Russian hackers use Ngrok feature and WinRAR exploit to attack embassies

After Sandworm and APT28 (known as Fancy Bear), another state-sponsored Russian hacker group, APT29, is leveraging the CVE-2023-38831 vulnerability in WinRAR for cyberattacks.
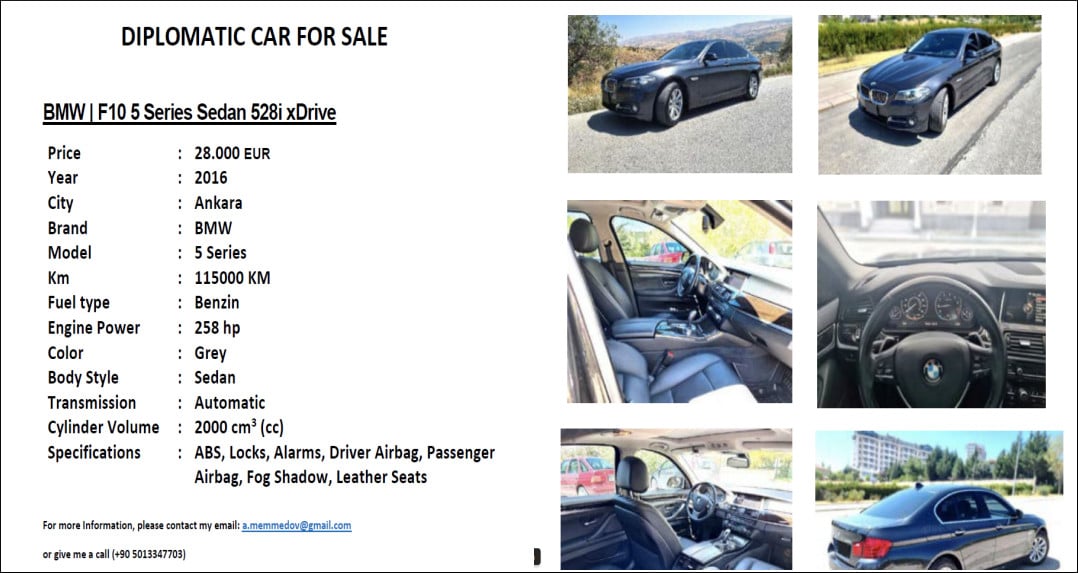
APT29 is tracked under different names (UNC3524,/NobleBaron/Dark Halo/NOBELIUM/Cozy Bear/CozyDuke, SolarStorm) and has been targeting embassy entities with a BMW car sale lure.
The CVE-2023-38831 security flaw affects WinRAR versions before 6.23 and allows crafting .RAR and .ZIP archives that can execute in the background code prepared by the attacker for malicious purposes.
The vulnerability has been exploited as a zero-day since April by threat actors targeting cryptocurrency and stock trading forums.
Ngrok static domain for cover comms
In a report this week, the Ukrainian National Security and Defense Council (NDSC) says that APT29 has been using a malicious ZIP archive that runs a script in the background to show a PDF lure and to download PowerShell code that downloads and executes a payload.
The malicious archive is called “DIPLOMATIC-CAR-FOR-SALE-BMW.pdf” and targeted multiple countries on the European continent, including Azerbaijan, Greece, Romania, and Italy.

source: Ukrainian National Security and Defense Council
APT29 has used the BMW car ad phishing lure before to target diplomats in Ukraine during a campaign in May that delivered ISO payloads through the HTML smuggling technique.
In these attacks, the Ukrainian NDSC says that APT29 combined the old phishing tactic with a novel technique to enable communication with the malicious server.
NDSC says that the Russian hackers used a Ngrok free static domain (a new feature Ngrok announced on August 16) to access the command and control (C2) server hosted on their Ngrok instance.
“In this nefarious tactic, they utilize Ngrok’s services by utilizing free static domains provided by Ngrok, typically in the form of a subdomain under “ngrok-free.app.” These subdomains act as discrete and inconspicuous rendezvous points for their malicious payloads” – National Security and Defense Council of Ukraine
By using this method, the attackers managed to hide their activity and communicate with compromised systems without being the risk of being detected.
Since researchers at cybersecurity company Group-IB reported that the CVE-2023-38831 vulnerability in WinRAR was exploited as a zero-day, advanced threat actors started to incorporate it into their attacks.
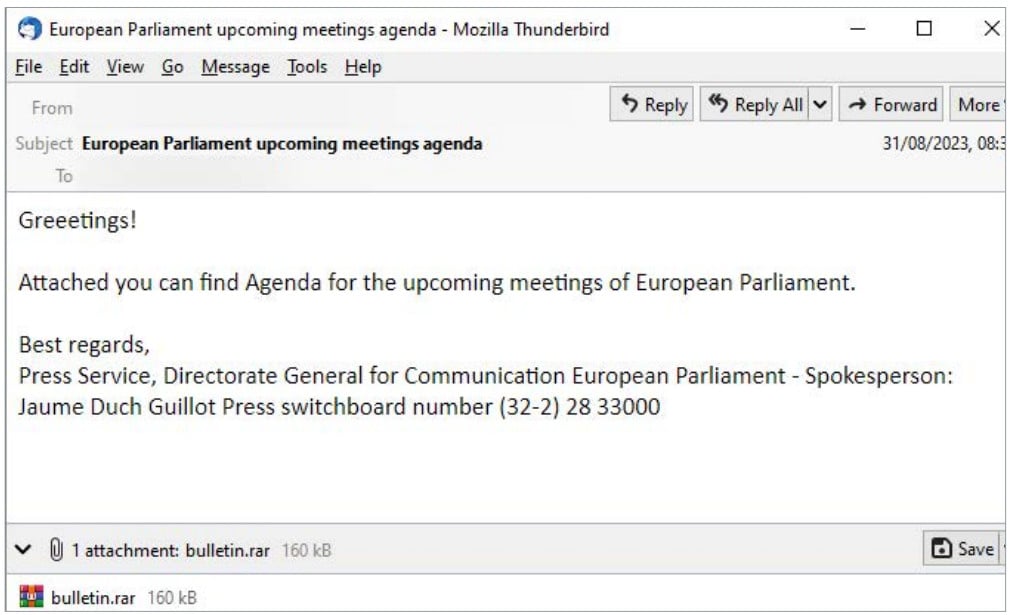
Security researchers at ESET saw attacks in August attributed to the Russian APT28 hacker group that exploited the vulnerability in a spearphishing campaign that targeted political entities in the EU and Ukraine using the European Parliament agenda as a lure.

source: ESET
A report from Google in October notes that the security issue was exploited by Russian and Chinese state hackers to steal credentials and other sensitive data, as well as to establish persistence on target systems.
The Ukrainian NDSC says that the observed campaign from APT29 stands out because it mixes old and new techniques such as the use of the WinRAR vulnerability to deliver payloads and Ngrok services to hide communication with the C2.
The report from the Ukrainian agency provides a set of indicators of compromise (IoCs) consisting of filenames and corresponding hashes for PowerShell scripts and an email file, along with domains and email addresses.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.


