Winning the Mind Game: The Role of the Ransomware Negotiator
Get exclusive insights from a real ransomware negotiator who shares authentic stories from network hostage situations and how he managed them.
The Ransomware Industry#
Ransomware is an industry. As such, it has its own business logic: organizations pay money, in crypto-currency, in order to regain control over their systems and data.
This industry’s landscape is made up of approximately 10-20 core threat actors who originally developed the ransomware’s malware. To distribute the malware, they work with affiliates and distributors who utilize widespread phishing attacks to breach organizations. Profits are distributed with approximately 70% allocated to the affiliates and 10%-30% to these developers. The use of phishing renders online-based industries, like gaming, finance and insurance, especially vulnerable.
In addition to its financial motivations, the ransomware industry is also influenced by geo-political politics. For example, in June 2021, following the ransomware attacks on the Colonial Pipeline and JBS, the Byden administration announced that ransomware was a threat to National Security. The administration then listed critical infrastructures that were “off limits” to attackers.
Following these steps, a number of threat actors decided to change course: declaring they would not attack essential and fundamental organizations like hospitals, power plants and educational institutions. A few months later, the FBI reported they had attacked prominent ransomware group REvil:
The attack garnered a response from the Conti group, which reflected their ideological motives:
Ransomware Vaccinations#
Managing a ransomware event is similar to managing a hostage situation. Therefore, to prepare for a ransomware incident, it is recommended for organizations to employ a similar crisis management structure. This structure is based on the following functions:
1. A crisis manager: #
- Coordinates the technological, business and legal tracks.
- The technological track includes forensic, investigation, containment, remediation and recovery, as well as professional dialogue. At this stage, the organization and the incident response teams assess the scope of the event. For example, how deep the attackers are in the system, how much data was exfiltrated, etc.
- The business track covers business continuity plans and media and PR. These are usually executed once the scope of the event is clear. It is recommended to be as transparent and accurate as possible when issuing public statements.
- The legal track includes legal, regulatory and compliance considerations. They track what guidelines need to be complied and in which time frames. Sometimes, they will also be the crisis managers.
- The crisis manager cannot be the decision-maker.
2. A decision making group:#
- The group or person that makes informed decisions based on the data from the crisis manager.
3. Law enforcement:#
- It is recommended to define this relationship in advance. The extent could be as minimal as just informing them and as deep as allowing them to manage the entire crisis.
4. Insurance:#
According to Etay Maor, Senior Director Security Strategy at Cato Networks, “We’re seeing more and more companies offering bundles of these ransomware services. However, it is recommended to separate these roles to ensure the most professional response.”
The Role of the Professional Negotiator#
Professional negotiation is the act of taking advantage of the professional communication with the hacker in various extortion situations. The role comprises four key elements:
1. Identifying the scope of the event – Takes place within the first 24-48 hours. Includes understanding what was compromised, how deep the attackers are in the system, whether the act is a single, double or triple ransomware, if the attack was financially motivated or if it was a political or personal attack, etc.In 90% of cases, the attack is financially motivated. If it is politically motivated, the information may not be recovered, even after paying the ransom.
2. Profiling the threat actor – Includes understanding whether the group is known or unknown, their behavioral patterns and their organizational structure. Understanding who the attacker is influences communication.For example, by finding out what the local time is for the attacker, the negotiator can identify where they came from. This can be used for improving negotiation terms, like leveraging public holidays to ask for a discount.
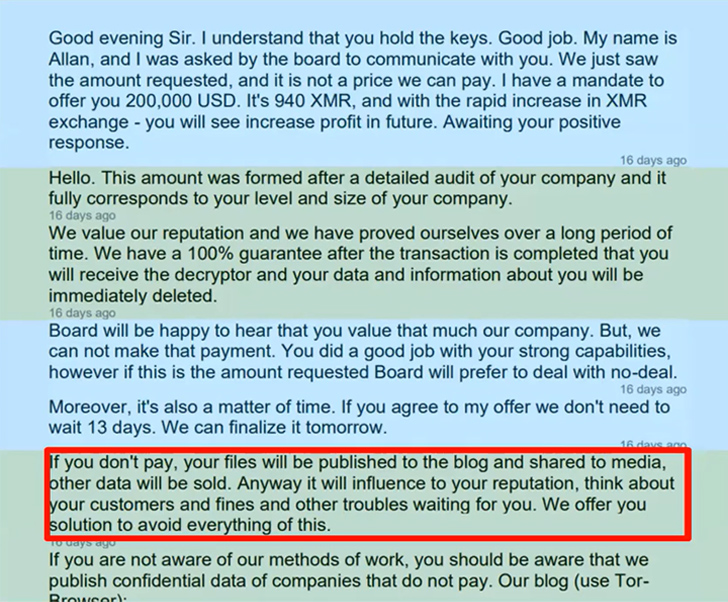
3. Assessing the “cost-of-no-deal” – Reflecting to the decision makers and the crisis managers what will happen if they don’t pay the ransom.For example, one company was able to buy 13 days through negotiations, allowing them to recover their information and relinquish paying the ransom altogether.
To Pay or Not to Pay?#
Etay Maor comments, “Ransomware is not an IT issue, it’s a business issue. “The decision whether to pay or not is a business decision, influenced by many factors. While the official FBI policy is not to pay, they enable companies to do so, if the CEO decides.
For example, in one case an online gaming company was losing more money than the ransom request every hour their operations were down, influencing their decision to pay the ransom as quickly as possible while minimizing negotiation time. US lawmakers have not banned ransomware payment either. This shows how complicated the issue is.
Tips for Protecting Against Ransomware Attacks#
Ransomware is becoming more prominent, but organizations can protect against it. Ransomware relies on phishing attacks and unpatched services. Therefore, it is recommended that CEOs meet their IT team regularly to ensure software and infrastructure are patched and up-to-date and that all important information is backed up. This will significantly reduce the chance of ransomware being able to exploit vulnerabilities and penetrate systems.
To learn more about ransomware attacks and how they are managed in real-time, watch the entire masterclass here.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.