Wazuh Building Robust Cybersecurity Architecture With Open Source Tools
Cybersecurity architecture refers to the design and structure of an organization’s approach to securing its information systems. It outlines the components, policies, technologies, and processes to protect digital assets.
The primary objective of a cybersecurity architecture is to establish a robust, resilient, and well-integrated defense against a wide range of cyber threats.
Building a cybersecurity architecture requires organizations to leverage several security tools to provide multi-layer security in an ever-changing threat landscape. However, the cost required to implement these security solutions could be enormous for small and medium enterprises (SMEs).
Leveraging open source tools and solutions to build a cybersecurity architecture offers organizations several advantages, such as cost-effectiveness, flexibility, community support, and transparency.
Open source solutions allow organizations to customize and adapt their cybersecurity infrastructure to specific needs while benefiting from the collective expertise of the global open source community.
Security design implementation
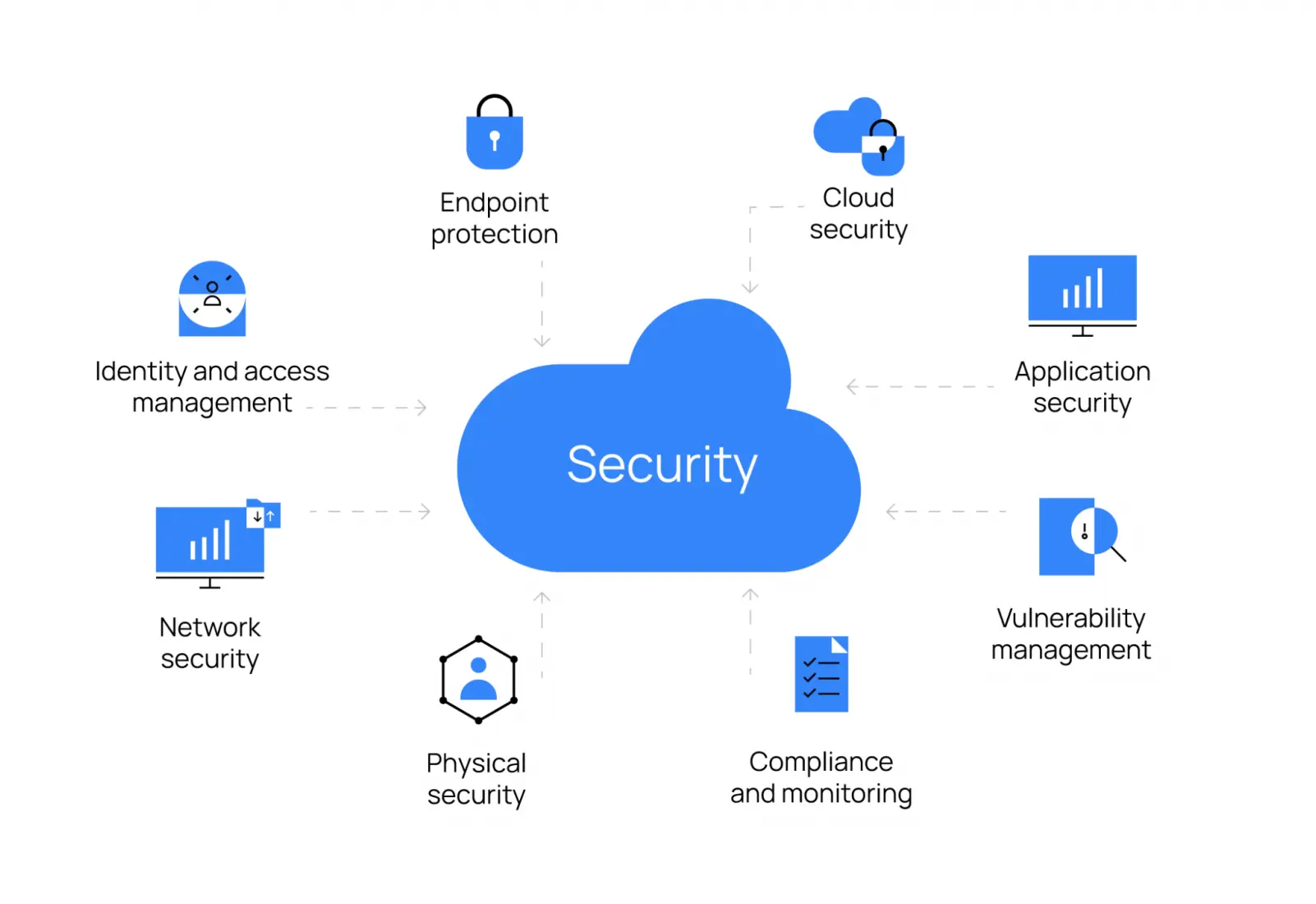
Safeguarding an organization’s digital assets requires the implementation of policies, processes, controls, and technology, with technology playing a vital role. Some key areas to consider when implementing a security architecture include:
- Endpoint protection
- Cloud security
- Network security
- Application security
- Identity and access management
- Monitoring and compliance
- Vulnerability management
- Physical security.
Organizations require various security tools that satisfy the key areas of a security architecture as they each play a role in securing digital assets.
For example, an anti-virus solution for endpoint security, web application firewall for application security, network firewall for network security, and SIEM solution for monitoring and compliance.
Leveraging open source tools in cybersecurity

Open Source Software (OSS) is software that is distributed with its source code available for use and modification while retaining its original rights. It is shared openly, enabling anyone to access the repository for independent code use or to contribute to the project’s design and functionality.
OSS is often designed with interoperability in mind. It promotes the sharing of improvements and innovations within the community of developers, contributors, and users who collaborate to improve the software.
This approach leads to rapid development, bug fixes, and enhancements of OSS.
There are many open source security projects on the internet. Leveraging these open source projects can help organizations reduce the cost of implementing security solutions as it eliminates paying licensing fees associated with proprietary solutions. This cost savings can be significant for organizations, especially those with budget constraints.
Some open source security tools and their functions
Building a cybersecurity architecture using open source software requires a strategic approach to selecting security tools that align with the roles and requirements of each component within the security framework. Below are examples of some open source tools that can fulfill these roles in a cybersecurity architecture.
- Wazuh (SIEM and XDR): It is a free and open source security platform that provides unified SIEM and XDR protection. It protects workloads across on-premises, virtualized, containerized, and cloud-based environments. Wazuh collects event data from various sources, including endpoints, network devices, cloud workloads, and applications. It analyzes telemetry in real time for threat detection, prevention, and compliance. The security agents have an anomaly and malware detection module that detects abnormal and malicious events on endpoints. Wazuh provides out-of-the-box support for compliance frameworks like PCI DSS, HIPAA, GDPR, NIST SP 800-53, and TSC.
- ClamAV (Clam AntiVirus): It is an open source antivirus engine designed for detecting various kinds of malicious software, including viruses, malware, and spyware. It is primarily used on Unix-like operating systems, but it also supports the Windows operating system. One of the notable features of ClamAV is its simplicity and resource efficiency, making it suitable for servers and systems where resource usage is important. It’s often used in email gateways and file servers to scan incoming and outgoing data for potential threats.
- Suricata: is an open source Network IDS (Intrusion Detection System), IPS (Intrusion Prevention System), and Network Security Monitoring (NSM) engine. It is designed to monitor network traffic and detect suspicious or malicious activity. Integrating Suricata with other security tools and components can be instrumental in crafting a comprehensive network security strategy.
- pfSense: is an open source firewall and routing software distribution based on FreeBSD, an open source Unix-like operating system. It is designed to be installed on standard PC hardware to provide a dedicated, feature-rich firewall and router solution. pfSense also offers a web-based interface for configuration and management.
- ModSecurity: is a widely used tool in web application security, providing an additional layer of defense against a range of web-based attacks. It is often part of a comprehensive security strategy that includes secure coding practices, regular security audits, and other security measures to protect web applications from evolving threats. It operates as an Apache or Nginx module, allowing it to integrate seamlessly with these popular web servers.
- VeraCrypt: is a free and open source disk encryption software that provides on-the-fly encryption. It allows users to create encrypted volumes or containers on storage devices. It includes features such as keyfile support, password strengthening, and the ability to use pre-boot authentication to secure the system before the operating system loads. VeraCrypt is available for Windows, macOS, and Linux.
- OpenDLP (Open Data Loss Prevention): is an open source data loss prevention solution designed to help organizations identify and protect sensitive data. OpenDLP assists in discovering sensitive data within an organization’s network. It scans endpoints, servers, and other networked devices to identify and classify data based on predefined policies. OpenDLP offers organizations the flexibility to define policies specifying what constitutes sensitive data and how it should be handled.
- OpenVAS (Open Vulnerability Assessment System): is an open source vulnerability scanning and management tool. It is used to detect security vulnerabilities in systems and networks, providing a way for organizations to assess and improve their overall security posture. OpenVAS performs automated scans for a wide range of vulnerabilities and generates detailed reports that highlight discovered vulnerabilities, their severity levels, and recommendations for remediation.
Taking it a step further with Wazuh

Wazuh is a security solution that offers unified SIEM and XDR protection across several platforms.
The article Wazuh – The free and open source XDR platform highlights how organizations can take advantage of the open nature of Wazuh to use and customize it based on their security needs freely.
It protects workloads across virtualized, on-premises, cloud-based, and containerized environments. Wazuh provides organizations with an effective approach to cybersecurity.
By collecting data from multiple sources and correlating it in real-time, it offers a broader view of an organization’s security posture.
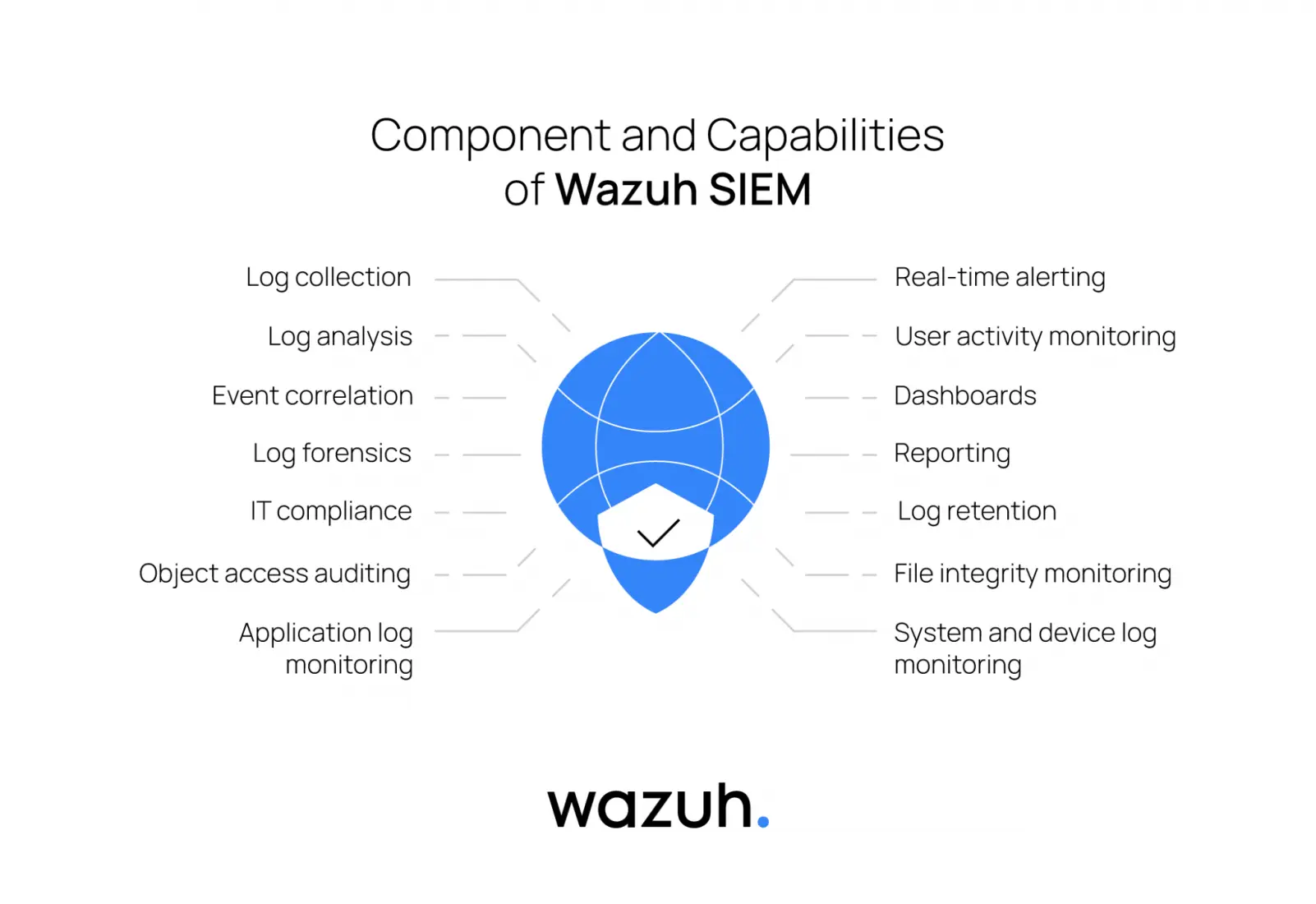
Wazuh plays a significant role in the open source community. By providing a platform for security information and event management, log analysis, intrusion detection, vulnerability detection, active response, file integrity monitoring, compliance monitoring, and more.
It provides flexibility and interoperability, enabling organizations to deploy agents across diverse operating systems seamlessly. This allows for centralized management and analysis of security events, with integration into other security tools and solutions augmenting its overall capabilities.
By enriching raw data with contextual information, security analysts can gain a better understanding of the nature and severity of threats.
Wazuh has over 20 million annual downloads and extensively supports users through a constantly growing open source community. Wazuh open source SIEM and XDR is designed to provide security analysts with features required to detect, prevent, and respond to threats as they occur.
For more information, check out the Wazuh documentation to learn about the various capabilities Wazuh offers.
Sponsored and written by Wazuh.
