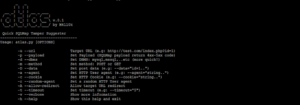
RMIScout – Wordlist And Bruteforce Strategies To Enumerate Java RMI Functions And Exploit RMI Parameter Unmarshalling Vulnerabilities
RMIScout performs wordlist and bruteforce attacks against exposed Java RMI interfaces to safely guess method signatures without invocation.On misconfigured servers,...