Update now! Multiple vulnerabilities patched in Google Chrome
Google has announced an update for the Chrome browser that includes 32 security fixes. The severity rating for one of the patched vulnerabilities is Critical.
The stable channel was promoted to 102.0.5005.61/62/63 for Windows, and 102.0.5005.61 for Mac and Linux.
Critical
Google rates vulnerabilities as critical if they allow an attacker to run arbitrary code on the underlying platform with the user’s privileges in the normal course of browsing.
Publicly disclosed computer security flaws are listed in the Common Vulnerabilities and Exposures (CVE) database. Its goal is to make it easier to share data across separate vulnerability capabilities (tools, databases, and services).
This update patches the critical vulnerability listed as CVE-2022-1853: Use after free in Indexed DB.
Use after free (UAF) is a vulnerability due to incorrect use of dynamic memory during a program’s operation. If after freeing a memory location a program does not clear the pointer to that memory, an attacker can use the error to manipulate the program.
IndexedDB is a low-level Application Programming Interface (API) for client-side storage of significant amounts of structured data, including files. This API uses indexes to enable high performance searches of this data. While Document Object Model (DOM) Storage is useful for storing smaller amounts of data, IndexedDB provides a solution for storing larger amounts of structured data.
Each IndexedDB database is unique to an origin (typically, this is the site domain or subdomain), meaning it should not be accessible by any other origin.
Google does not disclose details about vulnerabilities until users have had ample opportunity to install the patches, so I could be reading this wrong. But my guess is that an attacker could construct a specially crafted website and take over the visitor’s browser by manipulating the IndexedDB.
Other vulnerabilities
Of the remaining 31 vulnerabilities, Google has rated 12 as High. High severity vulnerabilities allow an attacker to execute code in the context of, or otherwise impersonate, other origins.
Another 13 vulnerabilities were rated as Medium. Medium severity bugs allow attackers to read or modify limited amounts of information, or which are not harmful on their own but potentially harmful when combined with other bugs.
Which leaves six vulnerabilities that were rated as Low. Low severity vulnerabilities are usually bugs that would normally be a higher severity, but which have extreme mitigating factors or a highly limited scope.
How to update
If you’re a Chrome user on Windows, Mac, or Linux, you should update to version 101.0.4951.41 as soon as possible.
The easiest way to update Chrome is to allow it to update automatically, which uses the same method as outlined below but doesn’t need you to do anything. But you can end up blocking automatic updates if you never close the browser, or if something goes wrong, such as an extension stopping you from updating the browser.
So, it doesn’t hurt to check now and then. And now would be a good time, given the severity of the vulnerabilities listed.
My preferred method is to have Chrome open the page chrome://settings/help which you can also find by clicking Settings > About Chrome.
If there is an update available, Chrome will notify you and start downloading it. Then all you have to do is relaunch the browser in order for the update to complete.
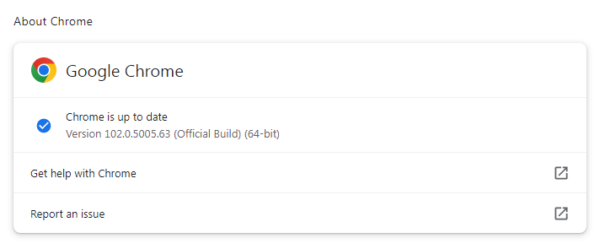
You should then see the message, “Chrome is up to date”.
Affected systems:
- Google Chrome for Windows versions prior to 102.0.5005.61/62/63
- Google Chrome for Mac and Linux versions prior to 102.0.5005.61
Stay safe, everyone!
The post Update now! Multiple vulnerabilities patched in Google Chrome appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![Black Basta Ransomware Victim: bdcm[.]com 4 Basta](https://www.redpacketsecurity.com/wp-content/uploads/2022/06/Basta-300x97.png)

