Daily Vulnerability Trends: Mon Aug 15 2022
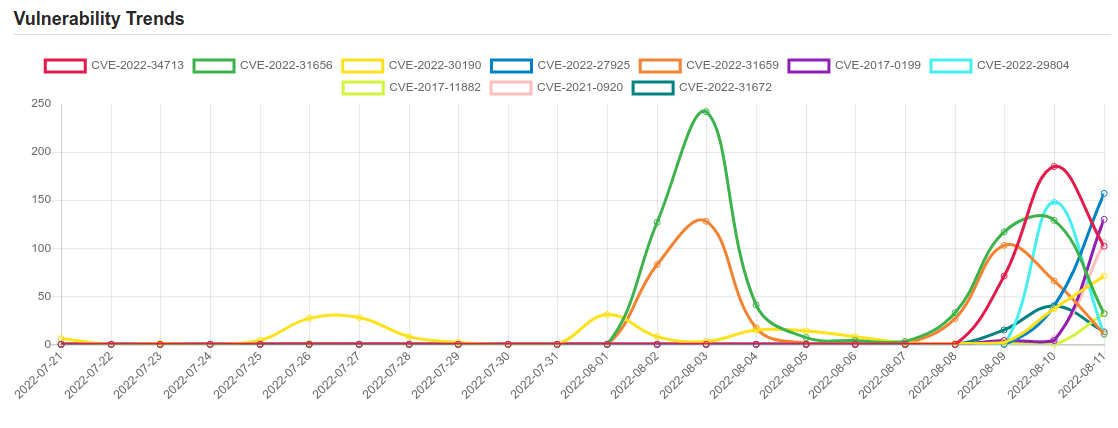
| CVE NAME | CVE Description |
| CVE-2017-11882 | Microsoft Office 2007 Service Pack 3, Microsoft Office 2010 Service Pack 2, Microsoft Office 2013 Service Pack 1, and Microsoft Office 2016 allow an attacker to run arbitrary code in the context of the current user by failing to properly handle objects in memory, aka “Microsoft Office Memory Corruption Vulnerability”. This CVE ID is unique from CVE-2017-11884. |
| CVE-2021-0920 | In unix_scm_to_skb of af_unix.c, there is a possible use after free bug due to a race condition. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-196926917References: Upstream kernel |
| CVE-2022-31672 | VMware vRealize Operations contains a privilege escalation vulnerability. A malicious actor with administrative network access can escalate privileges to root. |
| CVE-2022-31675 | VMware vRealize Operations contains an authentication bypass vulnerability. An unauthenticated malicious actor with network access may be able to create a user with administrative privileges. |
| CVE-2022-31674 | VMware vRealize Operations contains an information disclosure vulnerability. A low-privileged malicious actor with network access can access log files that lead to information disclosure. |
| CVE-2022-30134 | Microsoft Exchange Information Disclosure Vulnerability. This CVE ID is unique from CVE-2022-21979, CVE-2022-34692. |
| CVE-2022-2588 | No description provided |
| CVE-2022-31101 | prestashop/blockwishlist is a prestashop extension which adds a block containing the customer’s wishlists. In affected versions an authenticated customer can perform SQL injection. This issue is fixed in version 2.1.1. Users are advised to upgrade. There are no known workarounds for this issue. |
| CVE-2022-30333 | RARLAB UnRAR before 6.12 on Linux and UNIX allows directory traversal to write to files during an extract (aka unpack) operation, as demonstrated by creating a ~/.ssh/authorized_keys file. NOTE: WinRAR and Android RAR are unaffected. |
| CVE-2022-2586 | No description provided |
| CVE-2022-2585 | No description provided |
| CVE-2022-35665 | Adobe Acrobat Reader versions 22.001.20169 (and earlier), 20.005.30362 (and earlier) and 17.012.30249 (and earlier) are affected by a Use After Free vulnerability that could result in arbitrary code execution in the context of the current user. Exploitation of this issue requires user interaction in that a victim must open a malicious file. |
| CVE-2022-0028 | A PAN-OS URL filtering policy misconfiguration could allow a network-based attacker to conduct reflected and amplified TCP denial-of-service (RDoS) attacks. The DoS attack would appear to originate from a Palo Alto Networks PA-Series (hardware), VM-Series (virtual) and CN-Series (container) firewall against an attacker-specified target. To be misused by an external attacker, the firewall configuration must have a URL filtering profile with one or more blocked categories assigned to a source zone that has an external facing interface. This configuration is not typical for URL filtering and, if set, is likely unintended by the administrator. If exploited, this issue would not impact the confidentiality, integrity, or availability of our products. However, the resulting denial-of-service (DoS) attack may help obfuscate the identity of the attacker and implicate the firewall as the source of the attack. We have taken prompt action to address this issue in our PAN-OS software. All software updates for this issue are expected to be released no later than the week of August 15, 2022. This issue does not impact Panorama M-Series or Panorama virtual appliances. This issue has been resolved for all Cloud NGFW and Prisma Access customers and no additional action is required from them. |
| CVE-2022-34713 | Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability. This CVE ID is unique from CVE-2022-35743. |
| CVE-2022-31656 | VMware Workspace ONE Access, Identity Manager and vRealize Automation contain an authentication bypass vulnerability affecting local domain users. A malicious actor with network access to the UI may be able to obtain administrative access without the need to authenticate. |
| CVE-2022-30190 | Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability. |
| CVE-2022-27925 | Zimbra Collaboration (aka ZCS) 8.8.15 and 9.0 has mboximport functionality that receives a ZIP archive and extracts files from it. An authenticated user with administrator rights has the ability to upload arbitrary files to the system, leading to directory traversal. |
| CVE-2022-31659 | VMware Workspace ONE Access and Identity Manager contain a remote code execution vulnerability. A malicious actor with administrator and network access can trigger a remote code execution. |
| CVE-2017-0199 | Microsoft Office 2007 SP3, Microsoft Office 2010 SP2, Microsoft Office 2013 SP1, Microsoft Office 2016, Microsoft Windows Vista SP2, Windows Server 2008 SP2, Windows 7 SP1, Windows 8.1 allow remote attackers to execute arbitrary code via a crafted document, aka “Microsoft Office/WordPad Remote Code Execution Vulnerability w/Windows API.” |
| CVE-2022-29804 | Incorrect conversion of certain invalid paths to valid, absolute paths in Clean in path/filepath before Go 1.17.11 and Go 1.18.3 on Windows allows potential directory traversal attack. |
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below

To keep up to date follow us on the below channels.






