Thousands of Citrix servers vulnerable to patched critical flaws

Thousands of Citrix ADC and Gateway deployments remain vulnerable to two critical-severity security issues that the vendor fixed in recent months.
The first flaw is CVE-2022-27510, fixed on November 8. It’s an authentication bypass that affects both Citrix products. An attacker could exploit it to gain unauthorized access to the device, perform remote desktop takeover, or bypass the login brute force protection.
The second bug is tracked as CVE-2022-27518, disclosed and patched on December 13. It allows unauthenticated attackers to perform remote command execution on vulnerable devices and take control of them.
Threat actors had already been exploiting CVE-2022-27518 when Citrix published a security update to fix it.
Today, researchers at NCC Group’s Fox IT team report that while most public-facing Citrix endpoints have been updated to a safe version, thousands remain vulnerable to attacks.
Finding vulnerable versions
Fox IT analysts scanned the web on November 11, 2022, and found a total of 28,000 Citrix servers online.
To determine how many of the exposed ones are vulnerable to the two flaws, the researchers had to learn their version number, which was not included in the HTTP response from the servers.
Nevertheless, the responses carried MD5 hash-like parameters that could be used for matching them to Citrix ADC and Gateway product versions.
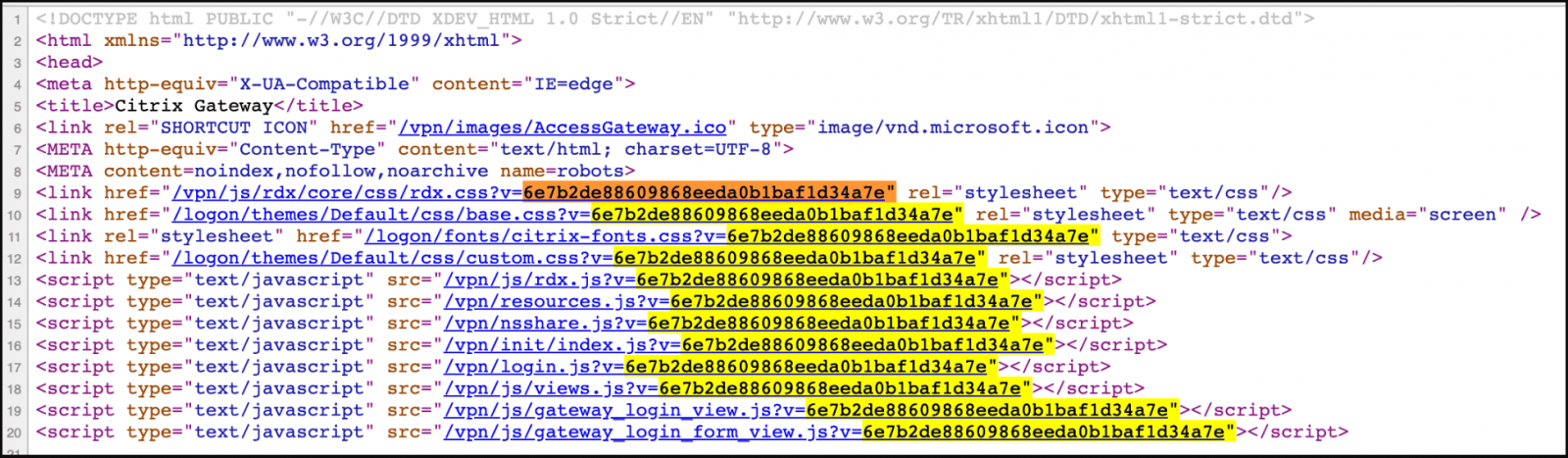

Hence, the team downloaded and deployed all Citrix ADC versions they could source from Citrix, Google Cloud Marketplace, AWS, and Azure on VMs and matched hashes to versions.
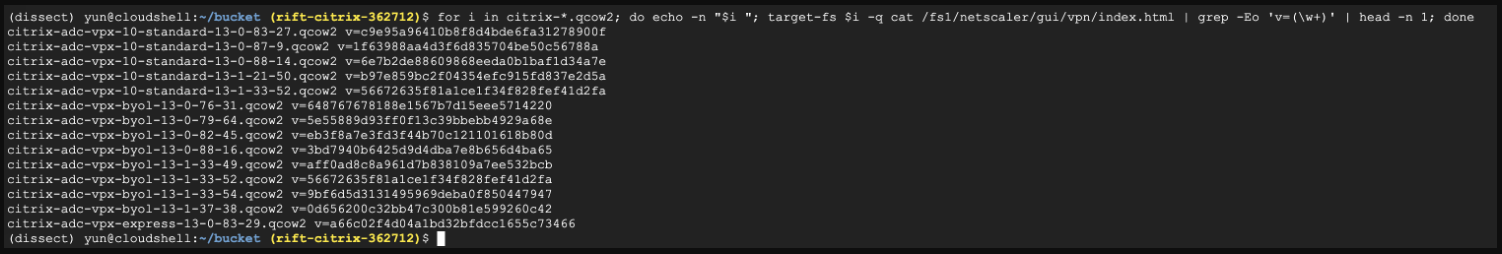

For the hashes that could not be matched with the versions sourced, the researchers resorted to figuring out the build date and deducing their version number based on that.
This further reduced the number of unknown versions (orphan hashes), but in general, most hashes had been coupled to specific product versions.
Thousands of vulnerable Citrix servers
The final results are summarized in the following graph, indicating that as of December 28, 2022, the majority is on version 13.0-88.14, which is unaffected by the two security issues.
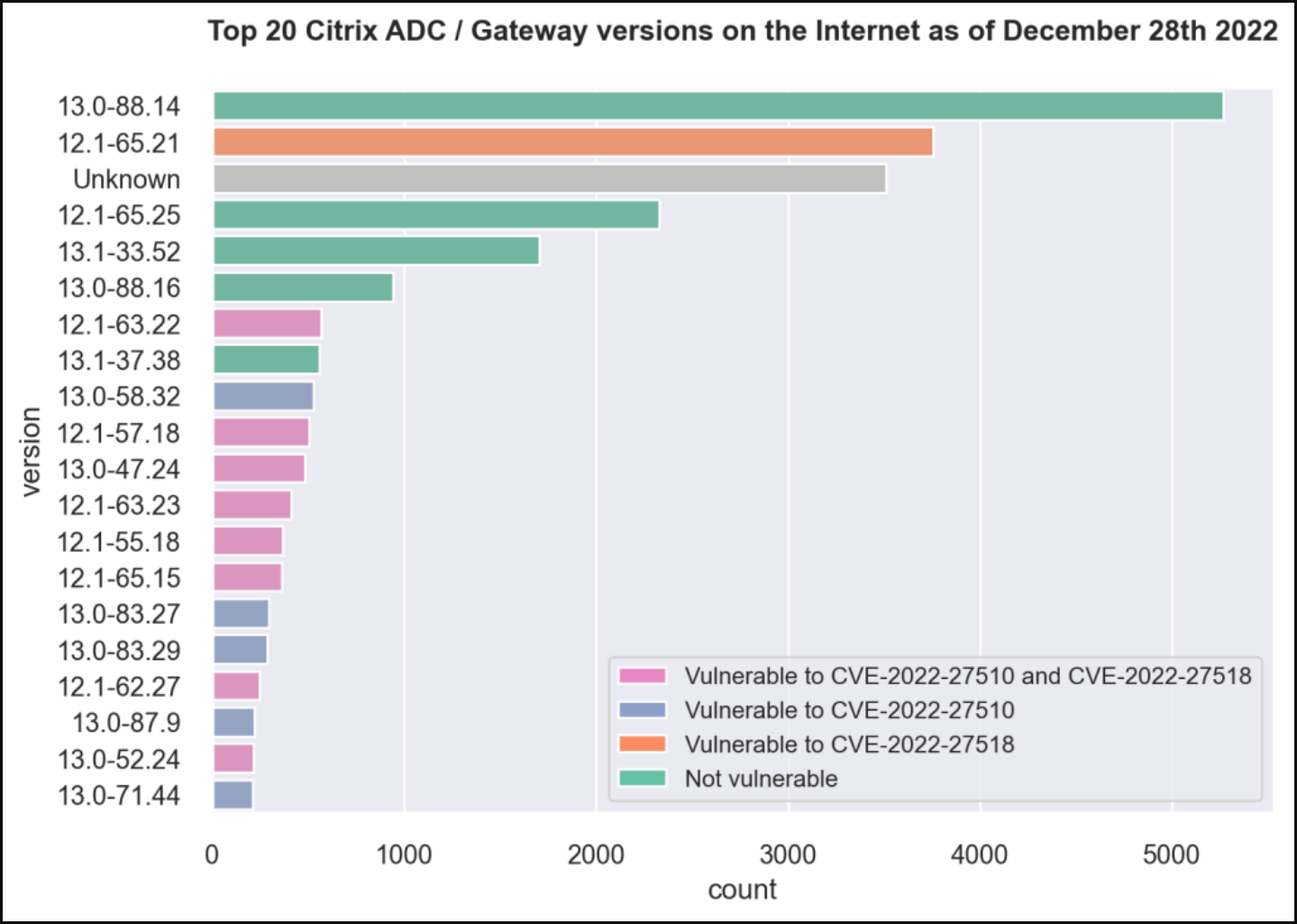
The second most popular version was 12.1-65.21, vulnerable to CVE-2022-27518 if certain conditions are met, was running on 3,500 endpoints.
The requirements for these machines to be exploitable ask for the use of SAML SP or IdP configurations, meaning that not all 3,500 systems were vulnerable to CVE-2022-27518.
Then there are over 1,000 servers vulnerable to CVE-2022-27510 and approximately 3,000 endpoints potentially vulnerable to both critical bugs.
The detections that return hashes with unknown Citrix version numbers come in third place, counting over 3,500 servers, which may or may not be vulnerable to either flaw.
Regarding the patching speed, the United States, Germany, Canada, Australia, and Switzerland responded quickly to the publication of the relevant security advisories.
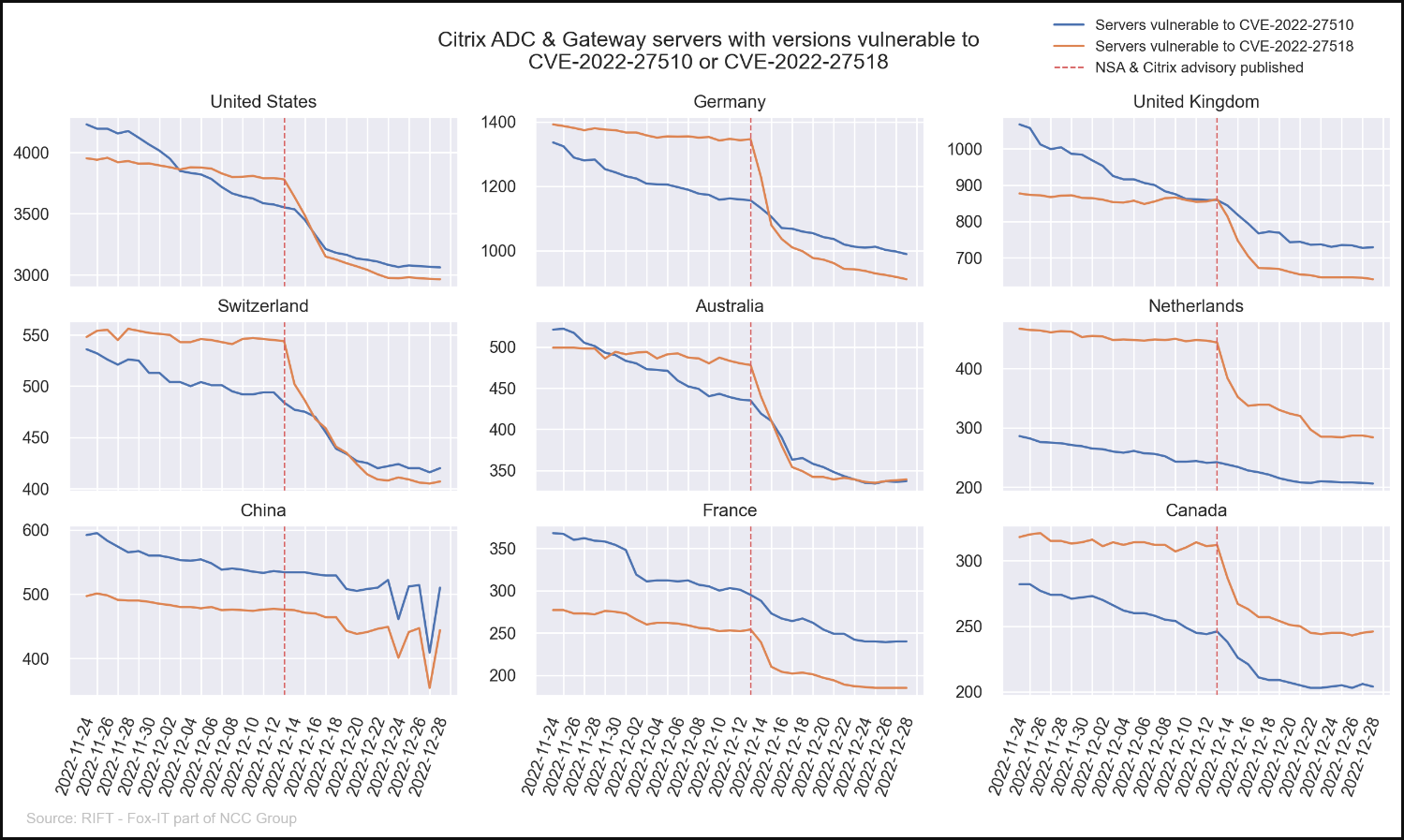
The Fox IT team hopes its blog will help raise awareness on Citrix administrators who are yet to apply the security updates for the recent critical flaws, with the statistics highlighting there’s still much work that remains to be done to close all security gaps.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below
To keep up to date follow us on the below channels.







![Black Basta Ransomware Victim: lactanet[.]ca 17 Basta](https://www.redpacketsecurity.com/wp-content/uploads/2022/06/Basta-300x97.png)