Apepe – Enumerate Information From An App Based On The APK File
Apepe is a Python tool developed to help pentesters and red teamers to easily get information from the target app. This tool will extract basic informations as the package name, if the app is signed and the development language…
Installing / Getting started
A quick guide of how to install and use Apepe.
- Python installed on your machine
- The .apk from the target mobile app
Features
- Detect mobile app development lanague
- Information gathering
- Extremely fast
- Low RAM and CPU usage
- Made in Python
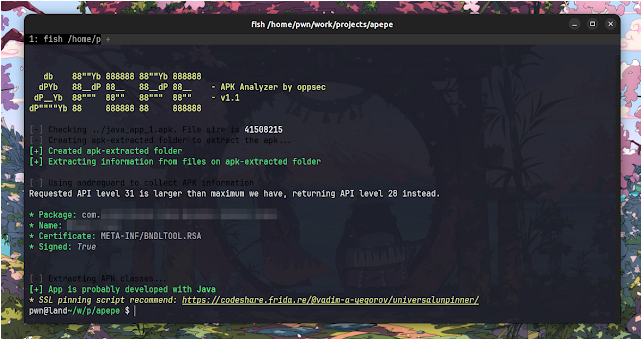
Example
To-Do
- Support to .ipa files (iOS)
- Detect certificate library used by the app
- Add argument to return list of possible SSL Pinning scripts
- Common vulnerabilities check?
Contributing
A quick guide of how to contribute with the project.
1. Create a fork from Apepe repository
2. Download the project with git clone https://github.com/your/Apepe.git
3. cd Apepe/
4. Make your changes
5. Commit and make a git push
6. Open a pull requestWarning
- The developer is not responsible for any malicious use of this tool.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.


![[LYNX] - Ransomware Victim: Inside One 3 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
