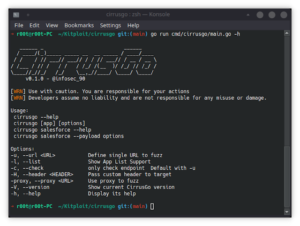
Chisel-Strike – A .NET XOR Encrypted Cobalt Strike Aggressor Implementation For Chisel To Utilize Faster Proxy And Advanced Socks5 Capabilities
A .NET XOR encrypted cobalt strike aggressor implementation for chisel to utilize faster proxy and advanced socks5 capabilities. Why write...










![[DEVMAN] - Ransomware Victim: m*c*e*ic*l[.]com 26 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
![Cobalt Strike Beacon Detected - 165[.]154[.]125[.]212:8080 27 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)
