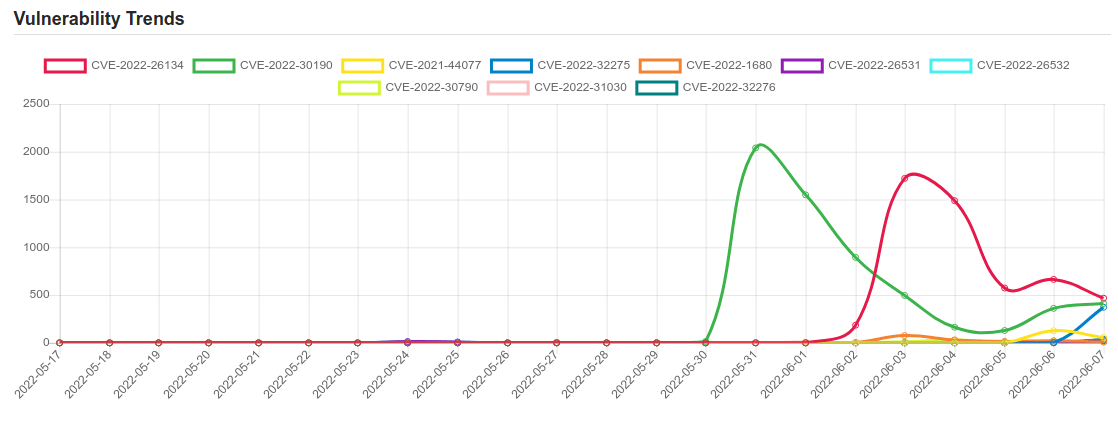
Daily Vulnerability Trends: Wed Jun 08 2022
| CVE NAME | CVE Description |
| CVE-2022-30552 | No description provided |
| CVE-2021-40444 | Microsoft MSHTML Remote Code Execution Vulnerability |
| CVE-2019-13764 | Type confusion in JavaScript in Google Chrome prior to 79.0.3945.79 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page. |
| CVE-2021-3695 | No description provided |
| CVE-2022-28737 | No description provided |
| CVE-2022-28736 | No description provided |
| CVE-2202-26134 | No description provided |
| CVE-2022-28735 | No description provided |
| CVE-2021-3697 | No description provided |
| CVE-2022-1966 | A use-after-free vulnerability was found in the Linux kernel’s Netfilter subsystem in net/netfilter/nf_tables_api.c. This flaw allows a local attacker with user access to cause a privilege escalation issue. |
| CVE-2022-32275 | Grafana 8.4.3 allows reading files via (for example) a /dashboard/snapshot/%7B%7Bconstructor.constructor’/.. /.. /.. /.. /.. /.. /.. /.. /etc/passwd URI. |
| CVE-2022-1680 | An account takeover issue has been discovered in GitLab EE affecting all versions starting from 11.10 before 14.9.5, all versions starting from 14.10 before 14.10.4, all versions starting from 15.0 before 15.0.1. When group SAML SSO is configured, the SCIM feature (available only on Premium+ subscriptions) may allow any owner of a Premium group to invite arbitrary users through their username and email, then change those users’ email addresses via SCIM to an attacker controlled email address and thus – in the absence of 2FA – take over those accounts. It is also possible for the attacker to change the display name and username of the targeted account. |
| CVE-2022-26531 | Multiple improper input validation flaws were identified in some CLI commands of Zyxel USG/ZyWALL series firmware versions 4.09 through 4.71, USG FLEX series firmware versions 4.50 through 5.21, ATP series firmware versions 4.32 through 5.21, VPN series firmware versions 4.30 through 5.21, NSG series firmware versions 1.00 through 1.33 Patch 4, NXC2500 firmware version 6.10(AAIG.3) and earlier versions, NAP203 firmware version 6.25(ABFA.7) and earlier versions, NWA50AX firmware version 6.25(ABYW.5) and earlier versions, WAC500 firmware version 6.30(ABVS.2) and earlier versions, and WAX510D firmware version 6.30(ABTF.2) and earlier versions, that could allow a local authenticated attacker to cause a buffer overflow or a system crash via a crafted payload. |
| CVE-2022-26532 | A argument injection vulnerability in the ‘packet-trace’ CLI command of Zyxel USG/ZyWALL series firmware versions 4.09 through 4.71, USG FLEX series firmware versions 4.50 through 5.21, ATP series firmware versions 4.32 through 5.21, VPN series firmware versions 4.30 through 5.21, NSG series firmware versions 1.00 through 1.33 Patch 4, NXC2500 firmware version 6.10(AAIG.3) and earlier versions, NAP203 firmware version 6.25(ABFA.7) and earlier versions, NWA50AX firmware version 6.25(ABYW.5) and earlier versions, WAC500 firmware version 6.30(ABVS.2) and earlier versions, and WAX510D firmware version 6.30(ABTF.2) and earlier versions, that could allow a local authenticated attacker to execute arbitrary OS commands by including crafted arguments to the CLI command. |
| CVE-2022-30790 | No description provided |
| CVE-2022-31030 | No description provided |
| CVE-2022-32276 | No description provided |
| CVE-2022-26134 | Confluence Server and Data Center code execution | CVE-2022-26134 |
| CVE-2022-30190 | Microsoft Windows Support Diagnostic Tool (MSDT) code execution | CVE-2022-30190 |
| CVE-2021-44077 | Zoho security update-CVE-2021-44077 |
If you like the site, please consider joining the telegram channel and supporting us on Patreon using the button below.



