A Module-Based Malware Spread by Word Document
As a module-based malware, Trickbot a malware family previously captured by FortiGuard Labs and afterward analyzed in 2016. It can broaden its functionalities by downloading new modules from its C&C server and executing them on its victim’s device.
While it was at first recognized as banking Trojan, it has progressively extended out its functionalities to gather credentials from its victims’ email accounts, browsers, installed network applications and so on. It is likewise able to send spam to its victim’s email contacts, just as deliver other malware to the victim’s device, like Emotet. As of late, FortiGuard Labs captured an MS Office Word sample in the wild that is spreading another variation of TrickBot.
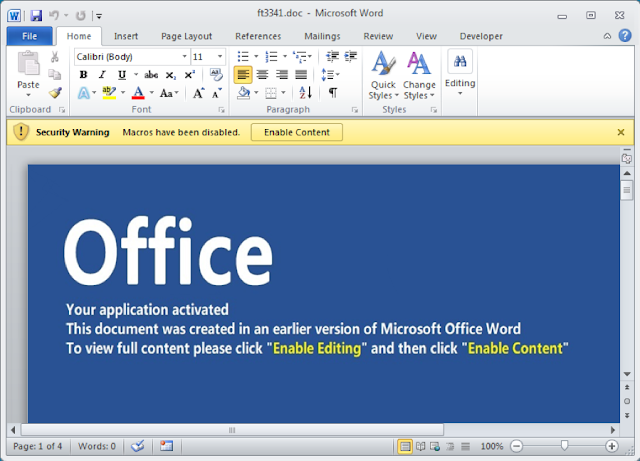
This is how by which it chips away at the victim’s machine. At the point when the malevolent Word document is opened with MS Office Word, it requests input, by requesting that the victim click the “Enable Content” button to empower the document’s Macro feature. When this is done, its malicious Macro (VBA code) is executed. By going to the Menu “Developer”- > “Visual Basic” we can look at the Macro’s VBA modules and code.
The Macro project is password-protected, so one can’t see any of the detailed data until the right password is provided. Luckily, there is an approach to sidestep this protection by changing its binary file. On the form, there is a Label control containing the malignant JS code, sketched out with a red rectangle. One of the VBA modules has an autorun() function which is called consequently when the Word doc opens. The VBA code at that point separates two files onto the victim’s framework.
One document is “C:AprilReportLogsTsgLogsTsg7LogsTsg8List1.bat”, with content “cscript/nologo C:AprilReportList1.jse”, and the other is “C:AprilReportList1.jse”, with JavaScript code from the label control, which is a tremendously jumbled JavaScript code. At that point, it begins the first extricated file “List1.bat”, which calls “script” running the huge JavaScript document “List1.jse”. The JavaScript code is heavily muddled. This secures the API function calls and consistent strings from being distinguished. They additionally utilize tons of unknown functions also.
At the point when the code starts, it first waits around for a minute to sidestep any auto-analysis devices by appearing to be dormant. After waiting, it then proceeds with the command “Select * from Win32_Process” to acquire every running procedure. It at that point puts the entirety of the names of these acquired procedures together and verifies whether its length is less than 3100.
Provided that this is true, it will raise an exception and close. For the most part, on a real computer, this length is bigger than 3100. As of now, it’s better ready to sidestep numerous auto-analysis systems, including Sandboxes and Virtual Machines.
For the solution for this issue, Fortinet customers are already said to have been shielded from this TrickBot variation by FortiGuard’s web filtering, Antivirus, and IPS benefits as follows: The downloading URL is appraised as “Malicious Websites” by the FortiGuard Web Filtering service. The Word doc and downloaded Dll record are distinguished as “VBA/TrickBot.MRVB!tr” and
“W32/TrickBot.EFDC!tr” and further blocked by the FortiGuard AntiVirus administration.
The IP locations of the C&C server are identified and then blocked by the FortiGuard IPS signature “Trojan.TrickBot”.



