Anti-war open-source software developer targets Russians and Belarussians with “protestware”
Russia is in the midst of its fourth week of attack against Ukraine. People worldwide have been increasingly and passionately showing support for Ukrainians since day one while condemning the atrocities of Russian President Vladimir Putin, the Russian military, and Belarus, its allied country.
While there is truly increased risk against lives and property in the frontline, we have also seen certain risks online affecting individuals and businesses alike. There were scams; disinformation campaigns; and several wiper malware variants including HermeticWiper, IsaacWiper, and CaddyWiper. But one emerging trend we’re beginning to see play a part in the online impacts of the Russia-Ukraine war is the appearance of “protestware”.
When protestware doesn’t just protest
Protestware is a portmanteau of the words “protest” and “software.” It is software used in protest against something or someone—and we know what those are in the context of the current Ukraine crisis. Protestware is a very new term, but it has already come of age in a span of days.
Many open-source developers have started expressing their support (“We Stand With Ukraine”) on their official websites, either as content or banner. Some have also begun modifying their applications to include similar messages of support in the program’s UI or README text files.
One package, for example, called es5-ext, a small library (or a “shim”) that can be used in ECMAScript 5 or ECMAScript 6 environments, has been given a new dependency named postinstall.js, which displays a “call for peace” message when the shim is run on systems using a Russian IP address.
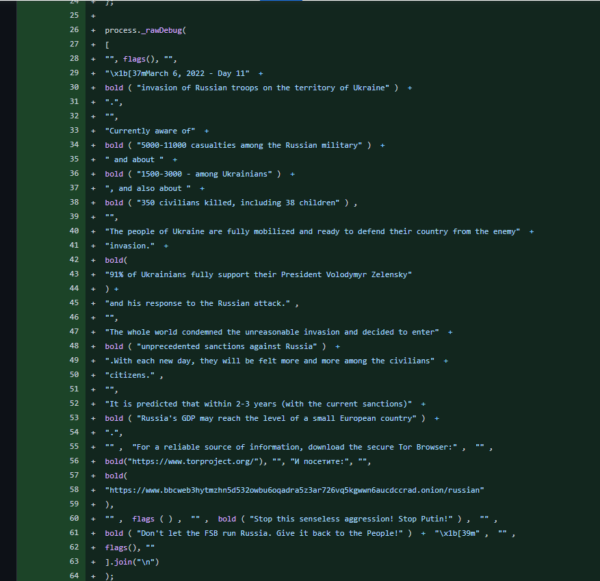
A portion of the message reads in English as follows:
Currently aware of 5000-11000 casualties among the Russian military and about 1500-3000 - among Ukranians, and also about 350 civilians killed, including 38 children.
The people of Ukraine are fully mobilized and ready to defend their country from the enemy invasion. 91% of Ukrainians fully support their President Volodymyr Zelensky and his response to the Russian attack.
The whole world condemned the unreasonable invasion and decided to enter unprecedented sanctions against Russia. With each new day, they will be felt more and more among the civilians citizens. It is predicted that within 2-3 years (with the current sanctions) Russia's GDP may reach the level of a small European country.Fellow developers criticized medikoo, the brains behind es5-ext and postinstall.js, saying “the NPM package is not a place for politics.” One even went as far as calling this benign change to the shim “malware.” But medicoo stood his ground, saying he’ll only remove the dependency “once the aggression stops, and Ukrainians can live in peace in their own country.”
Not all changes to one’s work are benign, though. Several open-source developers have started gravely sabotaging their projects by adding code that, at its worse, would wreak havoc on systems that download and run them.
One popular application, node-ipc, was updated in early March to include code that, according to Liran Tal, a security researcher from cybersecurity company Snyk, “raised concerns for suspicious activity and potential abuse of the source code and the package’s behavior.” When executed on systems geolocated in Russia or Belarus, versions 10.1.1 and 10.1.2 completely wipe files from machines and replace them with the heart emoji.
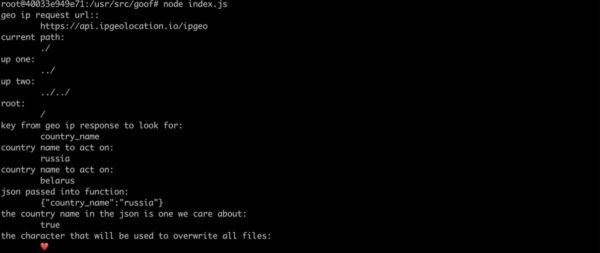
node-ipc developer Brandon Nozaki Miller (also known as RIAEvangelist, Sparky, and Electric Cowboy) also created a new library called PeaceNotWar. It carries the same wiping capabilities as the node-ipc package. Miller added this library as a dependency of node-ipc version 11.0.0. So every time node-ipc is called by other dependencies that import it, PeaceNotWar executes as well. One of the library’s payloads is to drop a file named WITH-LOVE-FROM-AMERICA.txt into an affected user’s desktop and their OneDrive.
Miller did the same for node-ipc version 9.2.2, the latest stable version of the package that many projects rely on. But he also added the highly popular module, colors, as a dependency on this package. Doing so would pull in nasty code deliberately created to introduce an infinite loop to the source code, triggering a denial of service (DoS) to any Node.js server using it.
Suffice to say, servers using version 9.2.2 would be rendered useless.
Portions of PeaceNotWar‘s README page on Github says this:
This code serves as a non-destructive example of why controlling your node modules is important. It also serves as a non-violent protest against Russia's aggression that threatens the world right now. This module will add a message of peace on your users' desktops, and it will only do it if it does not already exist just to be polite.
...
I pledge that this module, to the best of my knowledge and skills, does not do any damage to anyone's data. If you do not like what this module does, please just lock your dependencies to any of my work or other's which includes this module, to a version you have code reviewed and deemed acceptable for your needs. Also, please code-review your other modules for vulnerabilities.We have not confirmed that this module is already free of malicious code.
For those who are anti-war and pro-Ukraine, this form of protest may seem appropriate. But Snyk’s Tal raised questions that revealed a lack of foresight on the part of Miller in sabotaging his work and deploying his protestware.
“How does that reflect on the maintainer’s future reputation and stake in the developer community? Would this maintainer ever be trusted again to not follow up on future acts in such or even more aggressive actions for any projects they participate in?” Tal said in a post.
The US National Institute and Standards and Technology (NIST) recognizes the malicious package versions of node-ipc as a vulernability, which is tracked as CVE-2022-23812.
When protestware ripples out
Because of the new threat posed by protestware against Russia, Sberbank, Russia’s biggest state-owned bank, advised Russians to not update any software due to “increased cyberattacks.”
“We urge users to stop updating software now, and developers to tighten control over the use of external source code,” a press release from the bank states, “If there is an urgent need to use software, be sure to check all downloaded files with an antivirus, and when using someone else’s code in your programs, conduct a manual or automatic check, including, view the text of the source code.”
“In addition, various content and malicious code can be embedded in freely distributed libraries used for software development. The use of such software can lead to malware infection of personal and corporate computers, as well as IT infrastructure.”
The National Coordination Center for Computer Incidents (NCCCI), a Russian cybersecurity agency, also issued a list of recommended guidelines (text in Russian) for IT risk for Russian companies and organizations in light of sabotaged open-source software.
In an unfortunate and ironic turn of events, a Washington-based American NGO who monitors human rights in post-Soviet states is one of those affected by Miller’s protestware. A Github post, which has already been taken down but preserved for posterity here, details the harm that the protestware has caused the organization—and they are likely to seek litigation against the developer as a result:
Since our start in 2014, we have been in contact with 2,500 whistleblowers that provided us with detailed reports on various kinds of abuse happening there.
Due to internet censorship there, one of the web services used to contact us securely was hosted on servers located inside Belarus. Normally, we backup the received content to an external server on 20th day of every month, as this is reasonable given the volume we usually get, but since the start of the invasion on February 24th, traffic to our web service has increased over fiftyfold. Our staff has been working round the clock to accomodate the influx and during one of their tasks, package containing node-ipc module was updated on a production server, which resulted in executing your code and wiping over 30,000 messages and files detailing war crimes commited in Ukraine by Russian army and government officials. Due to the way the files were stored on the server, we are not able to recover any data and it's most likely gone forever. For some of the senders, this might as well have been their last contact with the outside world, as many of them were front-line soldiers that could've been killed in action during the offensive.
Personally, me and my colleagues are absolutely devastated. All I can say that your little shenanigan did more damage to us than Putin or Lukashenka ever could.Snyk has recommended that developers refrain from using affected packages of these modified FOSS (free and open source) projects altogether. If that is not possible, however, they should use an npm package manager to override poisoned versions and use a clean version instead.
When protestware becomes a point of no return
Protestware is one of the ways internet users have actively used tech to make a statement of support for Ukrainians, combat Russian government misinformation, and deliver news to Russian civilians who are victims of their own state’s propaganda and severe censorship.
Apart from the developers of these poisoned packages, no developer has been happy with what protestware had to offer. For one thing, a great majority of developers see the FOSS ecosystem as politically agnostic. Although the intent is understandable, many agree that there are better avenues for developers, especially those who maintain popular packages with millions of downloads, to exercise their support for a people or cause.
Protestware, whether seen as benign or malicious, throws a spanner in the face of developer trust. It has also, yet again, raised concerns about the safety and integrity of the software supply chain. All it takes is one developer deciding to turn things around and ruin everyone’s day. This is something any open-source software would start thinking more often, like a gray cloud hanging over their heads, uncertain of when sabotage might happen next.
“The Pandora’s box is now opened, and from this point on, people who use open source will experience xenophobia more than ever before, EVERYONE included,” writes GitHub user NM17. “The trust factor of open source, which was based on goodwill of the developers is now practically gone, and now, more and more people are realizing that one day, their library/application can possibly be exploited to do/say whatever some random dev on the internet thought was ‘the right thing to do.’ Not a single good came out of this ‘protest.’”
The post Anti-war open-source software developer targets Russians and Belarussians with “protestware” appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.



