Daily Vulnerability Trends: Sun Dec 18 2022
| CVE NAME | CVE Description |
| CVE-2021-4045 | TP-Link Tapo C200 IP camera, on its 1.1.15 firmware version and below, is affected by an unauthenticated RCE vulnerability, present in the uhttpd binary running by default as root. The exploitation of this vulnerability allows an attacker to take full control of the camera. |
| CVE-2022-27518 | Unauthenticated remote arbitrary code execution |
| CVE-2022-4543 | No description provided |
| CVE-2019-19781 | An issue was discovered in Citrix Application Delivery Controller (ADC) and Gateway 10.5, 11.1, 12.0, 12.1, and 13.0. They allow Directory Traversal. |
| CVE-2022-21225 | Improper neutralization in the Intel(R) Data Center Manager software before version 4.1 may allow an authenticated user to potentially enable escalation of privilege via adjacent access. |
| CVE-2022-45451 | No description provided |
| CVE-2022-28672 | This vulnerability allows remote attackers to execute arbitrary code on affected installations of Foxit PDF Reader 11.2.1.53537. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file. The specific flaw exists within the handling of Doc objects. The issue results from the lack of validating the existence of an object prior to performing operations on the object. An attacker can leverage this vulnerability to execute code in the context of the current process. Was ZDI-CAN-16640. |
| CVE-2022-44698 | Windows SmartScreen Security Feature Bypass Vulnerability. |
| CVE-2022-45025 | Markdown Preview Enhanced v0.6.5 and v0.19.6 for VSCode and Atom was discovered to contain a command injection vulnerability via the PDF file import function. |
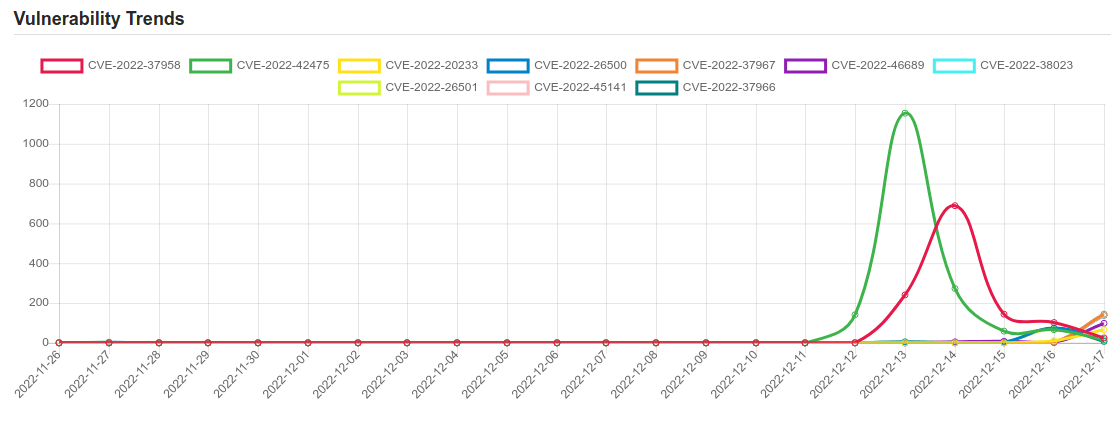
| CVE-2022-37958 | SPNEGO Extended Negotiation (NEGOEX) Security Mechanism Information Disclosure Vulnerability. |
| CVE-2022-42475 | No description provided |
| CVE-2022-20233 | In param_find_digests_internal and related functions of the Titan-M source, there is a possible out of bounds write due to an incorrect bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-222472803References: N/A |
| CVE-2022-26500 | Improper limitation of path names in Veeam Backup & Replication 9.5U3, 9.5U4,10.x, and 11.x allows remote authenticated users access to internal API functions that allows attackers to upload and execute arbitrary code. |
| CVE-2022-37967 | Windows Kerberos Elevation of Privilege Vulnerability. |
| CVE-2022-46689 | A race condition was addressed with additional validation. This issue is fixed in tvOS 16.2, macOS Monterey 12.6.2, macOS Ventura 13.1, macOS Big Sur 11.7.2, iOS 15.7.2 and iPadOS 15.7.2, iOS 16.2 and iPadOS 16.2, watchOS 9.2. An app may be able to execute arbitrary code with kernel privileges. |
| CVE-2022-38023 | Netlogon RPC Elevation of Privilege Vulnerability. |
| CVE-2022-26501 | Veeam Backup & Replication 10.x and 11.x has Incorrect Access Control (issue 1 of 2). |
| CVE-2022-45141 | No description provided |
| CVE-2022-37966 | Windows Kerberos RC4-HMAC Elevation of Privilege Vulnerability. |
| CVE-2022-39066 | There is a SQL injection vulnerability in ZTE MF286R. Due to insufficient validation of the input parameters of the phonebook interface, an authenticated attacker could use the vulnerability to execute arbitrary SQL injection. |
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below

To keep up to date follow us on the below channels.




![[QILIN] - Ransomware Victim: www[.]nuphoton[.]com 6 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)