Vmware Prevents Some Perpetual License Holders From Downloading Patches
Exclusive Some customers of Broadcom’s VMware business currently cannot access security patches, putting them at greater risk of attack.
Customers in that perilous position hold perpetual licenses for VMware products but do not have a current support contract with Broadcom, which will not renew those contracts unless users sign up for software subscriptions. Yet many customers in this situation run products that Broadcom continues to support with patches and updates.
In April 2024, Broadcom CEO Hock Tan promised “free access to zero-day security patches for supported versions of vSphere” so customers “are able to use perpetual licenses in a safe and secure fashion.”
VMware patches aren’t freely available; users must log on to Broadcom’s support portal to access the software.
Some VMware users in this situation have told The Register that when they enter the portal they cannot download patches, and that VMware support staff have told them it may be 90 days before the software fixes become available.
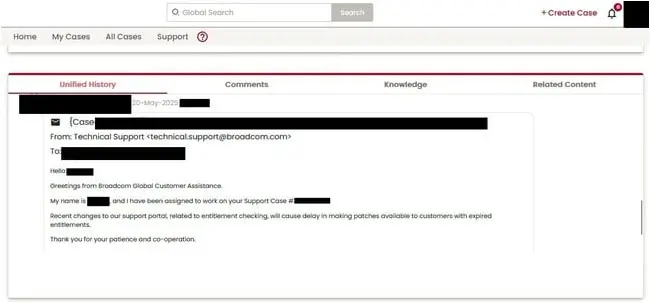
One VMware customer shared the following screenshot:
A VMware spokesperson confirmed that some customers cannot currently access patches:
“Because our support portal requires validation of customer entitlements for software patches, only entitled customers have access to the patches at this time,” the spokesperson explained.
That confirms the comment in screenshot above, in which a Broadcom support staffer wrote, “Recent changes to our support portal, related to entitlement checking, will cause delay in making patches available to customers with expired entitlements.”
The VMware spokesperson told us, “A separate patch delivery cycle will also be available for non-entitled customers and will follow at a later date.”
The spokesperson did not detail that later date. And as the screenshot above shows, users haven’t had access to patches since late May.
This is obviously a sub-optimal situation, as attackers are known to target VMware implementations.
VMware has published eleven security advisories in 2025, including last week’s warning of critical-rated flaws which allow an attacker with administrative privileges on a virtual machine to execute code on a host machine. That’s just about the worst thing that can happen in a virtualized environment.
As revealed by The Register last month, a Dutch court ordered Broadcom’s VMware subsidiary to continue providing software support for at least two years to Rijkswaterstaat (RWS), the exec arm of the Ministry of Infrastructure and Water Management in the Netherlands.
RWS was using VMware’s server virtualization for more than 15 years under a perpetual license, and declined to purchase a subscription licensing agreement that it claimed would cost 85 percent more to continue using the same software and receiving support.
We previously asked VMware to comment on this legal tussle but it didn’t respond. ®
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.


![[QILIN] - Ransomware Victim: IREM companies 2 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)