Spam and phishing in Q1 2020

Quarterly highlights
Don’t get burned
Burning Man is one of the most eagerly awaited events among fans of spectacular performance and installation art. The main obstacle to attending is the price of admission: a standard ticket will set you back $475, the number is limited, and the buying process is a challenge all by itself (there are several stages, registration data must be entered at a specific time, and if something goes wrong you might not get a second chance). Therefore, half-price fake tickets make for excellent bait.
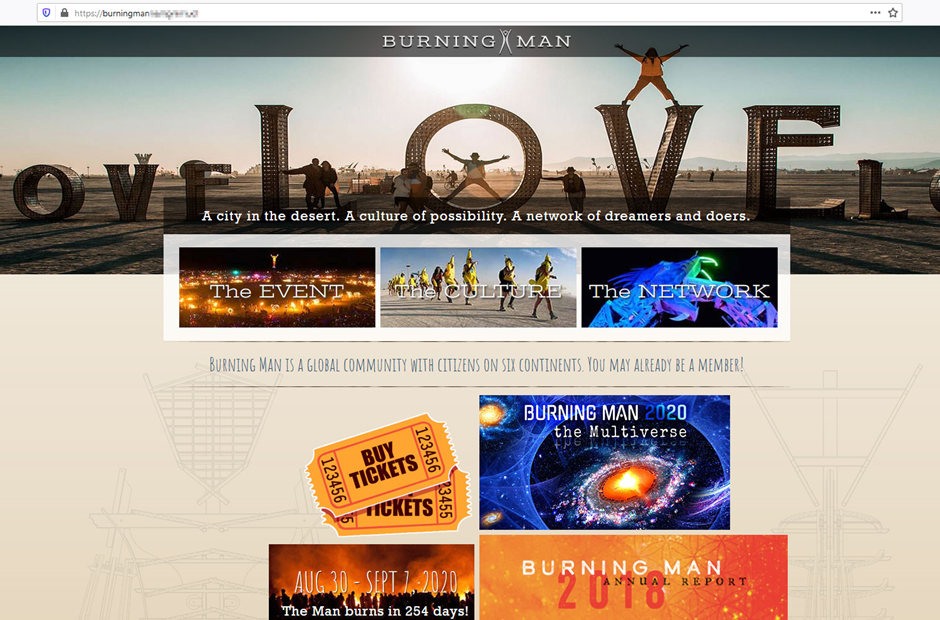

Scammers tried to make their website as close as possible to the original — even the page with the ticket description looked genuine.
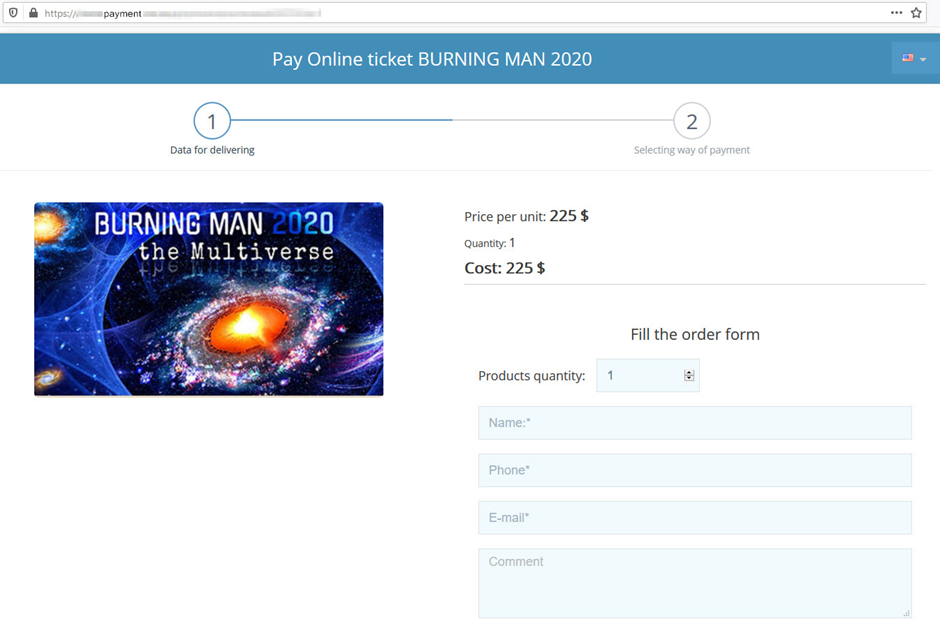

There were just three major differences from the original: only the main page and the ticket purchase section were actually operational, tickets were “sold” without prior registration, and the price was a steal ($225 versus $475).
Oscar-winning scammers
February 2020 saw the 92nd Academy Awards ceremony. Even before the big night, websites were popping up offering free viewings of all the nominated films. Fraudsters targeted users eager to see the short-listed movies before the presentation of the awards.

To promote these sites, Twitter accounts were created — one for each nominated film.
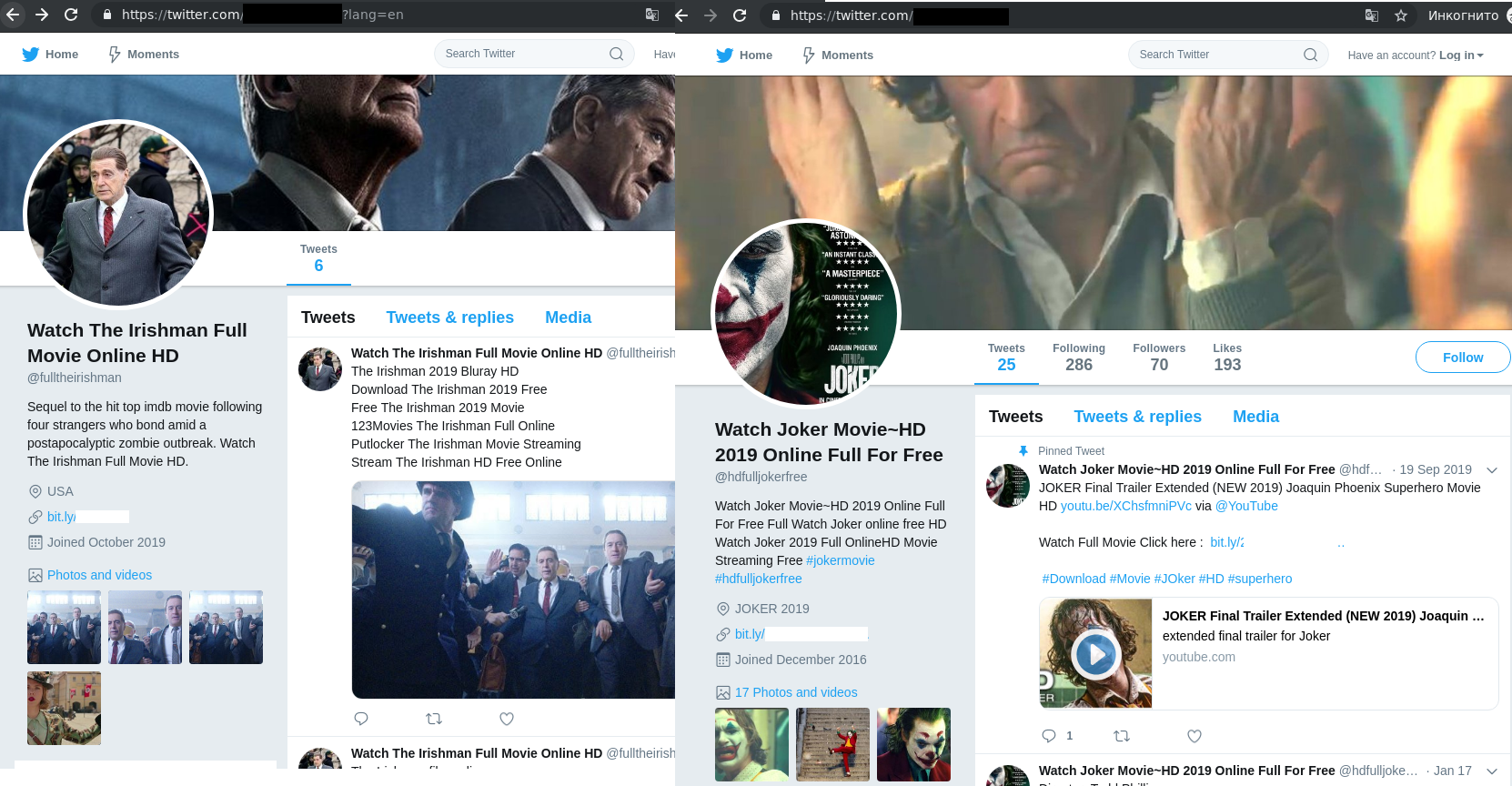

Curious users were invited to visit the resource, where they were shown the first few minutes before being asked to register to continue watching.
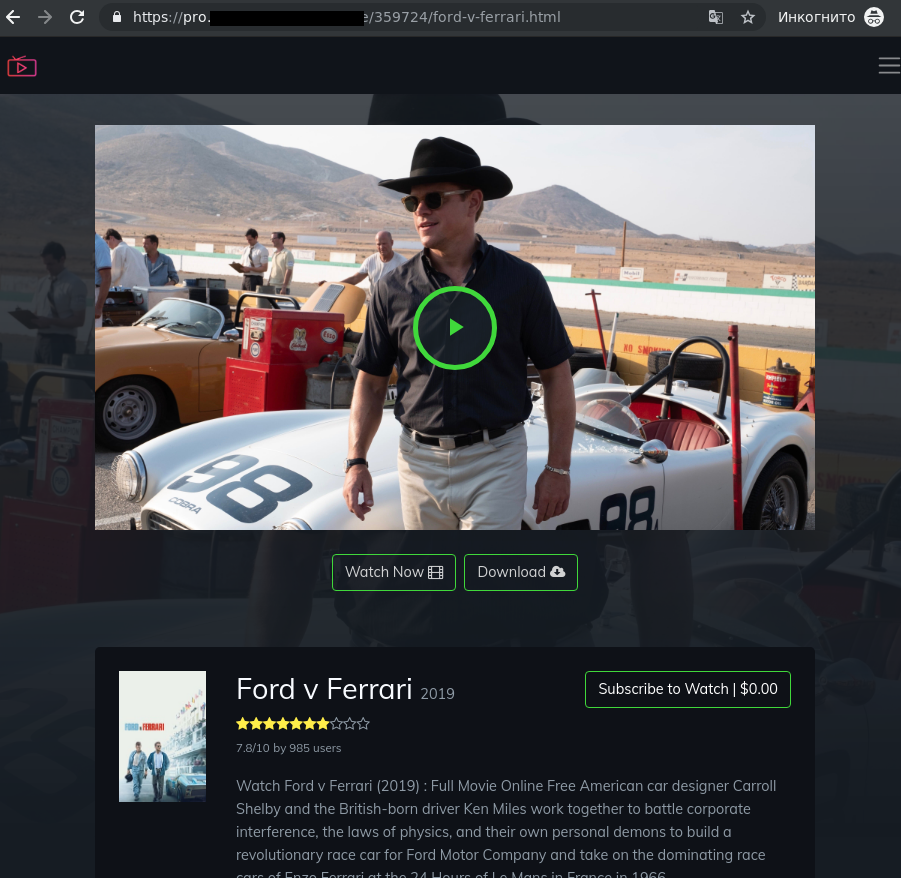

During registration, the victim was prompted to enter their bank card details, allegedly to confirm their region of residence. Unsurprisingly, a short while later a certain amount of money disappeared from their account, and the movie did not resume.

Users should be alert to the use of short links in posts on social networks. Scammers often use them because it’s impossible to see where a shortened URL points without actually following it.
There are special services that let you check what lies behind such links, often with an additional bonus in the form of a verdict on the safety of the website content. It is important to do a proper check on links from untrusted sources.
ID for hire
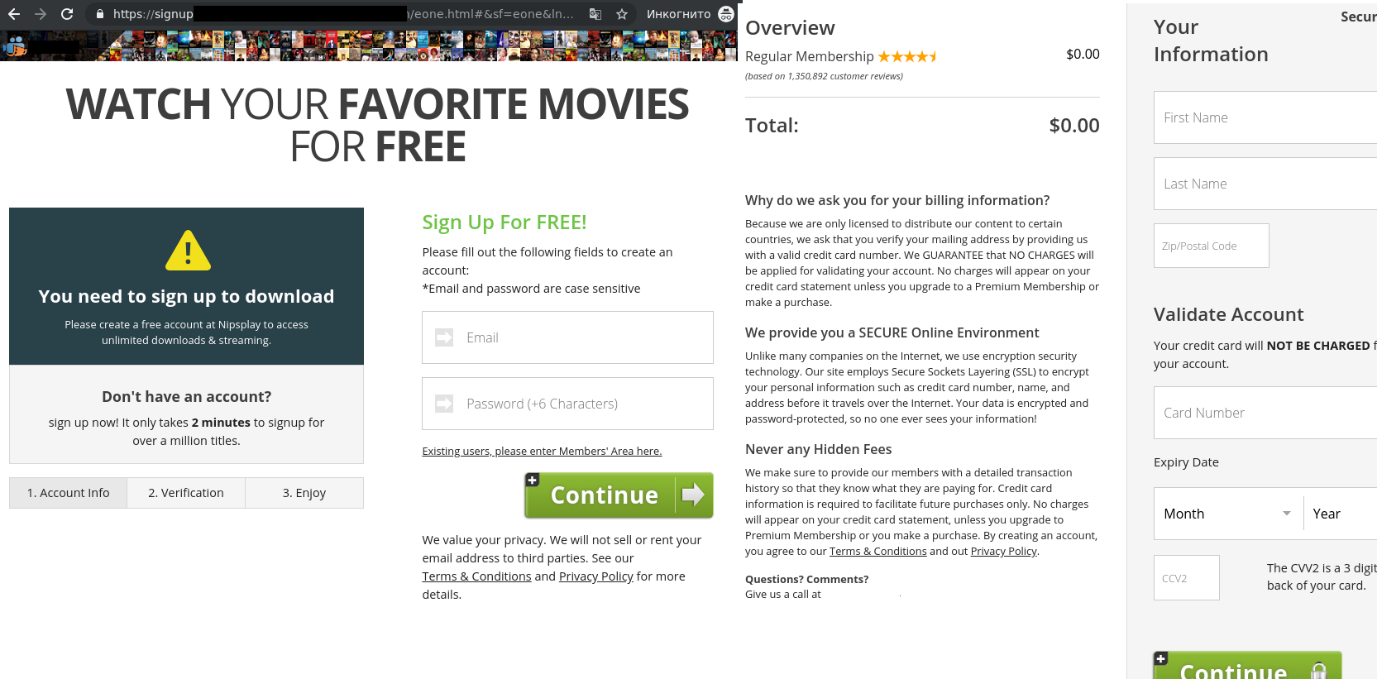
US companies that leak customer data can be heavily fined by the Federal Trade Commission (FTC). For example, in 2019 Facebook was slapped with a $5 billion penalty; however, users whose data got stolen do not receive any compensation. This is what scammers decided to exploit by sending a fake e-mail offering compensation from the non-existent Personal Data Protection Fund, created by the equally fictitious US Trading Commission.
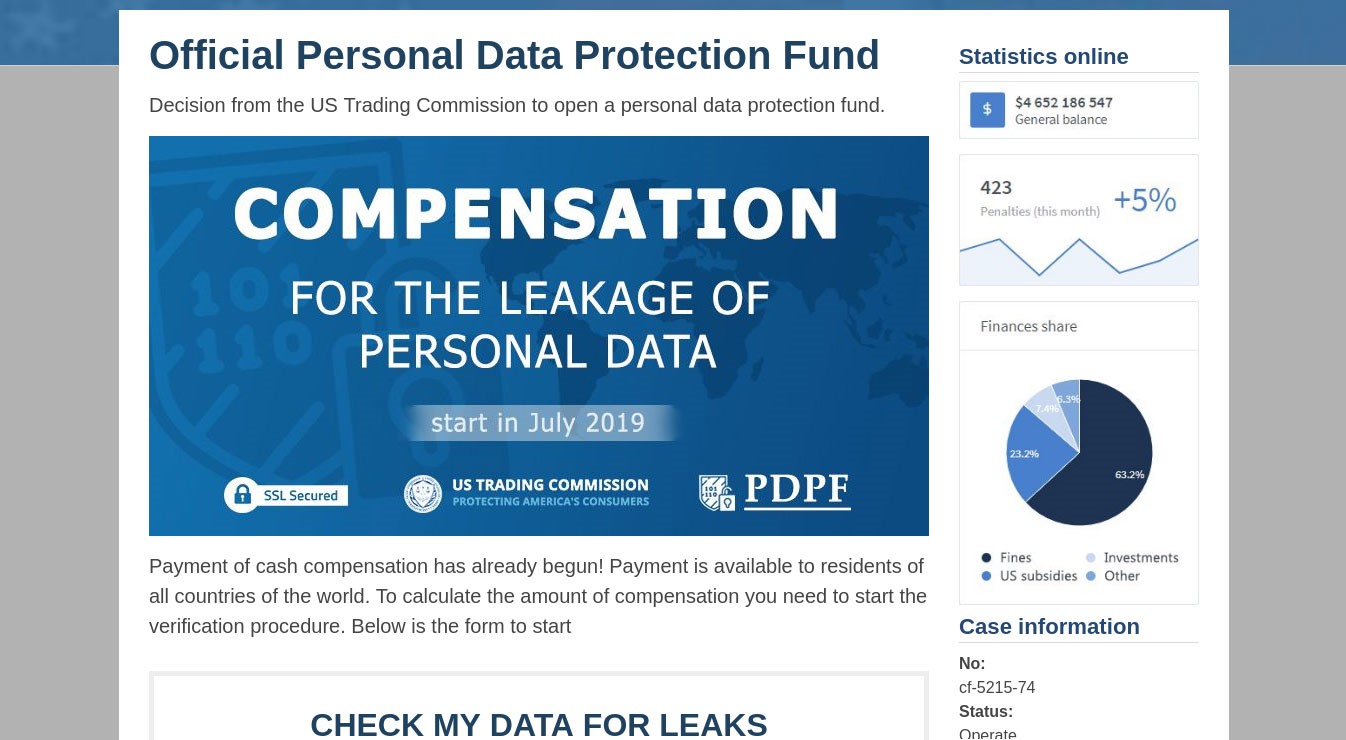

Inspired by the idea of services for checking accounts for leaks, the cybercriminals decided to create their own. Visitors were invited to check whether their account details had been stolen, and if so (the answer was “yes” even if the input was gibberish), they were promised compensation “for the leakage of personal data.”
To receive “compensation,” the victim’s citizenship was of no consequence — what mattered was their first name, last name, phone number, and social network accounts. For extra authenticity, a warning message about the serious consequences of using other people’s data to claim compensation popped up obsessively on the page.
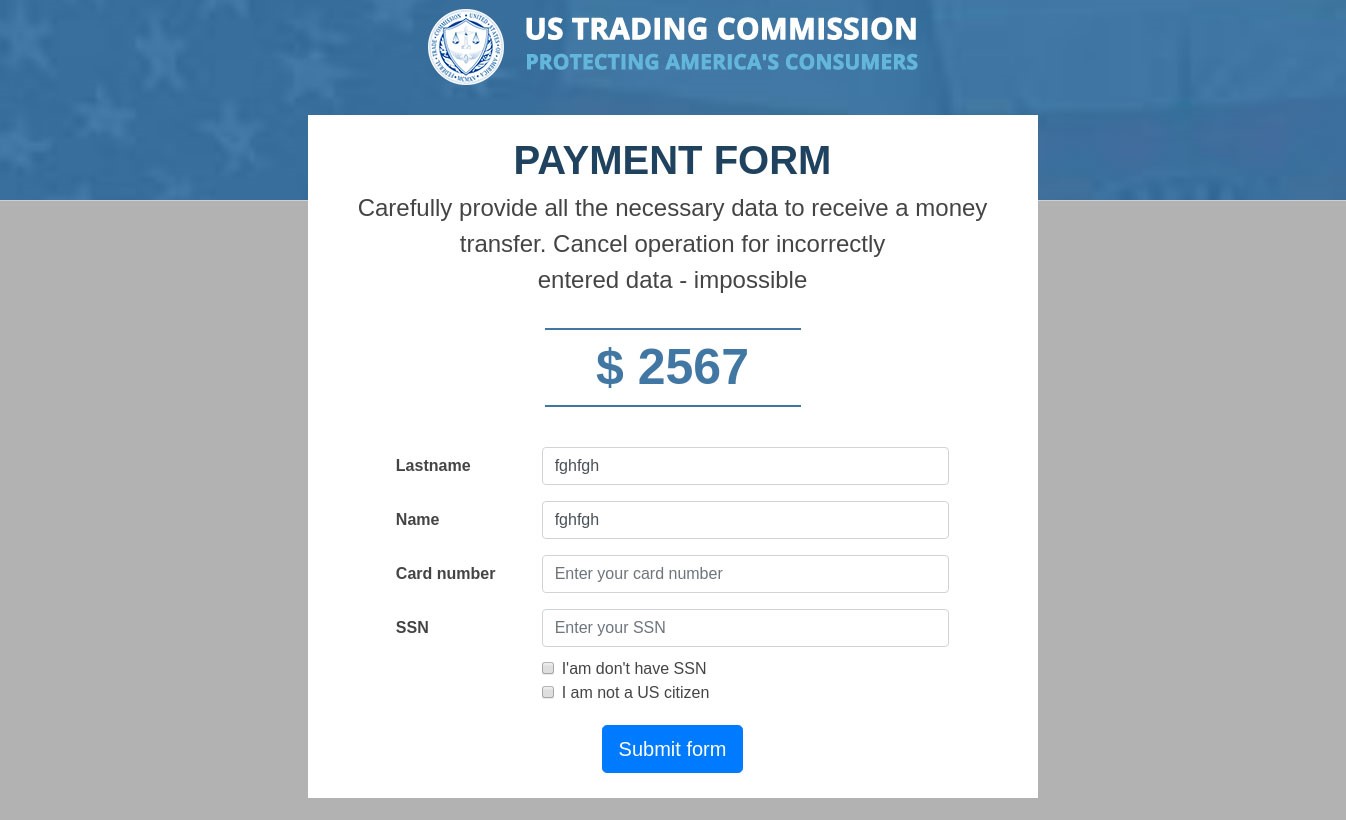

To receive the payment, US citizens were asked to enter their Social Security Number (SSN). Everyone else had to check the box next to the words “I’am don’t have SSN” (the mistakes are a good indicator of a fake), whereupon they were invited to “rent” an SSN for $9. Interestingly, even if the user already had an SSN, they were still pestered to get another one.
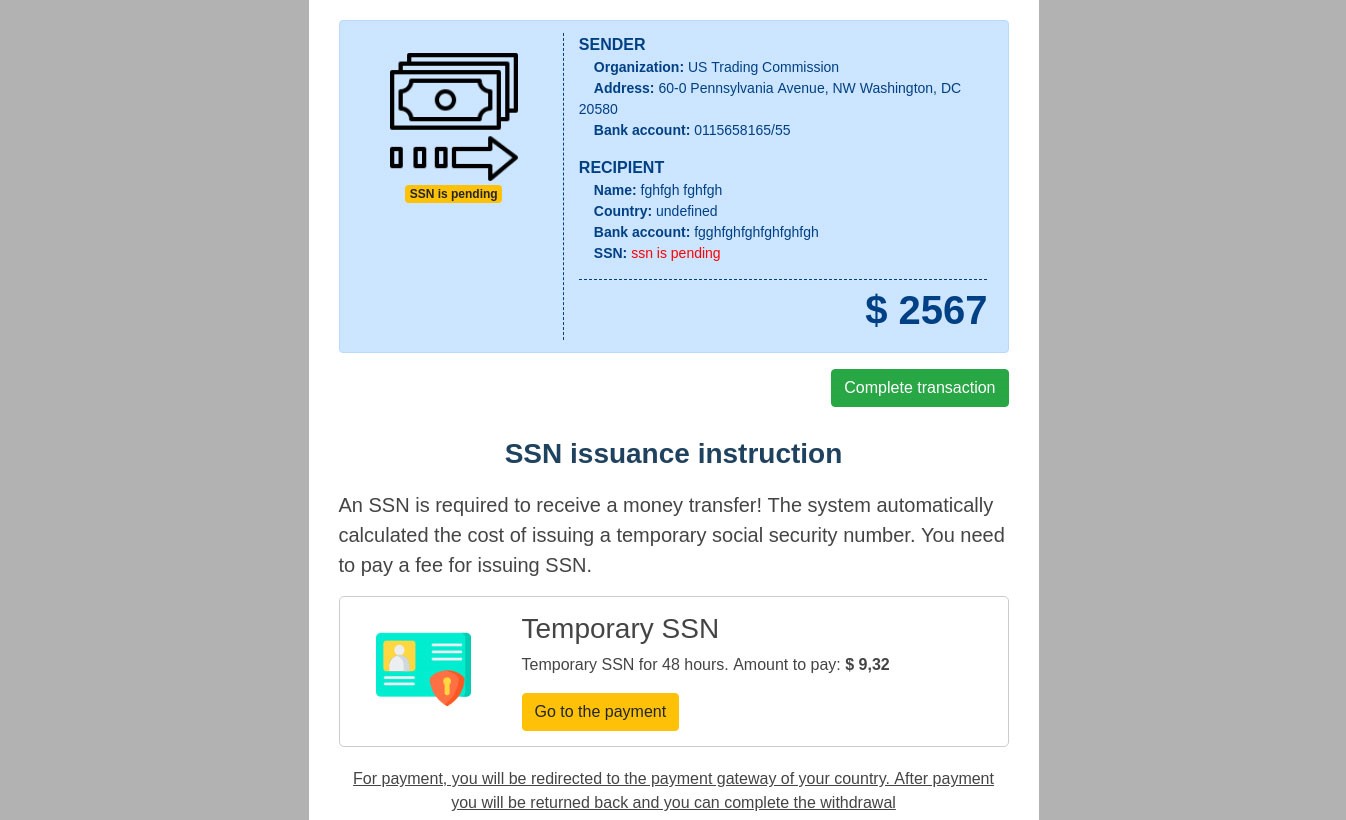

After that, the potential victim was redirected to a payment page with the amount and currency based on the user’s location. For instance, users in Russia were asked to pay in rubles.

The scam deployed the conventional scheme (especially common in the Runet) of asking the victim to pay a small commission or down payment for the promise of something much bigger. In Q1, 14,725,643 attempts to redirect users to such websites were blocked.
Disaster and pandemic
Fires in Australia
The natural disaster that hit the Australian continent was another get-rich opportunity for scammers. For example, one “Nigerian prince”-style e-mail scam reported that a millionaire dying of cancer was ready to donate her money to save the Australian forests. The victim was asked to help withdraw the funds from the dying woman’s account by paying a fee or making a small contribution to pay for the services of a lawyer, for which they would be rewarded handsomely at a later date.
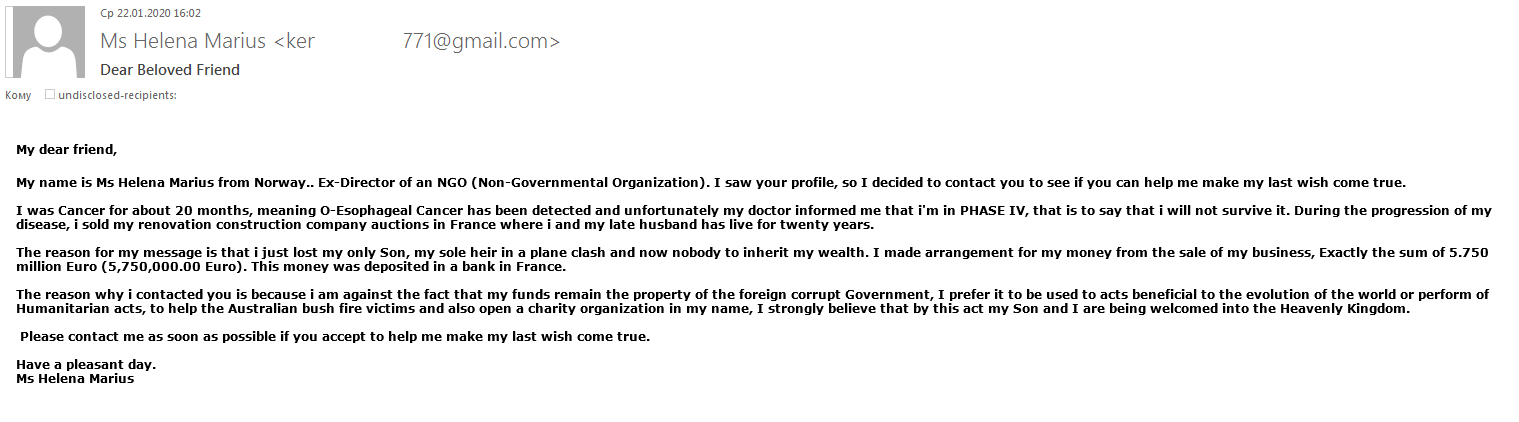

Besides the fictional millionaire, other “nature lovers” were keen to help out — their e-mails were more concise, but the scheme was essentially the same.


COVID-19
“Nigerian prince” scheme
COVID-19 was (and continues to be) a boon to scammers: non-existent philanthropists and dying millionaires are popping up everywhere offering rewards for help to withdraw funds supposedly for humanitarian purpsoses. Some recipients were even invited to help finance the production of a miracle vaccine, or take part in a charity lottery, the proceeds of which, it was said, would be distributed to poor people affected by the pandemic.
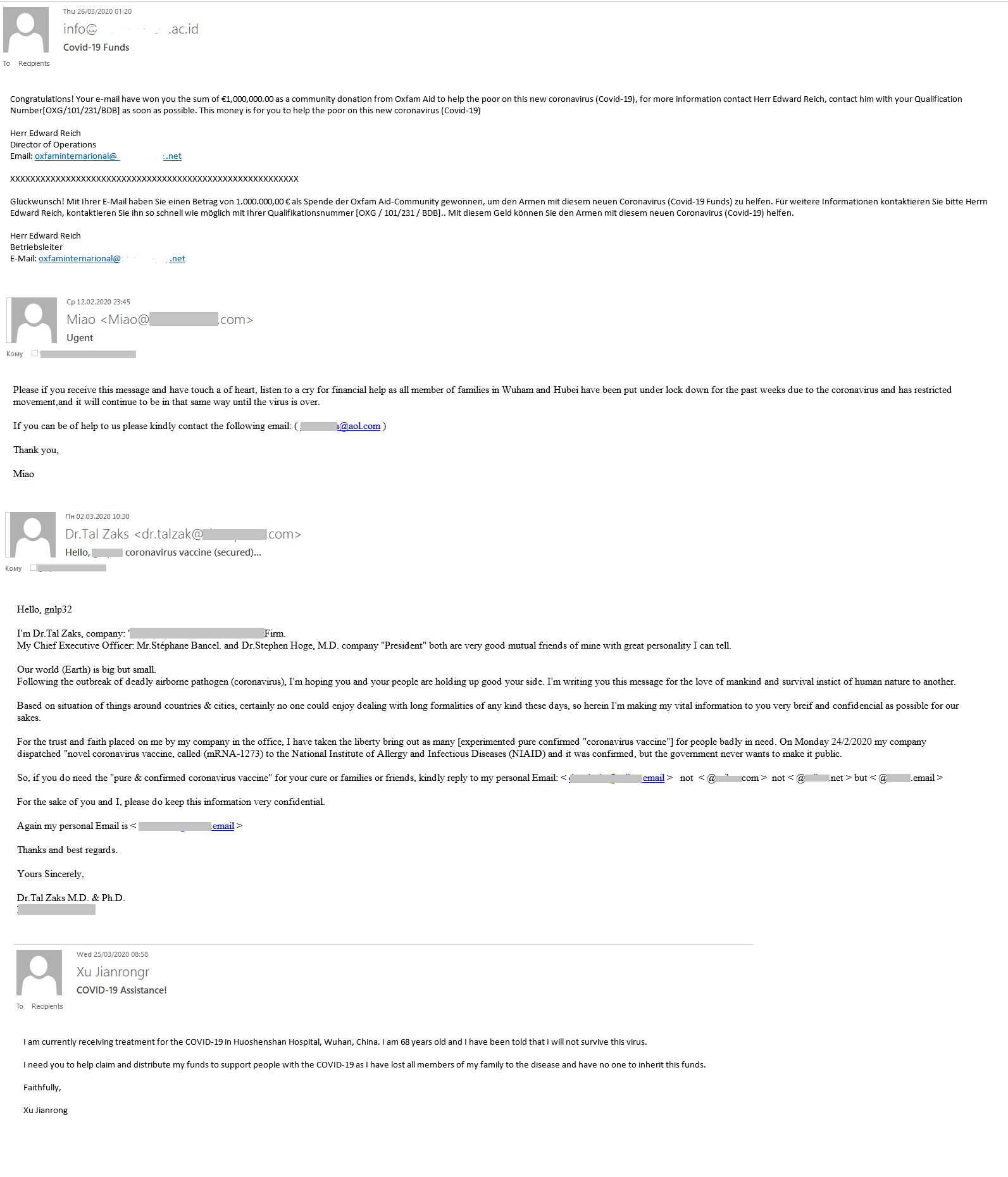

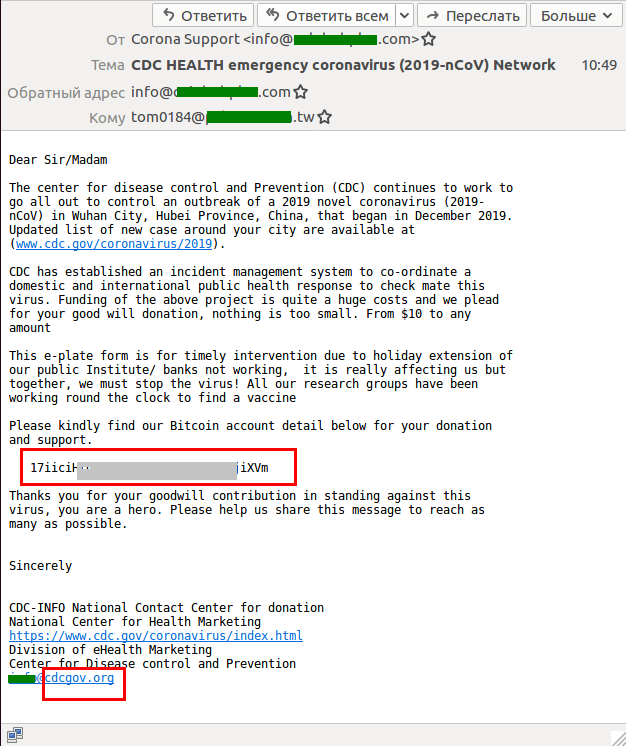
Bitcoin for coronavirus
Having introduced themselves as members of a healthcare organization, the scammers appealed to the victim to transfer a certain sum to the Bitcoin wallet specified in the message. The donation would allegedly go toward fighting the coronavirus outbreak and developing a vaccine, as well as helping victims of the pandemic.

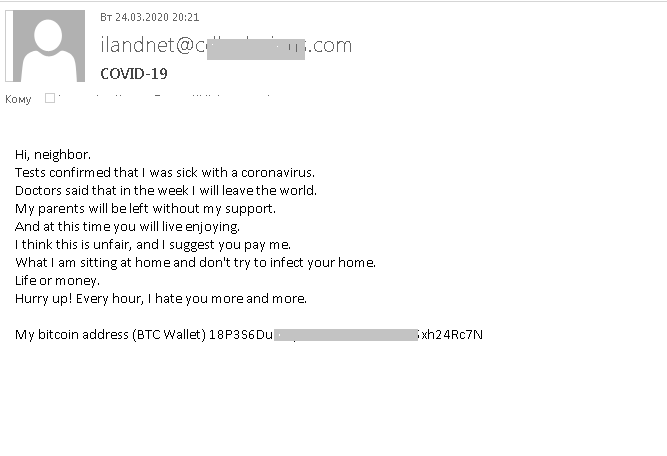
In one e-mail, the attackers played on people’s fear of contracting COVID-19: the message was from an unnamed “neighbor” claiming to be dying from the virus and threatening to infect the recipient unless the latter paid a ransom (which, it was said, would help provide a comfortable old age for the ransomer’s parents).

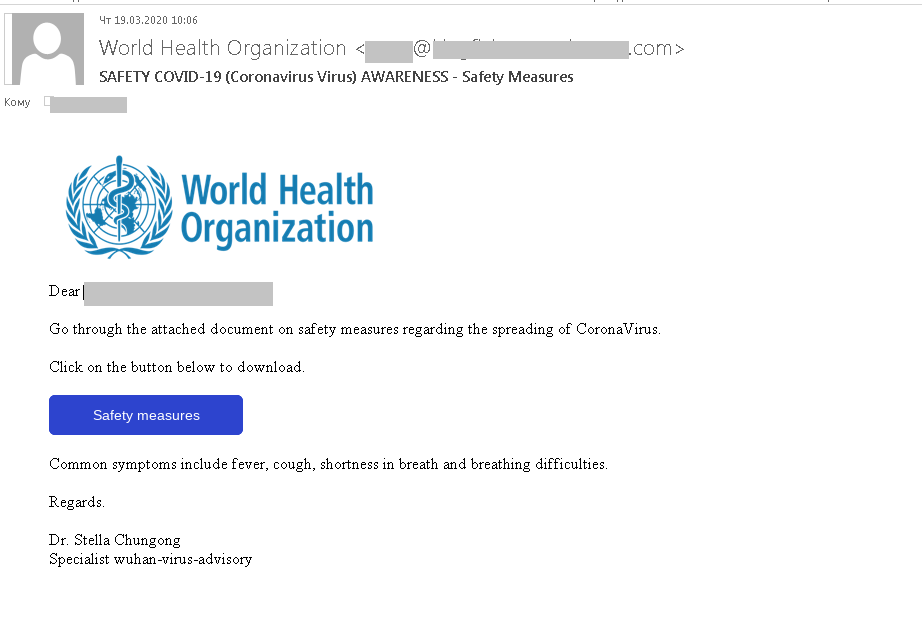
Dangerous advice from the WHO
One fraudulent mailing disguised as a WHO newsletter offered tips about staying safe from COVID-19.

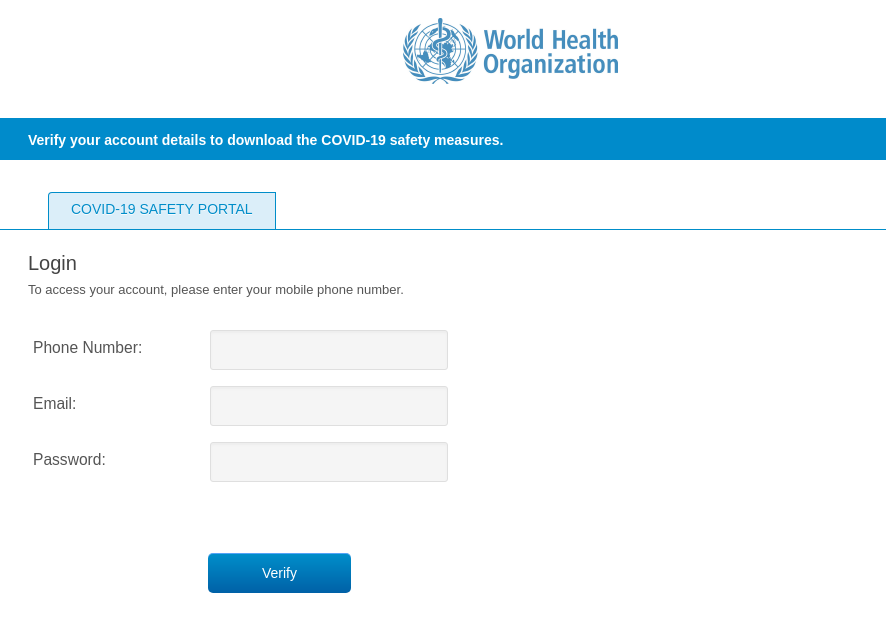
To get the information, the recipient had to click a link pointing to a fake WHO website. The design was so close to the original that only the URL gave away the scam. The cybercriminals were after login credentials for accounts on the official WHO site. Whereas in the first mailings only a username and password were asked for, in later ones a phone number was also requested.

In addition, we detected several e-mails supposedly from the WHO containing documents with malware. The recipient was asked to open the attachment (in DOC or PDF format), which allegedly offered coronavirus prevention advice. For example, this message contained Backdoor.Win32.Androm.tvmf:


There were other, less elaborate mailings with harmful attachments, including ones containing Trojan-Spy.Win32.Noon.gen:

Corporate segment
The coronavirus topic was also exploited in attacks on the corporate sector. For example, COVID-19 was cited in fraudulent e-mails as a reason for delayed shipments or the need to reorder. The authors marked the e-mails as urgent and required to check attached files immediately.

Another mailing prompted recipients to check whether their company was in a list of firms whose activities were suspended due to the pandemic. After which it asked for a form to be filled out, otherwise the company could be shut down. Both the list of companies and the form were allegedly in the archives attached to the message. In actual fact, the attachments contained Trojan-PSW.MSIL.Agensla.a:

We also registered a phishing attack on corporate users. On a fake page, visitors were invited to monitor the coronavirus situation across the world using a special resource, for which the username and password of the victim’s corporate mail account were required.

Government compensation
The introduction of measures to counter the pandemic put many people in a difficult financial situation. Forced downtime in many industries has had a negative impact on financial well-being. In this climate, websites offering compensation from the government pose a particular danger.
One such popular scheme was highlighted by a colleague of ours from Brazil. A WhatsApp messages about financial or food assistance were sent that appeared to come from a supermarket, bank, or government department. To receive the aid, the victim had to fill out the attached form and share the message with a certain number of contacts. After the form was filled out, the data was sent to the cybercriminals, while the victim got redirected to a page with advertising, a phishing site, a site offering a paid SMS subscription, or similar.
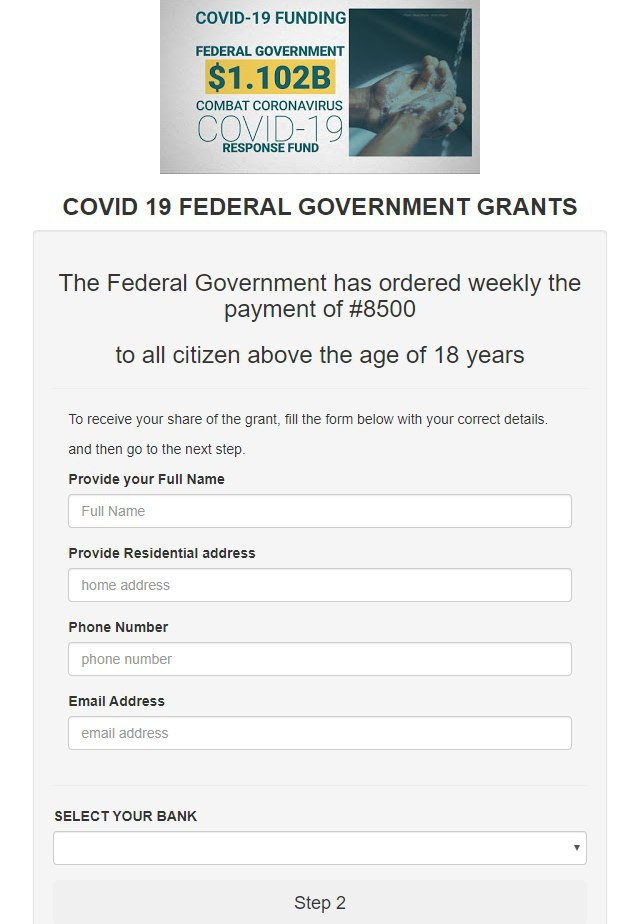



Given that the number of fake sites offering government handouts seems likely only to increase, we urge caution when it comes to promises of compensation or material assistance.
Anti-coronavirus protection with home delivery
Due to the pandemic, demand for antiseptics and antiviral agents has spiked. We registered a large number of mailings with offers to buy antibacterial masks.
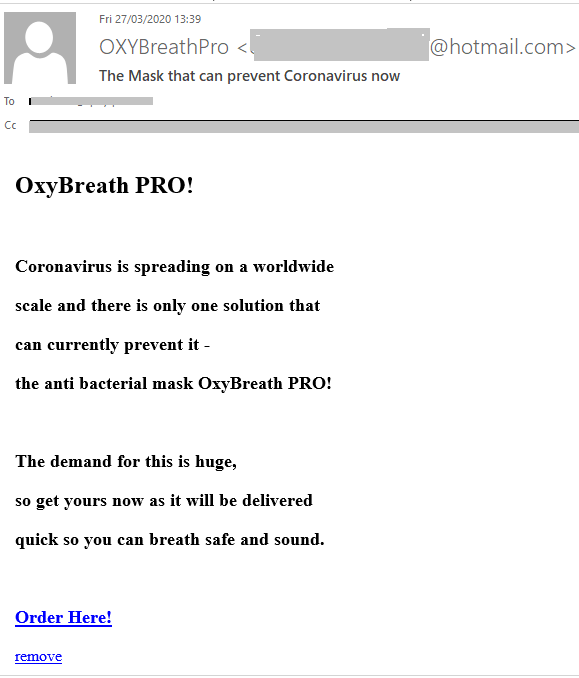

In Latin America, WhatsApp mass messages were used to invite people to take part in a prize draw for hand sanitizer products from the brewing company Ambev. The company has indeed started making antiseptics and hand gel, but exclusively for public hospitals, so the giveaway was evidently the work of fraudsters.


The number of fake sites offering folk remedies for the treatment of coronavirus, drugs to strengthen the immune system, and non-contact thermometers and test kits has also risen sharply. Most of the products on offer have no kind of certification whatsoever.
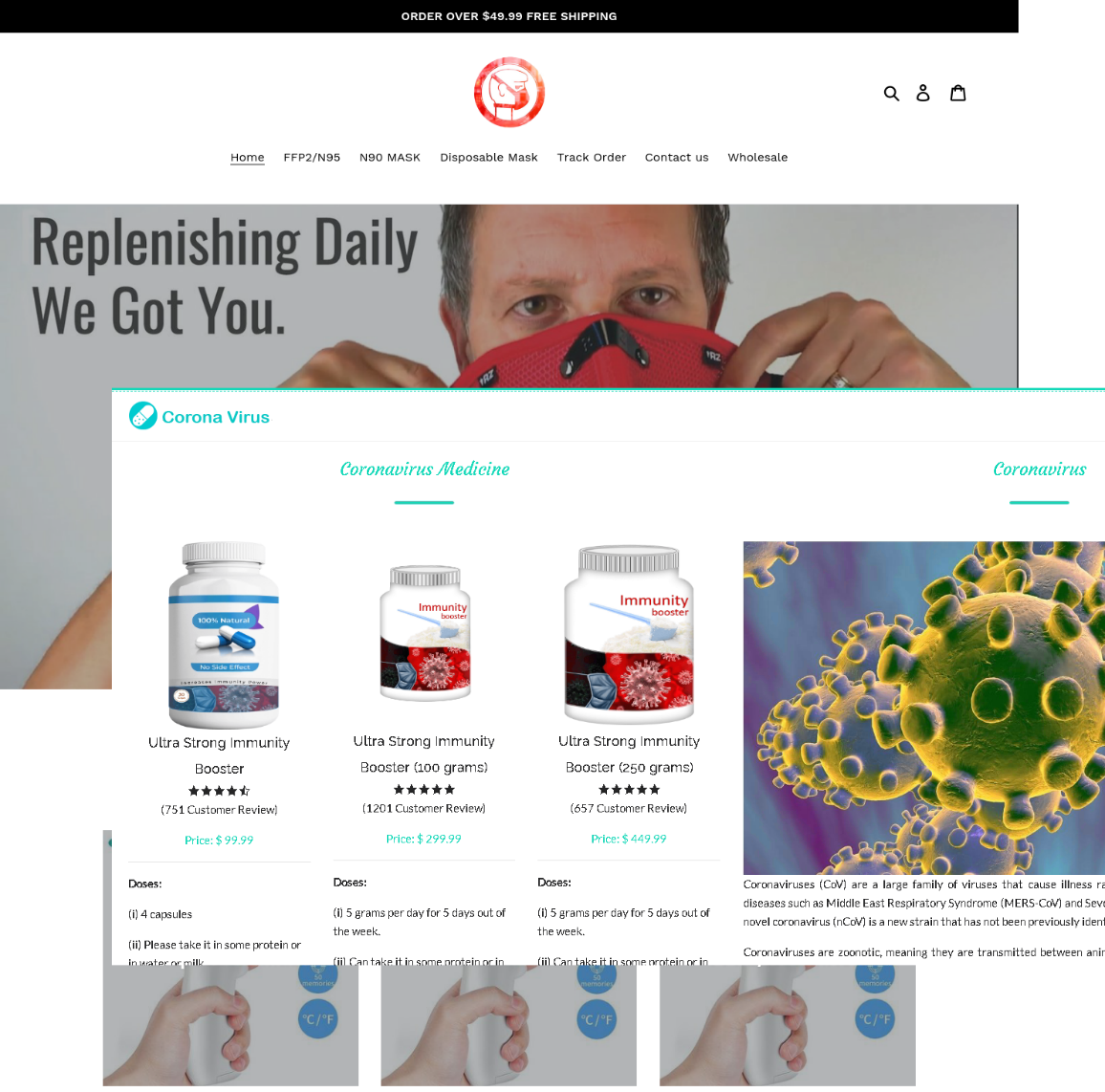

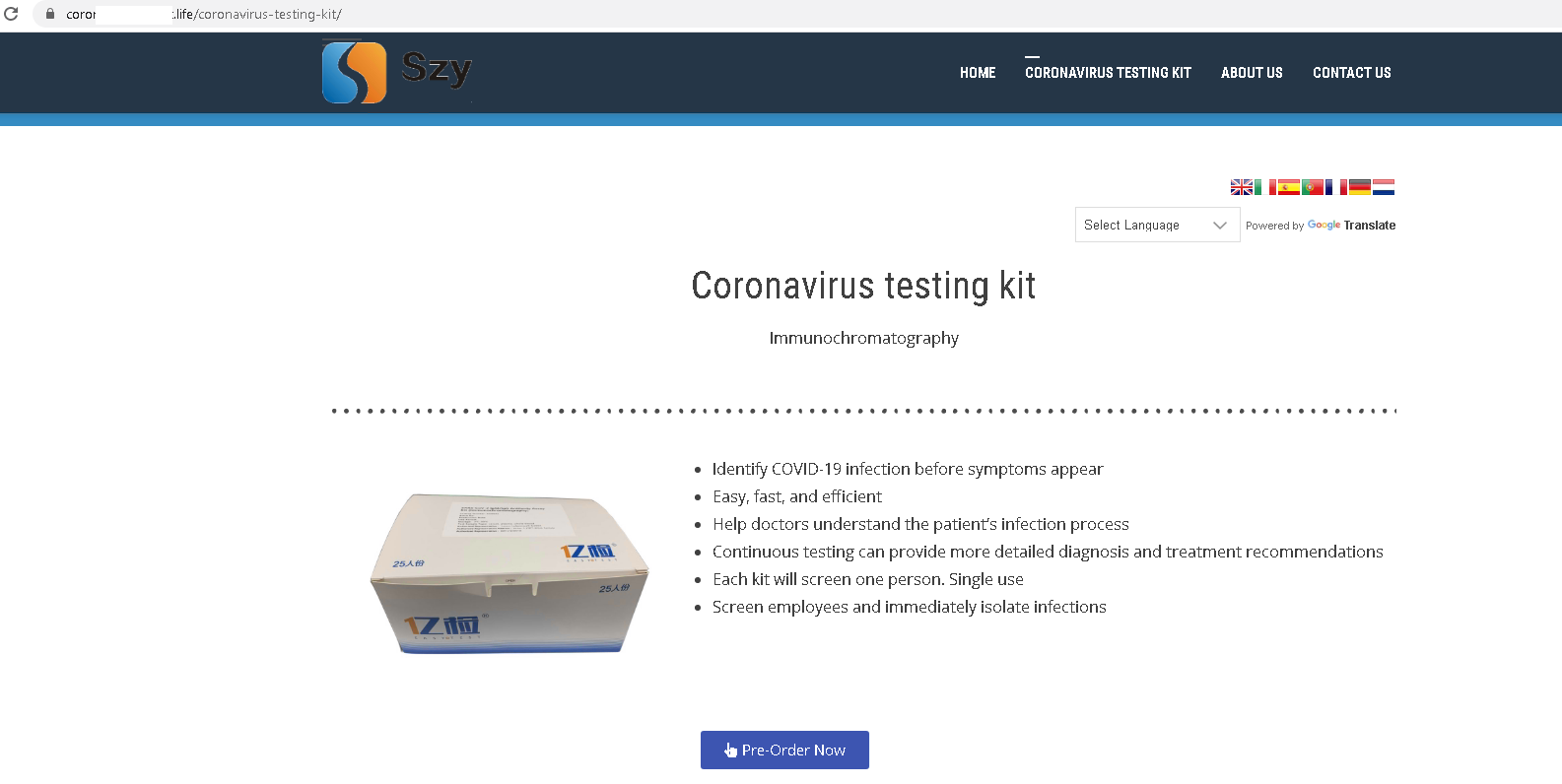

On average, the daily share of e-mails mentioning COVID-19 in Q1 amounted to around 6% of all junk traffic. More than 50% of coronavirus-related spam was in the English language. We anticipate that the number of phishing sites and pandemic-related scams will only increase, and that cybercriminals will use new attack schemes and strategies.
Statistics: spam
Proportion of spam in mail traffic
Proportion of spam in global mail traffic, Q4 2019 – Q1 2020 (download)
In Q1 2020, the largest share of spam was recorded in January (55.76%). The average percentage of spam in global mail traffic was 54.61%, down 1.58 p.p. against the previous reporting period.
Proportion of spam in Runet mail traffic, Q4 2019 – Q1 2020 (download)
In Q1, the share of spam in Runet traffic (the Russian segment of the Internet) likewise peaked in January (52.08%). At the same time, the average indicator, as in Q4 2019, remains slightly lower than the global average (by 3.20 p.p.).
Sources of spam by country
Sources of spam by country, Q1 2020 (download)
In Q1 2020, Russia led the TOP 5 countries by amount of outgoing spam. It accounted for 20.74% of all junk traffic. In second place came the US (9.64%), followed by Germany (9.41%) just 0.23 p.p. behind. Fourth place goes to France (6.29%) and fifth to China (5.22%), which is usually a TOP 3 spam source.
Brazil (3.56%) and the Netherlands (3.38%) took sixth and seventh positions, respectively, followed by Vietnam (2.55%), with Spain (2.34%) and Poland (2.21%) close on its heels in ninth and tenth.
Spam e-mail size
Spam e-mail size, Q4 2019 – Q1 2020 (download)
Compared to Q4 2019, the share of very small e-mails (up to 2 KB) in Q1 2020 fell by more than 6 p.p. and amounted to 59.90%. The proportion of e-mails sized 5-10 KB grew slightly (by 0.72 p.p.) against the previous quarter to 5.56%.
Meanwhile, the share of 10-20 KB e-mails climbed by 3.32 p.p. to 6.36%. The number of large e-mails (100–200 KB) also posted growth (+2.70 p.p.). Their slice in Q1 2020 was 4.50%.
Malicious attachments in e-mail
Number of Mail Anti-Virus triggerings, Q4 2019 – Q1 2020 (download)
In Q1 2020, our security solutions detected a total of 49,562,670 malicious e-mail attachments, which is almost identical to the figure for the last reporting period (there were just 314,862 more malicious attachments detected in Q4 2019).
TOP 10 malicious attachments in mail traffic, Q1 2020 (download)
In Q1, first place in terms of prevalence in mail traffic went to Trojan.Win32.Agentb.gen (12.35%), followed by Exploit.MSOffice.CVE-2017-11882.gen (7.94%) in second and Worm.Win32.WBVB.vam (4.19%) in third.
TOP 10 malicious families in mail traffic, Q1 2020 (download)
As regards malware families, the most widespread this quarter was Trojan.Win32.Agentb (12.51%), with Exploit.MSOffice.CVE-2017-11882 (7.98%), whose members exploit a vulnerability in Microsoft Equation Editor, in second place and Worm.Win32.wbvb (4.65%) in third.
Countries targeted by malicious mailshots
Distribution of Mail Anti-Virus triggerings by country, Q1 2020 (download)
First place by number of Mail Anti-Virus triggerings in Q1 2020 was claimed by Spain. This country accounted for 9.66% of all users of Kaspersky security solutions who encountered e-mail malware worldwide. Second place went to Germany (8.53%), and Russia (6.26%) took bronze.
Statistics: phishing
In Q1 2020, the Anti-Phishing system prevented 119,115,577 attempts to redirect users to scam websites. The percentage of unique attacked users was 8.80% of the total number of users of Kaspersky products in the world.
Attack geography
The country with the largest proportion of users attacked by phishers, not for the first time, was Venezuela (20.53%).
Geography of phishing attacks, Q1 2020 (download)
In second place, by a margin of 5.58 p.p., was Brazil (14.95%), another country that is no stranger to the TOP 3. Next came Australia (13.71%), trailing by just 1.24 p.p.
| Country | %* |
| Venezuela | 20.53% |
| Brazil | 14.95% |
| Australia | 13.71% |
| Portugal | 12.98% |
| Algeria | 12.12% |
| France | 11.71% |
| Honduras | 11.62% |
| Greece | 11.58% |
| Myanmar | 11.54% |
| Tunisia | 11.53% |
* Share of users on whose computers Anti-Phishing was triggered out of all Kaspersky users in the country
Organizations under attack
The rating of attacks by phishers on different categories of organizations is based on detections by Kaspersky products Anti-Phishing component. This component detects pages with phishing content that the user gets redirected to. It does not matter whether the redirect is the result of clicking a link in a phishing e-mail or in a message on a social network, or the result of a malicious program activity. When the component is triggered, a banner is displayed in the browser warning the user about a potential threat.
The largest share of phishing attacks in Q1 2020 fell to the Online Stores category (18.12%). Second place went to Global Internet Portals (16.44%), while Social Networks (13.07%) came in third.
Distribution of organizations affected by phishing attacks by category, Q1 2020 (download)
As for the Banks category, a TOP 3 veteran, this time it placed fourth with 10.95%.
Conclusion
Glancing at the results of Q1 2020, we anticipate that the COVID-19 topic will continue to be actively used by cybercriminals for the foreseeable future. To attract potential victims, the pandemic will be mentioned even on “standard” fake pages and in spam mailings.
The topic is also used extensively in fraudulent schemes offering compensation and material assistance.
It is highly likely that this type of fraud will become more frequent.
The average share of spam in global mail traffic (54.61%) this quarter decreased by 1.58 p.p. against the previous reporting period, while the number of attempted redirects totaled nearly 120 million.
Top of this quarter’s list of spam-source countries is Russia, with a share of 20.74%. Our security solutions blocked 49,562,670 malicious mail attachments, while the most common mail-based malware family, with a 12.35% share of mail traffic, was Trojan.Win32.Agentb.gen.

