(Almost) Hollow and Innocent: Monero Miner Remains Undetected via Process Hollowing

By Arianne Dela Cruz, Jay Nebre and Augusto Remillano II
As the value of cryptocurrencies increased (after a short dip in 2018), we observed increased activity from cryptocurrency mining malware this year, particularly infections and routines involving Monero miners. Over a span of a few months, we came across an infection routine that exploited vulnerabilities to propagate itself, and another that used fileless techniques to evade detection. Other routines involved the use of targeted attack tools to maximize profits, weaponized legitimate tools such as Windows Management Instrumentation to achieve persistence, and other sophisticated malware to hide cryptocurrency malware payloads to cash in on new platforms.
Recently, we found a cryptomining threat using process hollowing and a dropper component that requires a specific set of command line arguments to trigger its malicious behavior, leaving no trace for malicious activity detection or analysis to reference the file as malicious. The dropped file also acts as a container, which renders the main file inactive (without the correct arguments, the coinmining activity will also remain unexecuted). On its own, the file itself has no use and is not malicious, which allows it to evade detection. The campaign’s increased activity started in early November, and our telemetry recorded the most infection attempts on November 20th in Kuwait, Thailand, India, Bangladesh, the United Arab Emirates, Brazil and Pakistan.
Infection routine
The dropper is a 64-bit binary containing a packed malicious code, and we found the executable checking the arguments passed to it and verifying it upon unpacking.
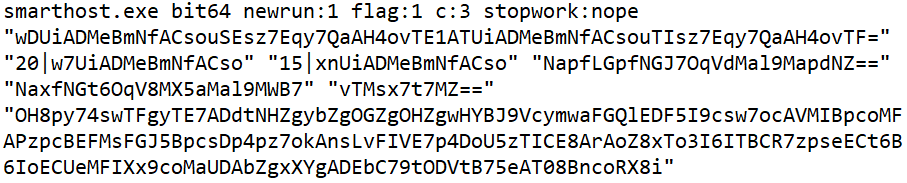
Figure 1. Unpacked 64-bit binary
Some of the parameters of the executable are encrypted, and decrypting the dropper’s argument revealed that the routine goes through two stages. First, it will perform specific arithmetic operations on the alphanumeric characters of the arguments. For this sample, we examined the argument vTMsx7t7MZ==, and applied this logic to every character in the string:
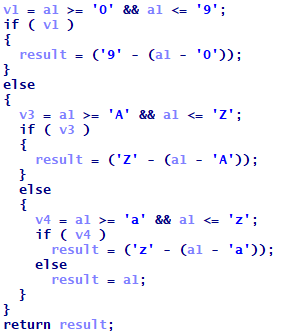
Figure 2. Arithmetic operations performed on the alphanumeric characters
We ended up with the string eGNhc2g2NA==, the regular Base64 encoded string that can be decoded using a number of tools. This decrypts a number of information from the arguments, including the cryptocurrency wallet address of the cybercriminals specified as part of the required arguments sent to trigger the malicious file and enable the coinmining activity:
- xcash64
- –donate-level 1 -o –0– -u XCA1nwsQ2hUe8GLawiqdCQbLe5FJjLXUCaQ48bLaZNdkiifhNyDDWi9ZQxhdWWVbfP5pizGtFar6jHoUx7cteUqo5DBsLe71Vg -p meer_m -a cn/double –k
The following are the possible file names of the dropped files:
- uakecobs.exe
- uakecobse.exe
- dakecobs.exe
- dakecobse.exe
- wakecobs.exe
- rakecobs.exe
Aside from requiring specific arguments, the dropper also obfuscates the names of the functions it will use for its malicious behavior.
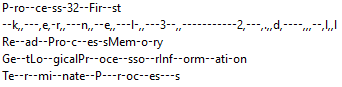
Figure 3. Snippets of obfuscated strings
Once executed with the correct arguments, the dropper drops and executes wakecobs.exe, a child process that will be created in a suspended state. Its memory will be unmapped and the dropper will then inject the malicious code onto it: an XMRig miner that runs unnoticed in the background.
Conclusion
While the number of new routines for malicious cryptocurrency miners have increased, overall detections for coinmining activities have decreased this year. We suspect that the cybercriminals behind this particular campaign may have been taking advantage of the decreased number of competitors especially as the year comes to a close. It’s also possible that the cybercriminals were exploring other regions to target with their cryptominer.
The dropper evades manual scanning and detection by injecting the malicious code in a dropped file and hiding itself in a different directory without an extension. By itself, the dropped file is considered non-malicious. Because the dropped copy doesn’t show any traces of cryptocurrency coinmining activity when submitted for whitebox, sandbox, and blackbox analysis, it presents certain challenges to IT teams and analysts. Its separate components, and without prior knowledge of the dropper component’s presence in the system, enterprises’ security teams may find no basis for tagging the file as malicious.
This technique can also be used to target and infect systems delivering other malware payloads. As the dropped file is only made of skeletal code with no behavior on its own, the file can stay undetected in the system and possibly evade even manual detection when dormant (the attackers can choose to activate the malware at specific times). The routine and technique is easy enough to implement for other cybercriminals to take advantage of, and enterprises should employ multilayered protections systems to make sure these kinds of threats do not compromise the company’s resources and assets.
Trend Micro solutions
Trend Micro endpoint solutions, such as the Smart Protection Suites and Worry-Free Business Security that have behavior monitoring capabilities, can protect users and businesses from these types of threats by detecting malicious files, scripts, commands, and messages as well as blocking all related malicious URLs. Trend Micro Apex One protection employs a variety of threat detection capabilities such as behavioral analysis, which protect against malicious scripts, injection, ransomware, as well as memory and browser attacks.
protection employs a variety of threat detection capabilities such as behavioral analysis, which protect against malicious scripts, injection, ransomware, as well as memory and browser attacks.
Indicators of Compromise (IoCs)
| SHA256 | Attribution | Detection |
| dd775ba66d6921035cc0cda61a6abff8f118a04a31eea082523157b48add4821 | Dropper | Coinminer.Win64.MALXMR.TIAOODCK |
| 04b495ee51e370fc93f431553bfdb592f678543c432137016d9ba4c64901a92a | Dropped file | Coinminer.Win64.MALXMR.TIAOODCJ |
URLs
39[.]99[.]146[.]107:47905 Disease vector
37[.]187[.]154[.]37:4466 Disease vector
MITRE ATT&CK Techniques
| Tactic | Technique | ID | Description |
| Defense evasion | Process injection | T1055 | Injection of coinmining routine to arbitrary dropped files |
| Command and control | Uncommonly used port | T1065 | Connects to ports 4466 and 3333 |
| Impact | Resource hijacking | T1496 | Mining routine that use up system resources |
The post (Almost) Hollow and Innocent: Monero Miner Remains Undetected via Process Hollowing appeared first on .

![[GLOBAL] - Ransomware Victim: loraincountyauditor[.]gov 6 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

