5 Steps To Improve Your Security Posture In Microsoft Teams

Article written by Hananel Livneh, Head of Product Marketing at Adaptive Shield.
The cybersecurity risks of SaaS chat apps, such as Microsoft Teams or Slack, often go underestimated. Employees feel secure when communicating on apps that are connected to their corporate network. It’s exactly this misplaced trust within intra-organizational messaging that opens the door to sophisticated attacks by criminal threat actors using a wide range of malicious activities.
By contacting employees who are off-guard in SaaS chat apps, threat actors can conduct phishing campaigns, launch malware attacks, and employ sophisticated social engineering tactics.
These sophisticated tactics make it challenging for security teams to detect threats. Employees also lack education when it comes to cybersecurity awareness around messaging apps, as cyber training mainly focuses on phishing via email.
Microsoft Teams chats is a platform that is susceptible to a growing number of incidents as its massive user base is an attractive target for cybercriminals.
In the most recently reported case, AT&T Cybersecurity discovered phishing conducted against its Managed Detection and Response (MDR) customers over Microsoft Teams in a DarkGate malware attack.
This article will shed light on the sources of this attack, draw parallels with previously identified vulnerabilities, and provide actionable remediation steps to fortify your organization against threats of this nature.
Uncovering Vulnerabilities in Teams
In a recent attack that took place over Microsoft Teams, attackers leveraged the app to send over 1,000 group chat invites. When targets accepted the invitation, they were manipulated into downloading a file that contained DarkGate malware. DarkGate has been circulating since 2018 in limited cybercriminal malware attacks, but its usage is spreading widely via messaging apps.
As noted by the AT&T Cybersecurity team in its report, Microsoft enables External Access by default, which allows members of one organization to add users outside the organization to their Teams chats.
In light of previously identified vulnerabilities and misconfigurations in Microsoft Teams, it is evident that the platform is susceptible to multiple attack vectors.
Additional recent incidents involved similar tactics of threat actors exploiting external access settings to contact internal users, including the Storm 0324 attack and the GIFShell vulnerability.
Another vulnerability was found by Max Corbridge and Tom Ellson from JUMPSEC’s Red Team allowed threat actors to bypass file-sharing restrictions and deliver malware directly to a target’s Teams inbox.
Understanding the interconnected nature of these external access setting vulnerabilities is crucial when crafting a comprehensive security strategy for SaaS messaging apps.
To fortify your organization against these phishing attacks and vulnerabilities, the research team at SaaS security company Adaptive Shield recommends implementing the following remediation measures.
1. Review External Access
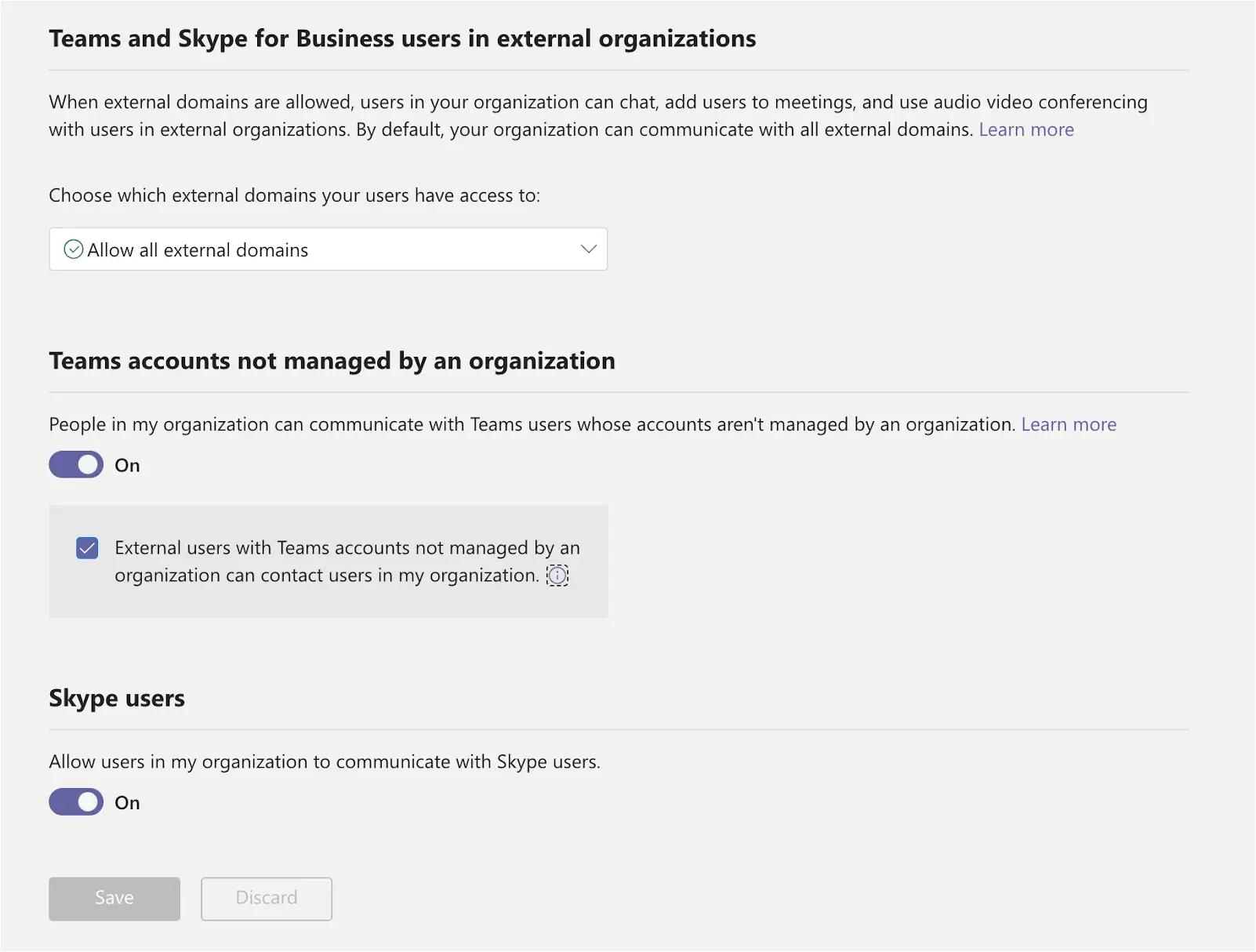
Assess the need for external tenants to message members of your organization. If it is not essential, disable external access in the Microsoft Teams Admins Center. Set the “Choose which external domains your users have access to” configuration to “Block all external domains.”
If external communication through Teams is required, enable access only for specific domains that regularly interact with users through Teams, to strike a balance between the organization’s communication needs and its security.
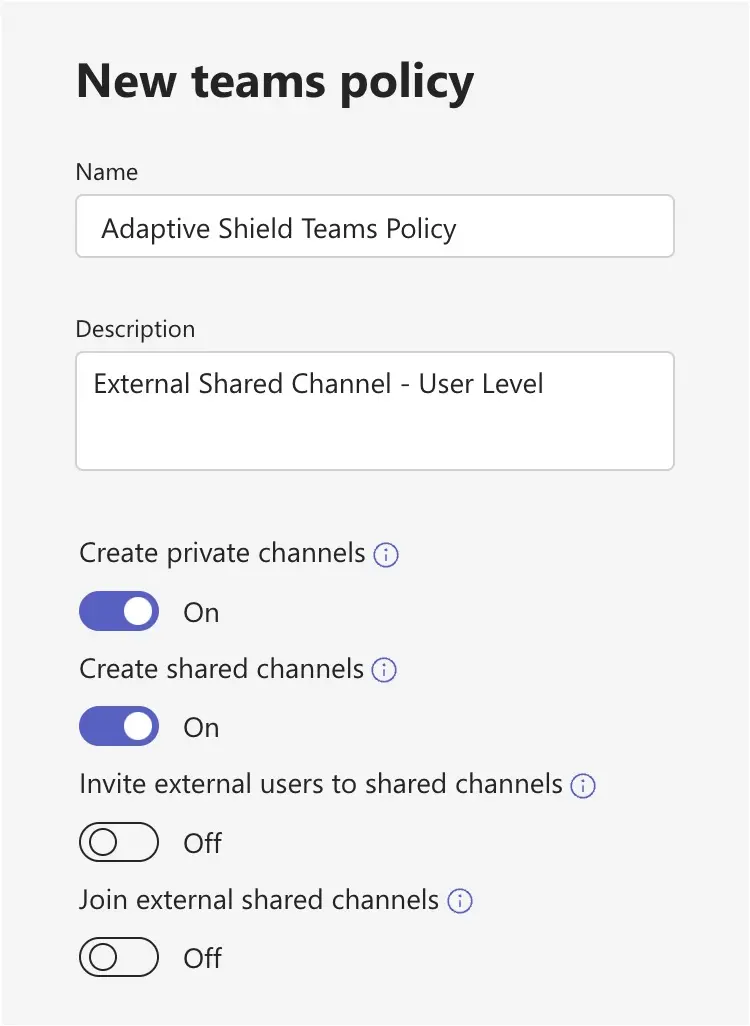
2. Block Invitations of External Users to Shared Channels
Shared Channel owners have the ability to invite external users to join their channel. This allows external users to read and write messages. In the Microsoft Teams Admin Center, under teams policy, toggle “Invite external users to shared channels” to off.
3. Limit Conversation Starters
Prevent unmanaged external Teams users from initiating conversations within your organization. In the Microsoft Teams External Access configurations, disable “External users with Teams accounts not managed by an organization can contact users in my organization.” By limiting who can start conversations, you reduce the likelihood of unauthorized access and communication.
4. Use Defender for Teams
Organizations that use Microsoft Defender for Office 365 can activate the Safe Attachments for Office 365 in the global settings to prevent users from inadvertently sharing malicious files in OneDrive and SharePoint+OneDrive. Once activated, Safe Attachments prevents users from opening or downloading files that are identified as malicious.

5. Educate Staff
Raise awareness among staff about social engineering campaigns that use productivity apps like Microsoft Teams. Emphasize that phishing attacks can take various forms beyond traditional emails. Encourage a security-conscious mindset and provide ongoing training so employees recognize and report suspicious activities.
Conclusion: Stay Proactive
As the threat landscape evolves, organizations must stay proactive in securing their communication SaaS platforms. By learning from recent phishing attacks and vulnerabilities, you can bolster your defenses against cyber threats.
Implementing the recommended remediation measures will contribute to a more secure Microsoft Teams environment, safeguarding your organization and its sensitive data from malicious actors.
Stay informed, stay vigilant, and prioritize SaaS security to ensure the resilience of your SaaS data.
Learn more about how to fortify your organization against threats on SaaS apps
Sponsored and written by Adaptive Shield.
