Shell To Pay: Crims Invade Your Pc With Castlerat Malware, Now In C And Python
A team of data thieves has doubled down by developing its CastleRAT malware in both Python and C variants. Both versions spread by tricking users into pasting malicious commands through a technique called ClickFix, which uses fake fixes and login prompts.
The two variants of the malware, dubbed CastleRAT by security researchers at Recorded Future, are not equal, however. Both will establish a presence and download additional malware via a remote shell, and the Python build can self-delete if necessary. The C build is the most adept – capable of harvesting keystrokes, taking screen captures, and registering persistence.
However, there is a method in this seeming disparity. The Python variant is far sneakier at slipping under the radar.
“The C variant of CastleRAT has yet to be publicly identified, but is flagged by numerous generic antivirus detections not specifically linked to any malware family,” a report from Recorded Future states. “It is therefore plausible that the Python variant of CastleRAT was designed with stealth in mind, as it currently exhibits zero or very few antivirus detections.”
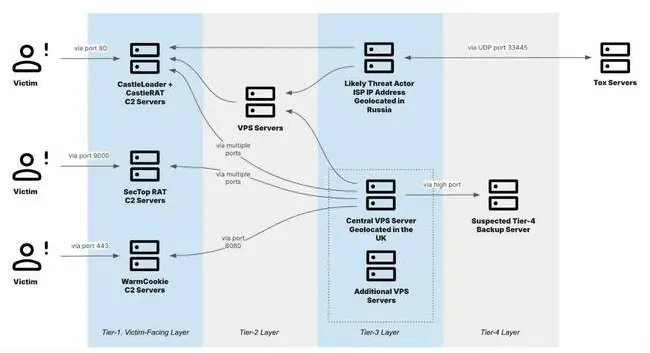
The malware is operated by the TAG-150 criminal crew, which was first identified this spring. They have already developed two other malware families – CastleBot and CastleLoader – which spread through bogus GitHub repositories and by using so-called ClickFix attacks that socially engineer computer users into running the malware themselves.
The ClickFix technique, first spotted last year, uses fake login screens from popular applications and web services, telling the user they have a problem and need to fix it. They instruct the operator to open the Windows Run dialog box or PowerShell terminal and cut and paste malware code into the system to “fix” the problem. And because the user installed the code themselves, it’s more likely to get past security checks.
It’s a disturbingly effective tactic. PRODAFT’s Catalyst platform reports that TAG-150’s CastleLoader code achieved a 28.7 percent success rating in persuading victims to install the malware themselves. As we saw in March, Booking.com customers proved rather easy to fool using this method.
According to the network schematics of the crew, they are a sophisticated international operation. The criminals use Tox Chat, the encrypted comms service that is becoming the tool favored by some malware operators for command and control, via a Russian ISP, and backup data on a virtual private server located in the Netherlands.
The gang operates as a malware-as-a-service operation, according to IBM, selling its infected systems to operators running a variety of info-stealing and ransomware operations. The bulk of their operations are hitting American targets, the report states, but attribution is difficult.
“Given its history of deploying multiple likely self-developed malware families, including CastleLoader, CastleBot, and now CastleRAT, TAG-150 is highly likely to develop and release additional malware in the near term,” the report states.
For defense, Recorded Future recommends using its own services – of course – but also monitoring ports 443 and 7777 for suspicious activity, and of course port 80. And don’t necessarily trust established providers – the researchers observed the malware being hosted from a Google Cloud IP address. ®
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![[Palo Alto Networks Security Advisories] CVE-2025-4614 PAN-OS: Session Token Disclosure Vulnerability 1 Palo_Alto_Networks_Logo](https://www.redpacketsecurity.com/wp-content/uploads/2025/02/Palo_Alto_Networks_Logo-300x55.png)

