questions about our private reports, please contact [email protected].
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


