Second colossal LinkedIn “breach” in 3 months, almost all users affected
LinkedIn has reportedly been breached—again—following reports of a massive sale of information scraped from 500M LinkedIn user profiles in the underground in May. According to Privacy Shark, the VPN company who first reported on this incident, a seller called TomLiner showed them he was in possession of 700 million Linkedin user records. That means almost all (92 percent) of LinkedIn’s users are affected by this.
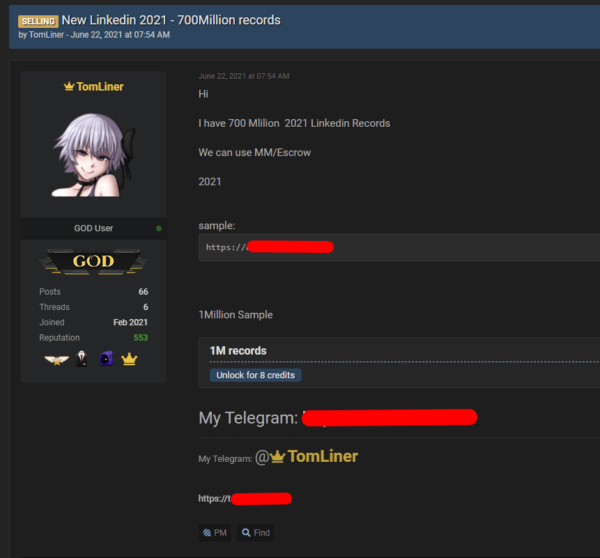

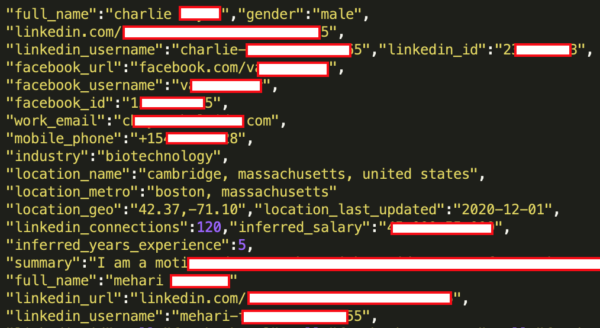
RestorePrivacy, an information site about privacy, examined the proof the seller put out and found the following information, scraped from LinkedIn user profiles:
- Email addresses
- Full names
- Phone numbers
- Physical addresses
- Geolocation records
- LinkedIn username and profile URL
- Personal and professional experience/background
- Genders
- Other social media account usernames
Note that account credentials and banking details don’t appear to be part of the proof. This suggests that the data was scraped rather than breached. Scraping happens when somebody uses a computer program to pull public data from a website, using the website in a way it wasn’t intended to be used. Each individual request or visit is similar to a real user visiting a web page, but the sum total of all the visits leaves the scraper with an enormous database of information.
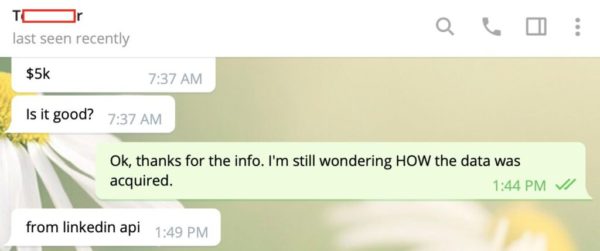
How was the seller able to scrape hundreds of millions of records? According to RestorePrivacy, the seller abused LinkedIn’s API, a similar tactic to the one used in the almost-as-enormous April LinkedIn “breach”, and the huge Facebook “breach” in the same month.

In a statement, Privacy Shark garnered from Leonna Spilman, who spoke on behalf of LinkedIn, the company claims there is really no breach: “While we’re still investigating this issue, our initial analysis indicates that the dataset includes information scraped from LinkedIn as well as information obtained from other sources. This was not a LinkedIn data breach and our investigation has determined that no private LinkedIn member data was exposed. Scraping data from LinkedIn is a violation of our Terms of Service and we are constantly working to ensure our members’ privacy is protected.”
Spilman’s statement echoes the one LinkedIn released after the April “leak” blow out: “We have investigated an alleged set of LinkedIn data that has been posted for sale and have determined that it is actually an aggregation of data from a number of websites and companies. It does include publicly viewable member profile data that appears to have been scraped from LinkedIn. This was not a LinkedIn data breach, and no private member account data from LinkedIn was included in what we’ve been able to review.”

What to do?
Some may read news stories like this and think “Eh, they just got my info that I wanted to be public. It’s not a big deal, right?”
Look at it this way: Having, say, your email address or contact number available for everyone—even strangers—to see is risky. If they know these two things about you, you can be a candidate target for spam campaigns: email, SMS, and robocalls. We don’t know anyone who likes receiving these campaigns.
To make matters worse, the more that scammers know about you, the more plausible and enticing they can make their messages for, and the easier it is for them to pretend to be you when scamming others.
If you’re a LinkedIn user, and you’re worried about the possible repercussions, now is a good time to take the time to sit down and audit your LinkedIn profile.
Start with security: Make sure you have two-factor authentication (2FA) enabled. You may also want to check whether your email address or phone numbers are on HaveIBeenPwned (LinkedIn suffered a genuine breach in 2012, and over 100 million passwords were stolen).
Don’t know what HaveIBeenPwned is? Check our writeup about it what it is and how to use it here!
Take a look at your LinkedIn profile and decide which bits of it you’d rather make private. After all, if a company shows interest in hiring you, you can give them some of your info, such as your contact number, if they ask for it. Better yet, consider setting up a Zoom call with them instead. Remember that you, as a LinkedIn user, can decide which information to show or hide, and who gets to see them, too.
Stay safe!
The post Second colossal LinkedIn “breach” in 3 months, almost all users affected appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.