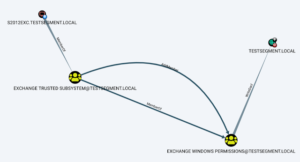
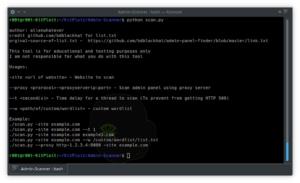
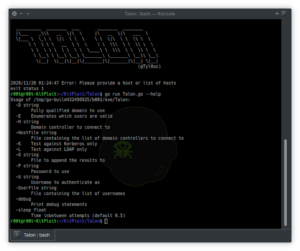
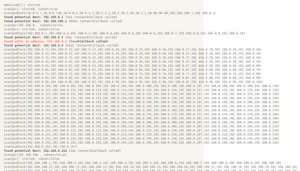
Enum4Linux-Ng – A Next Generation Version Of Enum4Linux (A Windows/Samba Enumeration Tool) With Additional Features Like JSON/YAML Export
enum4linux-ng.py is a rewrite of Mark Lowe's (former Portcullis Labs now Cisco CX Security Labs) enum4linux.pl, a tool for enumerating...