Credit card skimmer piggybacks on Magento 1 hacking spree
Back in the fall of 2020 threat actors started to massively exploit a vulnerability in the no-longer maintained Magento 1 software branch. As a result, thousands of e-commerce shops were compromised and many of them injected with credit card skimming code.
While monitoring activities tied to this Magento 1 campaign, we identified an e-commerce shop that had been targeted twice by skimmers. This in itself is not unusual, multiple infections on the same site are common.
However this case was different. The threat actors devised a version of their script that is aware of sites already injected with a Magento 1 skimmer. That second skimmer will simply harvest credit card details from the already existing fake form injected by the previous attackers.
In the incident we describe in this post, the threat actors also took into account that an e-commerce site may get cleaned up from a Magento 1 hack. When that happens, an alternate version of their skimmer injects its own fields that mimic a legitimate payments platform.
Mass Magento 1 infections
The Magento 1 end-of-life coupled with a popular exploit turned out to be a huge boon for threat actors. A large number of sites have been hacked indiscriminately just because they were vulnerable.
RiskIQ attributed these incidents to Magecart Group 12, which has a long history of web skimming using various techniques including supply-chain attacks.
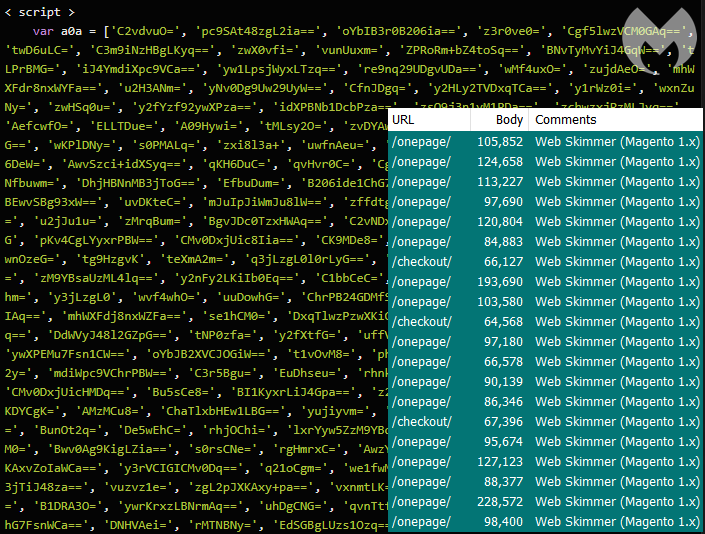
This skimmer is rather lengthy and contains various levels of obfuscation that make debugging it more challenging. Although there are variations, the format and decoy payment form are very much the same.
No honor among thieves
Costway is a retailer that started to sell its own name-brand products via platforms such as Amazon and later rolled out costway.com and subsequent localized online stores. Their French portal (costway[.]fr) attracted about 180K visitors last December.
Our crawlers identified that the websites for Costway France, UK, Germany and Spain, which run the Magento 1 software, had been compromised around the same time frame.
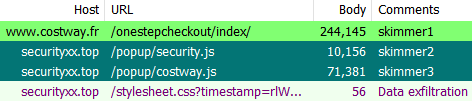
We can see the credit card skimmer injection directly on the checkout page for costway[.]fr as it stands out in English while the rest of the site is in French. This is not surprising considering that the Magento 1 hacking campaign is automated and fairly indiscriminate.
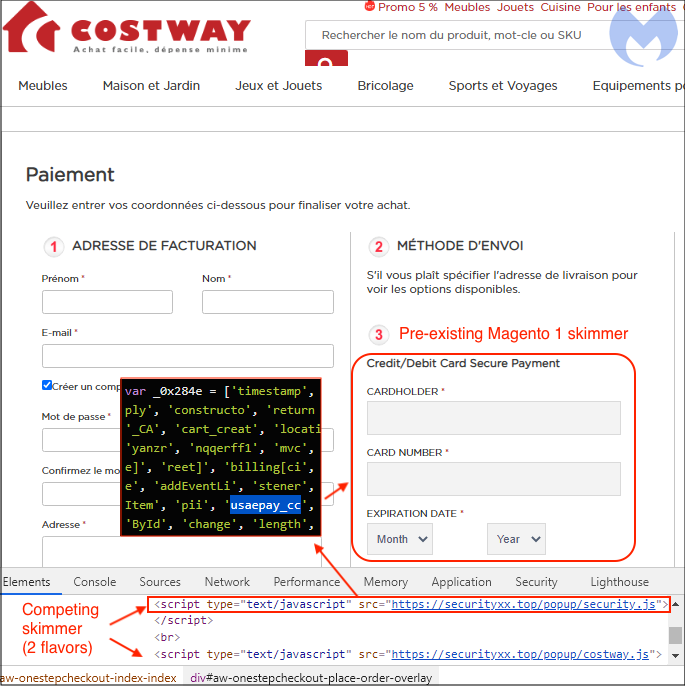
But what’s more interesting is that another skimmer is also present on the site (loaded externally from securityxx[.]top) and targeting the Magento 1 skimmer.
It’s possible that the threat actors’ level of access to e-commerce sites differs. The former exploit a core vulnerability that grants them root access while perhaps the latter can only perform specific types of injections. If that is the case, this would explain why they simply leave the fake form alone and grab credentials from it.
There’s an additional twist here where the criminals also planned for the scenario where the e-commerce site gets cleaned up from the Magento 1 injection.
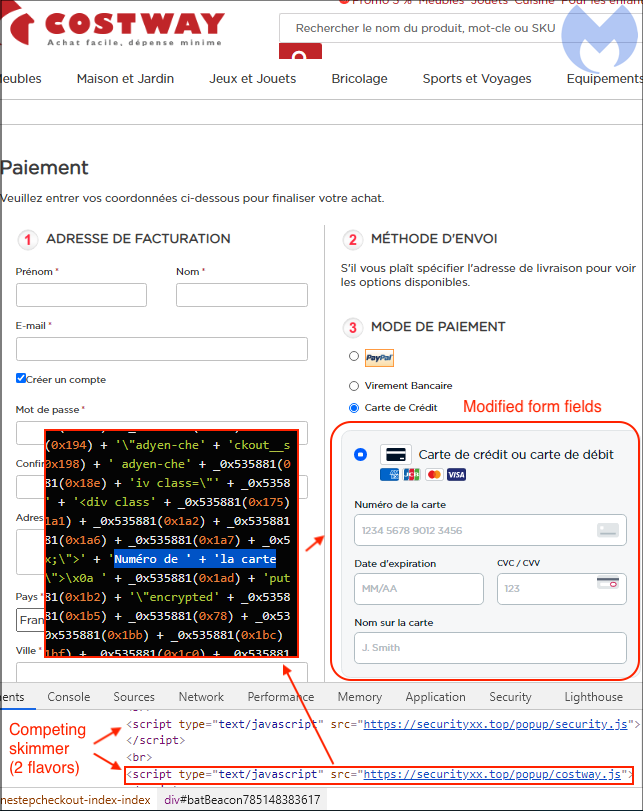
The skimmer creates its own form fields which closely ressemble the legitimate ones from the Adyen payments platform that Costway uses. Visually, only a very small style change (font size) gives it away, but there are more significant implications under the hood.
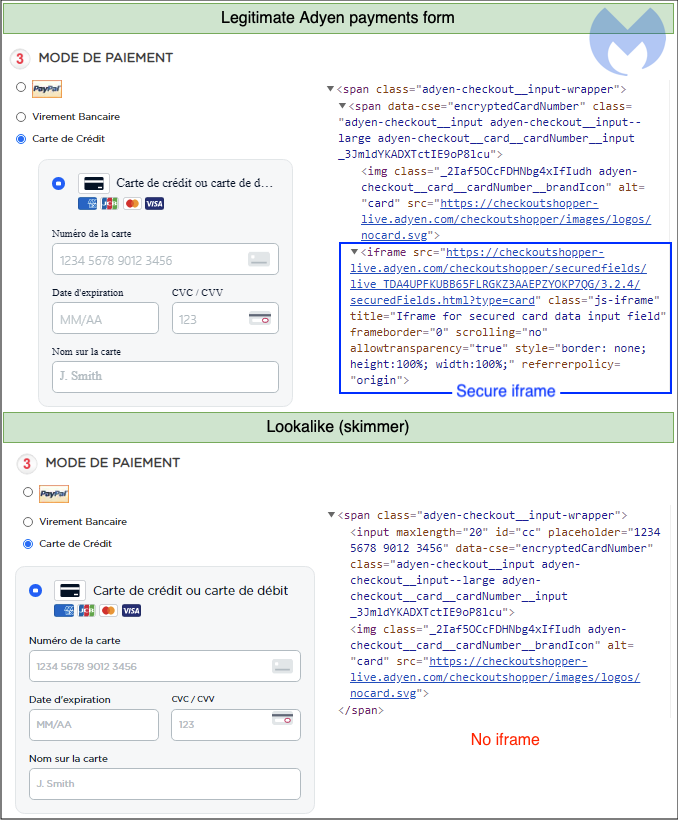
Adyen encrypts the form fields using their proprietary technology. The threat actors wanted to recreate the same look and feel from Adyen but be able to harvest the credit card information in their own way.
To summarize, from a victim’s perspective, there are 3 different skimmers that get loaded when they proceed to the checkout page.
- Magento 1 hack skimmer injected directly in checkout page
- Custom skimmer (securityxx[.]top/security.js) that steals from Magento 1 skimmer
- Custom skimmer (securityxx[.]top/costway.js) that alters legitimate payment iframe
Previous skimmer
The same threat actors were already busy working on Costway’s compomise at least in late December 2020 as recorded in this urlscanio crawl. They used the custom domain costway[.]top to host their code.
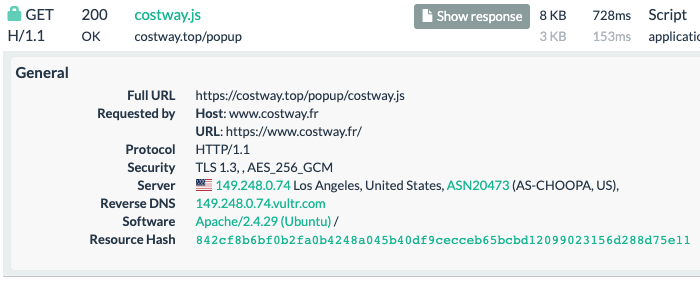
The domain costway[.]top is related to a family we have come across before. There is overlap with the skimmer code they use, naming conventions and even infrastructure.
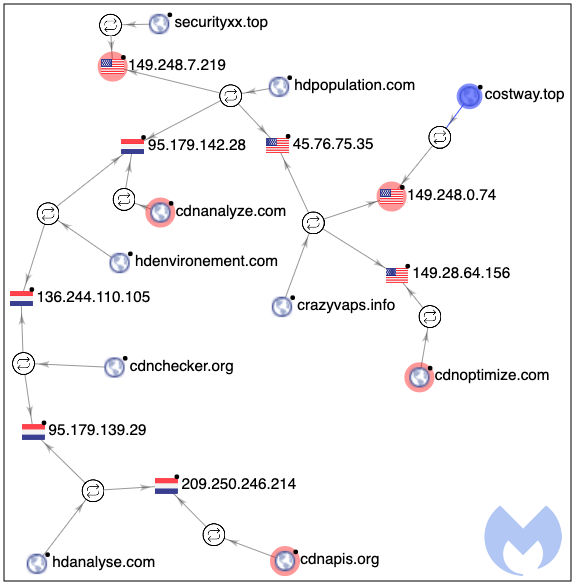
At the moment, this group is quite active and continues with the same techniques we have seen several months ago.
Competing for resources
A large number of Magento 1 sites have been hacked but yet are not necessarily being monetized. Other threat actors that want access will undoubtedly attempt to inject their own malicious code. When that happens, we see criminals trying to access the same resources and sometimes fighting with one another.
We informed Costway during our investigation but also witnessed their site getting reinfected. The costway[.]top domain was discarded in favor of securityxx[.]top where threat actors customized the skimmer specifically for them.
At the time of writing, costway[.]fr is still compromised but Malwarebytes users are protected thanks to our Browser Guard extension and general web protection available in our software.
We would like to thank Jordan Herman over at RiskIQ for sharing additional indicators with us.
Indicators of Compromise (IOCs)
securityxx[.]top
costway[.]top
hdpopulation[.]com
cdnanalyze[.]com
hdenvironement[.]com
crazyvaps[.]info
cdnchecker[.]org
cdnoptimize[.]com
hdanalyse[.]com
cdnapis[.]org
cookiepro[.]cloud
cdndoubleclick[.]net
149[.]248[.]7[.]219
95[.]179[.]142[.]28
45[.]76[.]75[.]35
136[.]244[.]110[.]105
149[.]248[.]0[.]74
149[.]28[.]64[.]156
95[.]179[.]139[.]29
209[.]250[.]246[.]214
The post Credit card skimmer piggybacks on Magento 1 hacking spree appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[FLOCKER] - Ransomware Victim: G*********************y[.]org 9 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

