Fake Trump sex video used to spread QNode RAT
Researchers uncovered a malspam campaign that spreads the QNode remote access Trojan (RAT) using fake Trump’s sex scandal video as bait.
Security experts from Trustwave uncovered a malspam campaign that is delivering the QNode remote access Trojan (RAT) using fake Trump’s sex scandal video as bait.
The spam messages use the subject “GOOD LOAN OFFER!!” and have attached to the email an archive containing a Java Archive (JAR) file called “TRUMP_SEX_SCANDAL_VIDEO.jar”.
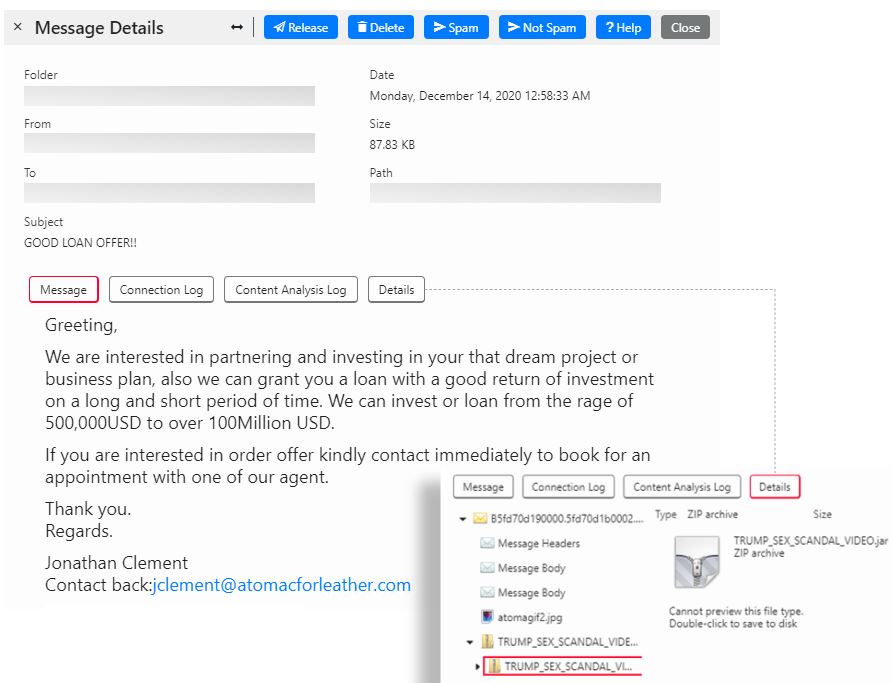
Upon executing the attachment, the malicious code attempts to install the Qnode RAT on the recipient’s machine.
“While reviewing our spam traps, a particular campaign piqued our interest primarily because the attachment to the email does not coincide with the theme of the email body.” states the post published by the experts.” “We suspect that the bad guys are attempting to ride the frenzy brought about by the recently concluded Presidential elections since the filename they used on the attachment is totally unrelated to the email’s theme.”
The downloader distributed in this malspam campaign appears to be a variant of the QRAT downloader that was discovered by Trustwave researchers in August.
Experts highlighted some other similarities with the older variants such as the obfuscation of the JAR file with the Allatori Obfuscator, the support for Windows OS only, and the fact that the installer of Node.Js is retrieved from the official website nodejs.org.
The QRAT variant continues to have multi-stage downloaders. The first downloader is the JAR file used as an attachment in the spam message.
As detailed in the August report published by Trustwave, the first downloader has two major tasks, it first sets up the Node.Js platform onto the system, then downloads and executes the second-stage downloader.
The second-stage downloader named “wizard.js” fetches and executes the Qnode RAT from an C2 server, it is also to achieve persistence on the infected system.
The new variant employed in the new campaign has the following notable new features and changes:
- this JAR sample is significantly larger than the one used in past campaigns;
- threat actor behind this campaign added a GUI and a supposed Microsoft ISC License into the JAR’s code.
- this variant not use the string “qnodejs“ to evade detection and the downloader code was split-up into different buffers inside the JAR.
- when downloading next stage malware, only the argument “–hub-domain” is required when communicating to the command-and-control servers (C&Cs).
- the JAR file downloads a file named “boot.js” and saves it at %temp%_qhub_node_{random}
QRAT support multiple RAT features, including, obtaining system information, performing file operations, and acquiring credentials of certain applications. This variant supports multiple applications, including Chrome, Firefox, Thunderbird, and Outlook.
“This threat has been significantly enhanced over the past few months since we first examined it. To achieve the same end goal, which is to infect the system with a QNode RAT, the JAR file downloader characteristics and behavior were improved.” concludes the report.
“While the attachment payload has some improvements over previous versions, the email campaign itself was rather amateurish, and we believe that the chance this threat will be delivered successfully is higher if only the email was more sophisticated.”
If you want to receive the weekly Security Affairs Newsletter for free subscribe here.
|
|
Pierluigi Paganini
(SecurityAffairs – hacking, RAT)
The post Fake Trump sex video used to spread QNode RAT appeared first on Security Affairs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.



