Daily Vulnerability Trends: Sat Jun 18 2022
| CVE NAME | CVE Description |
| CVE-2021-38665 | Remote Desktop Protocol Client Information Disclosure Vulnerability |
| CVE-2022-23222 | kernel/bpf/verifier.c in the Linux kernel through 5.15.14 allows local users to gain privileges because of the availability of pointer arithmetic via certain *_OR_NULL pointer types. |
| CVE-2022-22057 | Use after free in graphics fence due to a race condition while closing fence file descriptor and destroy graphics timeline simultaneously in Snapdragon Auto, Snapdragon Compute, Snapdragon Connectivity, Snapdragon Industrial IOT, Snapdragon Mobile, Snapdragon Wearables |
| CVE-2022-20798 | A vulnerability in the external authentication functionality of Cisco Secure Email and Web Manager, formerly known as Cisco Security Management Appliance (SMA), and Cisco Email Security Appliance (ESA) could allow an unauthenticated, remote attacker to bypass authentication and log in to the web management interface of an affected device. This vulnerability is due to improper authentication checks when an affected device uses Lightweight Directory Access Protocol (LDAP) for external authentication. An attacker could exploit this vulnerability by entering a specific input on the login page of the affected device. A successful exploit could allow the attacker to gain unauthorized access to the web-based management interface of the affected device. |
| CVE-2021-40604 | A Server-Side Request Forgery (SSRF) vulnerability in IPS Community Suite before 4.6.2 allows remote authenticated users to request arbitrary URLs or trigger deserialization via phar protocol when generating class names dynamically. In some cases an exploitation is possible by an unauthenticated user. |
| CVE-2022-32969 | No description provided |
| CVE-2022-27924 | Zimbra Collaboration (aka ZCS) 8.8.15 and 9.0 allows an unauthenticated attacker to inject arbitrary memcache commands into a targeted instance. These memcache commands becomes unescaped, causing an overwrite of arbitrary cached entries. |
| CVE-2021-27748 | No description provided |
| CVE-2022-27511 | Corruption of the system by a remote, unauthenticated user. The impact of this can include the reset of the administrator password at the next device reboot, allowing an attacker with ssh access to connect with the default administrator credentials after the device has rebooted. |
| CVE-2022-22620 | A use after free issue was addressed with improved memory management. This issue is fixed in macOS Monterey 12.2.1, iOS 15.3.1 and iPadOS 15.3.1, Safari 15.3 (v. 16612.4.9.1.8 and 15612.4.9.1.8). Processing maliciously crafted web content may lead to arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited.. |
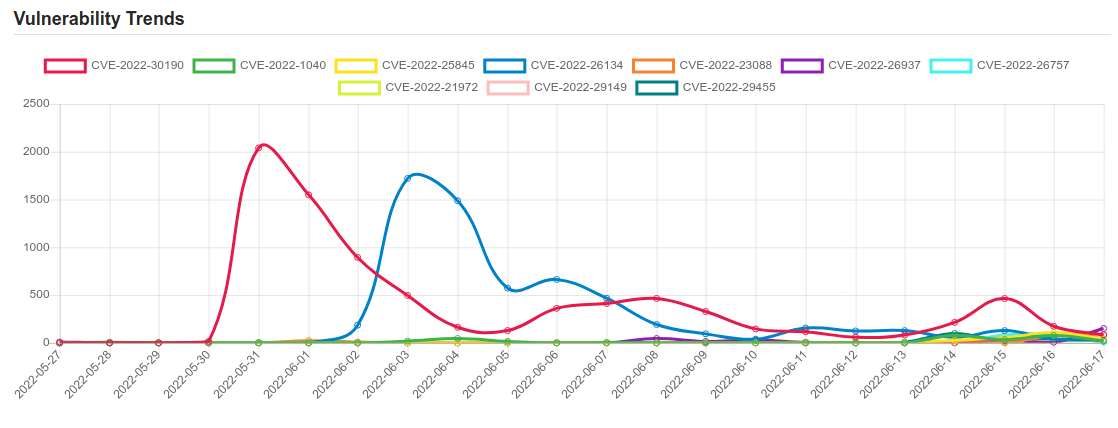
| CVE-2022-30190 | Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability. |
| CVE-2022-1040 | An authentication bypass vulnerability in the User Portal and Webadmin allows a remote attacker to execute code in Sophos Firewall version v18.5 MR3 and older. |
| CVE-2022-25845 | The package com.alibaba:fastjson before 1.2.83 are vulnerable to Deserialization of Untrusted Data by bypassing the default autoType shutdown restrictions, which is possible under certain conditions. Exploiting this vulnerability allows attacking remote servers. Workaround: If upgrading is not possible, you can enable [safeMode](https://github.com/alibaba/fastjson/wiki/fastjson_safemode). |
| CVE-2022-26134 | In affected versions of Confluence Server and Data Center, an OGNL injection vulnerability exists that would allow an unauthenticated attacker to execute arbitrary code on a Confluence Server or Data Center instance. The affected versions are from 1.3.0 before 7.4.17, from 7.13.0 before 7.13.7, from 7.14.0 before 7.14.3, from 7.15.0 before 7.15.2, from 7.16.0 before 7.16.4, from 7.17.0 before 7.17.4, and from 7.18.0 before 7.18.1. |
| CVE-2022-23088 | No description provided |
| CVE-2022-26937 | Windows Network File System Remote Code Execution Vulnerability. |
| CVE-2022-26757 | A use after free issue was addressed with improved memory management. This issue is fixed in tvOS 15.5, iOS 15.5 and iPadOS 15.5, Security Update 2022-004 Catalina, watchOS 8.6, macOS Big Sur 11.6.6, macOS Monterey 12.4. An application may be able to execute arbitrary code with kernel privileges. |
| CVE-2022-21972 | Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability. This CVE ID is unique from CVE-2022-23270. |
| CVE-2022-29149 | Azure Open Management Infrastructure (OMI) Elevation of Privilege Vulnerability. |
| CVE-2022-29455 | DOM-based Reflected Cross-Site Scripting (XSS) vulnerability in Elementor’s Elementor Website Builder plugin <= 3.5.5 versions. |
If you like the site, please consider joining the telegram channel and supporting us on Patreon using the button below.


![[INCRANSOM] - Ransomware Victim: coruzcitywndata+ 3 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)