Enhancing your application security program with continuous monitoring

Historically, cybersecurity models have been largely reactive. Organizations would assess vulnerabilities at specified intervals, typically following a security incident or a scheduled audit. While this method does have its merits, the dynamic nature of today’s cyber threats demands a more proactive approach to cybersecurity.
The standard security model of point-in-time assessments has worked well in the past and has their place for distinct use cases. But with the increase in zero-day vulnerabilities, polymorphic malware, and Advanced Persistent Threats (APTs), there’s an argument for more frequent, even continuous, cybersecurity evaluations.
Let’s explore the differences between these two approaches and how they can help organizations enhance their application security program, and beyond.
Traditional web application pen testing vs. pen testing as a service
Point-in-time assessments are like snap-shots taken at a particular instance of time. This approach is effective in detecting vulnerabilities that exist only at that specific moment.
Traditional pen testing is one example of how these assessments are carried out. A team of ethical hackers would be hired to annually assess and identify vulnerabilities in an organization’s network, systems, and apps.
In contrast, pen testing as a service (PTaaS) takes a continuous monitoring approach. PTaaS is an ongoing process that combines manual testing with automated tools to continuously scan for vulnerabilities and threats.
This approach offers a more proactive form of security that allows organizations to detect potential weaknesses before they become exploitable.
While point-in-time pen testing assessments provide a brief overview of an organization’s security posture; PTaaS gives organizations the opportunity to identify vulnerabilities earlier and take corrective action before threats become exploitable.
Best pen testing approach for securing web apps
To secure web applications, organizations can now choose between traditional web application penetration testing and PTaaS. The decision often hinges on an organization’s specific needs and challenges.
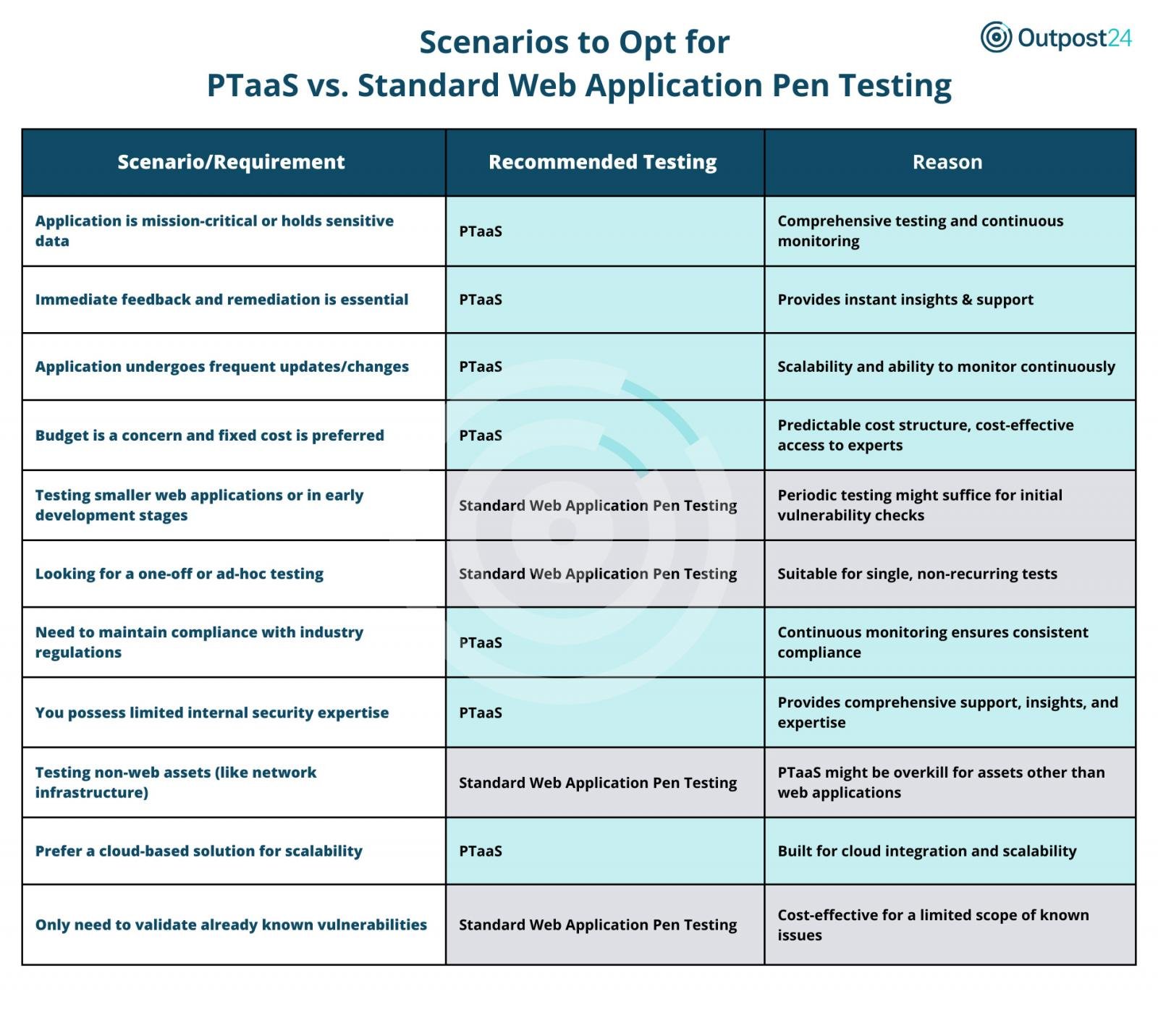
PTaaS shines in situations where:
- Mission-critical applications are involved, demanding comprehensive and continuous monitoring.
- Immediate feedback is paramount. PTaaS offers rapid detection and remediation support.
- The application frequently updates or changes, requiring scalable, continuous vigilance.
- Organizations seek a predictable cost structure and expert insights without straining the budget.
- Consistent compliance with industry regulations is a priority, and continuous monitoring becomes a necessity.
- There’s limited internal security expertise, making external comprehensive support vital.
- A cloud-based solution is preferred for its scalability and integration capabilities.
- Seamless integration with CI/CD pipelines is required, especially in agile development environments.
Standard web application pen testing is ideal when:
- The focus is on smaller web applications or those in the early stages, where periodic checks can suffice.
- The need is for one-off or ad-hoc tests without the requirement of ongoing monitoring.
- The aim is to test non-application assets like network infrastructure, where a specialized approach is more cost-effective.
- The primary goal is to validate known vulnerabilities, offering a targeted and cost-effective solution.
- Detailed analysis of specific vulnerabilities, such as Cross-Site Scripting (XSS) or SQL Injection, is required.
In essence, both testing methods offer valuable insights, but the context determines the best fit. Organizations should align their choice with their unique challenges to ensure optimal cybersecurity outcomes.
Embracing the continuous monitoring approach across the board
Beyond securing web applications, innovations like Endpoint Attack Surface Management (EASM) and Risk-Based Vulnerability Management (RBVM) have emerged as game changers for elevating an organization’s cybersecurity posture.
EASM enables organizations to gain a holistic view into their external attack surface. Its automated approach enables organization to reduce the risk of a cyberattack by identifying and analyzing vulnerable assets in real time, even those they don’t know about.
Historically, vulnerability management was a reactive game, often plagued with the challenge of ‘alert fatigue’. But Risk-Based Vulnerability Management (RBVM) changed that narrative. Rather than flagging every vulnerability as seen in traditional vulnerability scanning, RBVM tools prioritize them based on contextual risk. This helps organizations make better decisions about which vulnerabilities to address first.
As the contours of cyber threats evolve, so must our defence mechanisms. Embracing continuous monitoring in PTaaS, EASM, and RBVM, is not just a strategy – it’s imperative for businesses in today’s digital landscape.
Recognizing this shift, Outpost24 offers cybersecurity solutions that provide a unified, continuous, and proactive approach to improve cyber resilience.
From web application testing at scale, to attack surface analysis and vulnerability management, we help organization address potential issues before they escalate.
Sponsored and written by Outpost24
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.


![[HANDALA] - Ransomware Victim: Hotam EC 4 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)