Stealthy Kv Botnet Hijacks Soho Routers And Vpn Devices

The Chinese state-sponsored APT hacking group known as Volt Typhoon (Bronze Silhouette) has been linked to a sophisticated botnet named ‘KV-botnet’ it uses since at least 2022 to attack SOHO routers in high-value targets.
Volt Typhoon commonly targets routers, firewalls, and VPN devices to proxy malicious traffic so it blends with legitimate traffic to remain undetected.
A joint report by Microsoft and the US government assesses that the attackers are building infrastructure that can be used to disrupt communications infrastructure in the USA.
“Microsoft assesses with moderate confidence that this Volt Typhoon campaign is pursuing development of capabilities that could disrupt critical communications infrastructure between the United States and Asia region during future crises,” warns Microsoft.
A detailed report published today by the Black Lotus Labs team at Lumen Technologies reveals that a Volt Typhoon campaign has been targeting Netgear ProSAFE firewalls, Cisco RV320s, DrayTek Vigor routers, and, more recently, Axis IP cameras.
“The campaign infects devices at the edge of networks, a segment that has emerged as a soft spot in the defensive array of many enterprises, compounded by the shift to remote work in recent years,” explains Lumen
The covert data transfer network built with the help of KV-botnet was used in attacks targeting telecommunication and internet service providers, a US territorial government entity in Guam, a renewable energy firm in Europe, and US military organizations.
The targeting scope of KV-botnet indicates a focus on espionage and information gathering, although Black Lotus reports that many of the infections appear opportunistic.
The botnet’s activity increased significantly since August 2023 and then again in mid-November 2023. The most recent observed attack dates are December 5, 2023, so the malicious activity is ongoing.
KV-botnet technical details
Black Lotus has identified two activity clusters, separated as ‘KV’ and ‘JDY.’ The former targets high-value entities and is likely operated manually, while the latter engages in broader scanning using less sophisticated techniques.
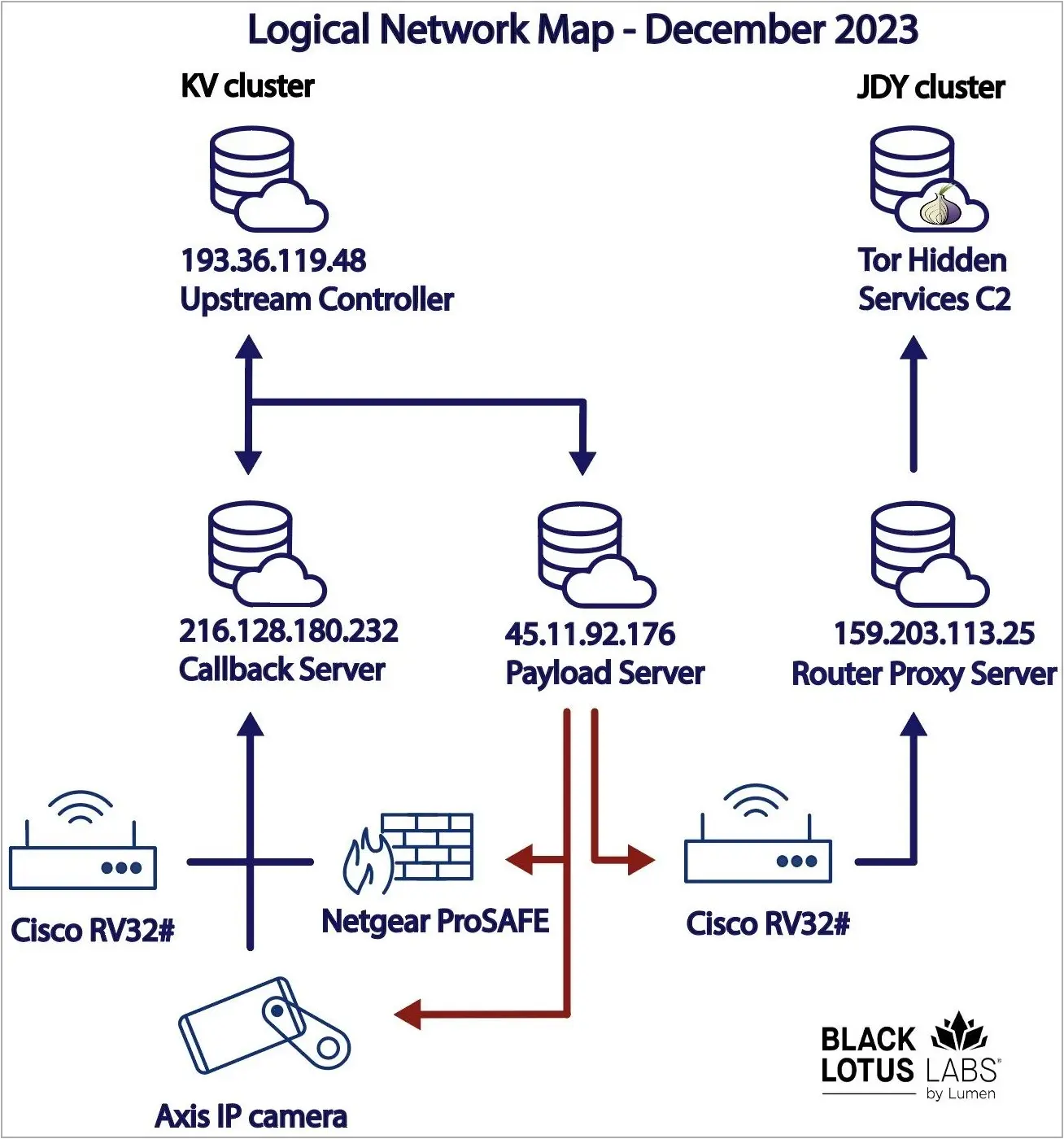
The botnet targets end-of-life devices used by SOHO (small office, home office) entities that don’t maintain a sound security stance. Supported architectures include ARM, MIPS, MIPSEL, x86_64, i686, i486 and i386.
The attacks initially focused on Cisco RV320s, DrayTek Vigor routers, and NETGEAR ProSAFE firewalls, but the malware was later expanded to also target Axis IP cameras like models M1045-LW, M1065-LW, and p1367-E.
Volt Typhoon engages in a complex infection chain that involves multiple files like bash scripts (kv.sh), halting specific processes and removing security tools running on the infected device.
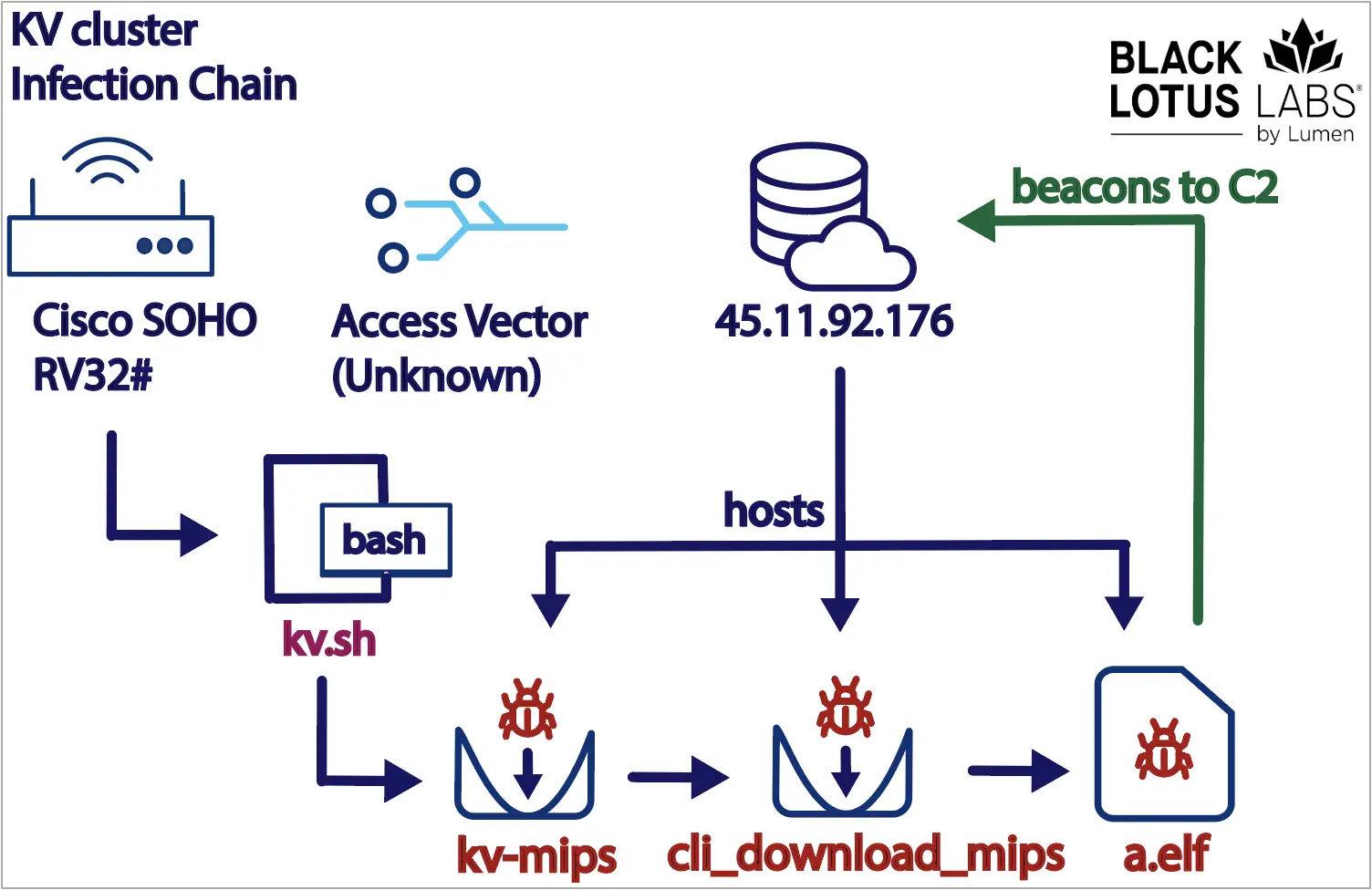
To evade detection, the bot sets up random ports for communication with the C2 (command and control) server and disguises itself by adopting the names of existing processes.
Also, all tooling resides in memory, so the bot is challenging to detect, although this approach impacts its capability to persist on compromised devices.
The commands KV-botnet receives from the C2 concern updating communication settings, exfiltrating host info, performing data transmission, creating network connections, executing host tasks, and others.
“While we did not discover any prebuilt functions in the original binary to enable targeting of the adjacent LAN, there was the ability to spawn a remote shell on the SOHO device,” explains Black Lotus in the report.
“This capability could have been used to either manually run commands or potentially retrieve a yet-to-be-discovered secondary module to target the adjacent LAN.”
Chinese operation
Black Lotus Labs links this botnet to Volt Typhoon after finding overlaps in IP addresses, similar tactics, and working times that align with China Standard Time.
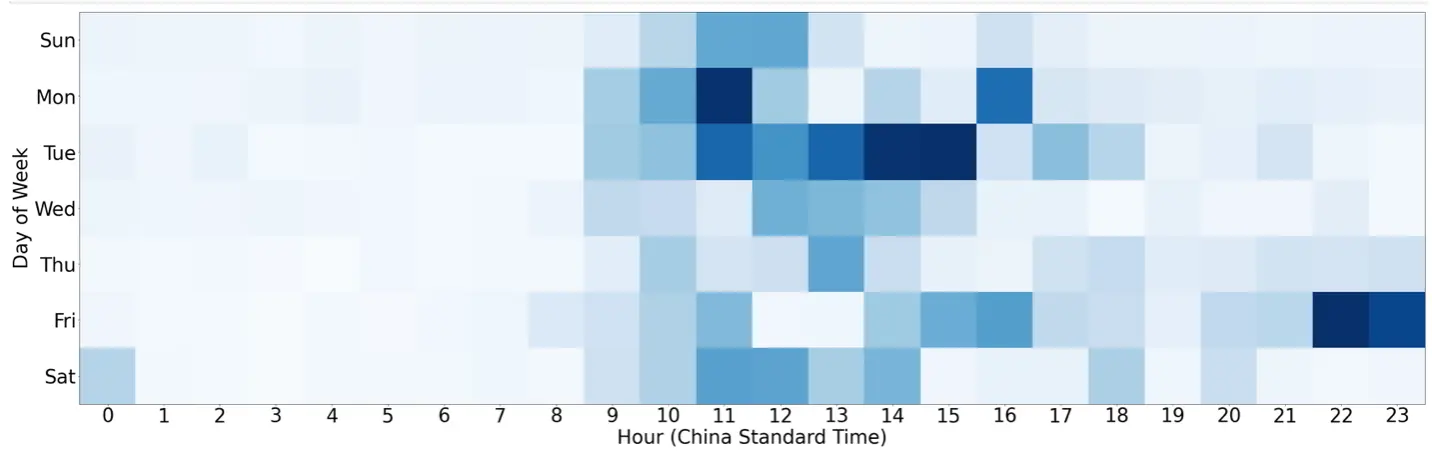
The advanced obfuscation techniques and covert data transfer channels seen in KV-botnet attacks, like employing tunneling layers, overlap with previously documented Volt Typhoon tactics, as do the target selection and interest in specific regions and organization types.
Also, Lumen’s report mentions a suspicious decline in KV-botnet operations that coincided with the public disclosure of Volt Typhoon activities by CISA in May 2023.
Lumen has released indicators of compromise (IOCs) on GitHub, including malware hashes and IP addresses associated with the botnet.
