Chinese Hackers Exploit VMware Zero-Day to Backdoor Windows and Linux Systems
The Chinese state-sponsored group known as UNC3886 has been found to exploit a zero-day flaw in VMware ESXi hosts to backdoor Windows and Linux systems.
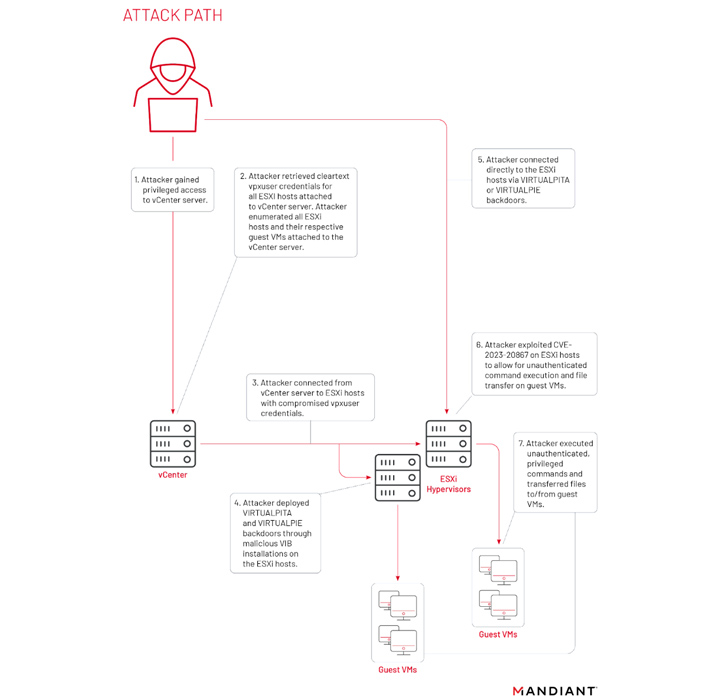
The VMware Tools authentication bypass vulnerability, tracked as CVE-2023-20867 (CVSS score: 3.9), “enabled the execution of privileged commands across Windows, Linux, and PhotonOS (vCenter) guest VMs without authentication of guest credentials from a compromised ESXi host and no default logging on guest VMs,” Mandiant said.
UNC3886 was initially documented by the Google-owned threat intelligence firm in September 2022 as a cyber espionage actor infecting VMware ESXi and vCenter servers with backdoors named VIRTUALPITA and VIRTUALPIE.
Earlier this March, the group was linked to the exploitation of a now-patched medium-severity security flaw in the Fortinet FortiOS operating system to deploy implants on the network appliances and interact with the aforementioned malware.
The threat actor has been described as a “highly adept” adversarial collective targeting defense, technology, and telecommunication organizations in the U.S., Japan, and the Asia-Pacific region.
“The group has access to extensive research and support for understanding the underlying technology of appliances being targeted,” Mandiant researchers said, calling out its pattern of weaponizing flaws in firewall and virtualization software that do not support EDR solutions.
As part of its efforts to exploit ESXi systems, the threat actor has also been observed harvesting credentials from vCenter servers as well as abusing CVE-2023-20867 to execute commands and transfer files to and from guest VMs from a compromised ESXi host.
A notable aspect of UNC3886’s tradecraft is its use of Virtual Machine Communication Interface (VMCI) sockets for lateral movement and continued persistence, thereby allowing it to establish a covert channel between the ESXi host and its guest VMs.
Discover the untapped vulnerabilities in your API ecosystem and take proactive steps towards ironclad security. Join our insightful webinar!
Get Ready to Learn“This open communication channel between guest and host, where either role can act as client or server, has enabled a new means of persistence to regain access on a backdoored ESXi host as long as a backdoor is deployed and the attacker gains initial access to any guest machine,” the company said.
The development comes as Summoning Team researcher Sina Kheirkhah disclosed three different flaws in VMware Aria Operations for Networks (CVE-2023-20887, CVE-2023-20888, and CVE-2023-20889) that could result in remote code execution.
“UNC3886 continues to present challenges to investigators by disabling and tampering with logging services, selectively removing log events related to their activity,” it further added. “The threat actors’ retroactive cleanup performed within days of past public disclosures on their activity indicates how vigilant they are.”
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.







![[GLOBAL] - Ransomware Victim: loraincountyauditor[.]gov 8 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

