Crimeware trends: self-propagation and driver exploitation

Introduction
If one sheep leaps over the ditch, the rest will follow. This is an old saying, found in various languages, and it can be applied to ransomware developers. In previous blog posts, we highlighted an increase in the popularity of platform-independent languages and ESXi support, and recently, we wrote about ransomware borrowing these propagation methods.
Last month, we wrote in our crimeware reporting service about further ransomware variants that now had their own methods for copying and executing malware on other machines within the network. We also wrote about a case of abusing vulnerable drivers, something that might become popular in the future as well. In this blog post, we provide excerpts from these reports.
For questions or more information on our crimeware reporting service, please contact [email protected].
Some ransomware statistics
During the first ten months of 2022, the share of users affected by targeted ransomware among all users affected by all types of malware almost doubled year-on-year, reaching 0.026%.
Share of users attacked by targeted ransomware, January–October 2021 and January–October, 2022 (download)
LockBit
LockBit is one of the most popular, innovative and rapidly developing current ransomware families. Recently, we noticed that a new option was added to the LockBit builder site, as can be seen below:
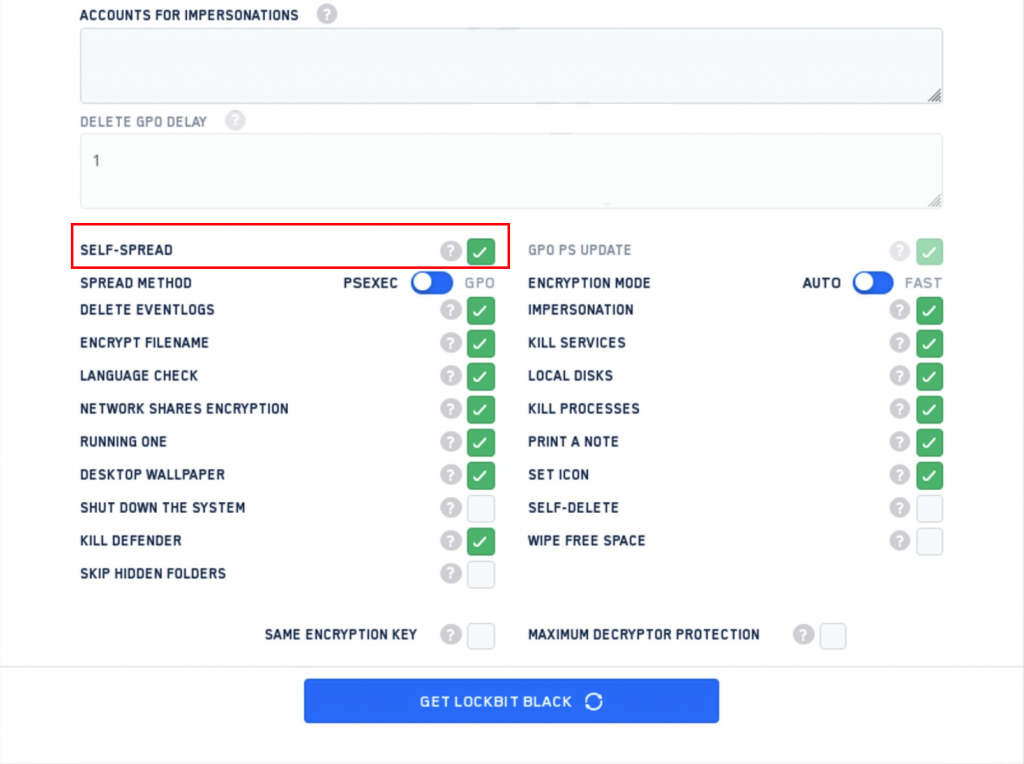
New functionality created by LockBit developers
In addition to PsExec, the most common way of spreading ransomware overall, LockBit now supports “self-spread”. Naturally, we were interested in the details of this self-spreading mechanism—especially, how it works.
The ransomware is installed as a service onto the infected machine. This service makes a call to netapi32.DsGetDcNameW to get the details of the domain that the infected machine belongs to and then creates a named pipe. When this operation is complete, the module dumps the operating system credentials, obtaining the handles from explorer.exe and lsass.exe with the help of the named pipe created earlier.
This is where it stops. Essentially, there is no self-spreading—this is more of credential dumping. Although it fits in the broader trend we are seeing these days—more and more functionality embedded in ransomware to reduce reliance on other tools—there is no self-spreading, as it is no longer necessary to use tools like Mimikatz.
Play
Play is a new ransomware variant that we recently ran into—it has no code similarities with other ransomware samples. The ransomware is highly obfuscated, which complicates analysis.
Play is in an early development stage. For example, there is no leak site and victims have to contact the criminals via the email address in the ransom note. Despite this, Play also contains functionality that lately has been found in other ransomware variants: self-propagation.
Play collects different IPs on the same subnet and tries to discover SMB resources with the help of NetShareEnum(), which results in ARP traffic, as can be seen from the Wireshark screenshot below. The idea behind this activity is to spread the ransomware to other machines on the same network.
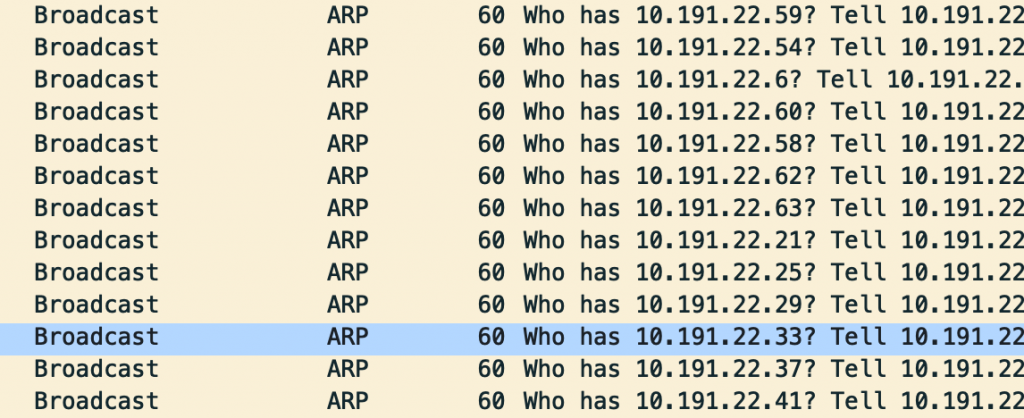
ARP requests made by Play ransomware
Once an SMB resource is found, the ransomware establishes a connection, and tries to mount it, and to spread and execute itself in the remote system. This can be seen in the Wireshark screenshot below.
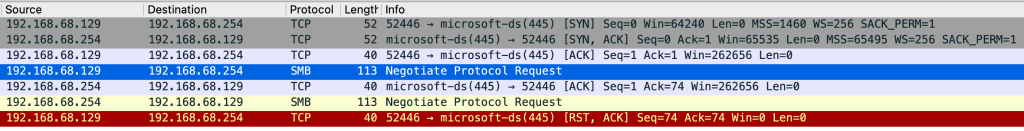
SMB connections
Driver abuse
Drivers can contain vulnerabilities that attackers may be able to exploit. One such driver is Anti Rootkit by Avast. Although it was previously abused by AvosLocker, the vulnerabilities that are being exploited now (CVE-2022-26522 and CVE-2022-26523) were not known back then. They allow attackers to escalate their privileges in the targeted system or perform a sandbox escape. The vulnerabilities were described in detail by SentinelLabs and fixed at the beginning of 2022. We know that at least two ransomware families, AvosLocker and Cuba, exploit these.
There are a few advantages to using the trick with vulnerable drivers. Firstly, it disables other security products in the system. Secondly, it is a security solution that is being installed, which results in fewer alerts being raised. Thirdly, by exploiting the driver, the attackers can kill processes running on the machine.
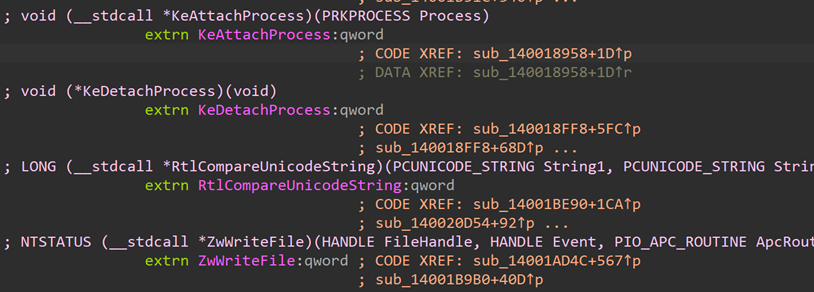
The process killing function
Conclusion
Ransomware developers keep an eye on their competitors’ work. If one of them implements certain functionality that works well, chances are that others will follow suit This keeps their ransomware more interesting for their affiliates. The self-propagation of ransomware is a prime example of that.
Therefore, we believe that faulty drivers could be yet another instance of typical ransomware group TTP that other groups will borrow in the future.
Intelligence reports can help you to protect yourself against these threats. If you want to stay up to date on the latest TTPs used by criminals or if you have questions about our private reports, please contact [email protected].
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.



![[HANDALA] - Ransomware Victim: Hotam EC 8 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)