L4NC34 Ransomware Teaches That Ransomware Attacks Ought To Never Be Trifled With

There is no denying the fact that whenever the word ransomware is mentioned computers are an instinctive afterthought to have been largely infected by the same. The impact is without a doubt an extremely serious one and so it always escapes our notice that it’s the websites also that are touched upon by this impact.
While Ransomware is normally thought to be a method wherein files are encrypted in a super-perplexing way, alongside a ransom note asking hundreds to thousands of dollars’ worth of cryptocurrency.
Typically this is kind of the reality — however, attackers aren’t very similar to each other and not all may have the technical ability or would even attempt to go to such lengths.
Thus as of late, there was a case where the entire website files were apparently encrypted and had their file names changed to affix a “.crypt”.
Among the files, we additionally found the ransom note one might usually discover in this type of malware, but this one was somewhat unusual — it wasn’t an HTML or a .txt file. Rather, the ransom note was actually located inside a PHP file and appeared to contain actual capacities.
Here is a more critical look at the file.
The code of the malicious PHP file is as follows:
‘.base64_decode(‘PHRpdGxlPkw0TkMzNCBSYW5zb213YXJlPC90aXRsZT4KPGx[pbmsgcmVj[REDACTED BASE64 CODE]dCBNYWlsIDogbDRuYzM0MEBnbWFpbC5jb20=’).’
At first glance, nothing looks particularly surprising here, when decoded the result is:
“; } function decdir($dir){ $files = array_diff(scandir($dir), array(‘.’, ‘..’)); foreach($files as $file) { if(is_dir($dir.”/”.$file)){ decdir($dir.”/”.$file); }else { decfile($dir.”/”.$file); } } } decdir($_SERVER[‘DOCUMENT_ROOT’]); echo “
Webroot Decrypted
“; unlink($_SERVER[‘PHP_SELF’]); unlink(‘.htaccess’); copy(‘htabackup’,’.htaccess’); echo ‘Success !!!’; } else { echo ‘Failed Password !!!’; } exit(); } ?>

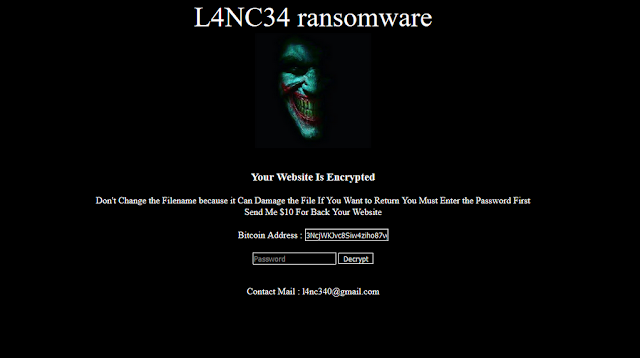
Your Website Is Encrypted
Don’t Change the Filename because it Can Damage the File If You Want to Return You Must Enter the Password First
Send Me $10 For Back Your Website
Bitcoin Address :
Contact Mail: [email protected]
Now the portions of code responsible for displaying the ransom note, along with the actual decryption process for the files are very clearly visible.
However, this code contains a few specific characteristics that are worth noting.
$input = $_POST[‘pass’]; $pass = “9c6679accb84e3ef938b1f4c24158355”; if(isset($input)) { if(md5($input) == $pass) {
This ‘snippet’ basically verifies if the password inputted on the page coordinates the hardcoded md5 hash. That appears to be somewhat odd; one may expect that the alleged key was not hardcoded — yet if so, at that point there might be a purpose behind these apparently encrypted files.
This next bit is answerable for the ransomware’s file decryption function:
function decfile($filename){ if (strpos($filename, ‘.crypt’) === FALSE) { return; } $decrypted = gzinflate(file_get_contents($filename)); file_put_contents(str_replace(‘.crypt’, ”, $filename), $decrypted); unlink(‘crypt.php’); unlink(‘.htaccess’); unlink($filename); echo “$filename Decrypted !!!
“;
While there really isn’t anything special or very complex about it. The decryption process just seems to take into account the actual contents of the file and then gzinflate them.
From what is clearly evident here, it’s safe to assume that the only way this hacker “encrypted” the files was to gzdeflate the files and change their file name.
This is what one of the encrypted files looked like:
Backing up to the original ransom note/script and modifying it to execute the decryption function without affecting anything else.
We can go ahead and run it either through a terminal or through the browser directly. And when done so with the following command:
$php ransom.php
Webroot Decrypted
Success !!!
What’s visible is the decrypted contents of the previous file, which look as expected.
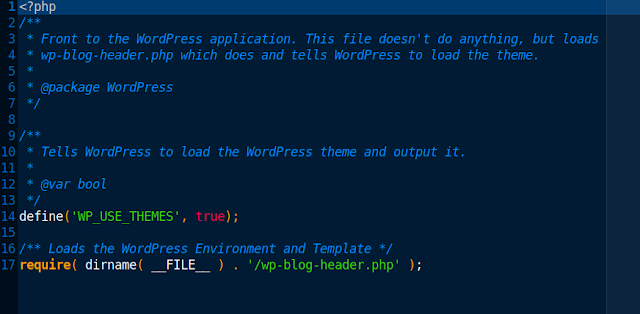
Well, thankfully the ransomware encryption was easily and quickly reverted without paying the $10 fee.
But the question that still stands strong is that since it’s so easy to reverse this infection, ‘Did someone ever even end up paying the attacker?’
The answer to which can be found if we take a look at the bitcoin wallet address
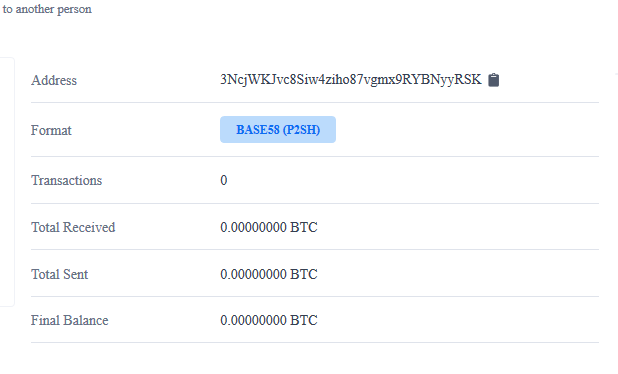
Fortunately, it appears that there were no transactions on this wallet. Ideally, that implies that none of the infected sites wound up paying the ransom and had the option to return the malignant file without issues.
In any case, this being observed the Ransomware attacks ought to never be trifled with as in the United States alone, potential expenses surpassed $7.5 billion in 2019. What’s more, much like other ransom included crimes, but still, there’s no guarantee that paying a ransom will end in a positive result.

![[Palo Alto Networks Security Advisories] CVE-2025-4614 PAN-OS: Session Token Disclosure Vulnerability 7 Palo_Alto_Networks_Logo](https://www.redpacketsecurity.com/wp-content/uploads/2025/02/Palo_Alto_Networks_Logo-300x55.png)

