Fake Vpn Chrome Extensions Force Installed 15 Million Times

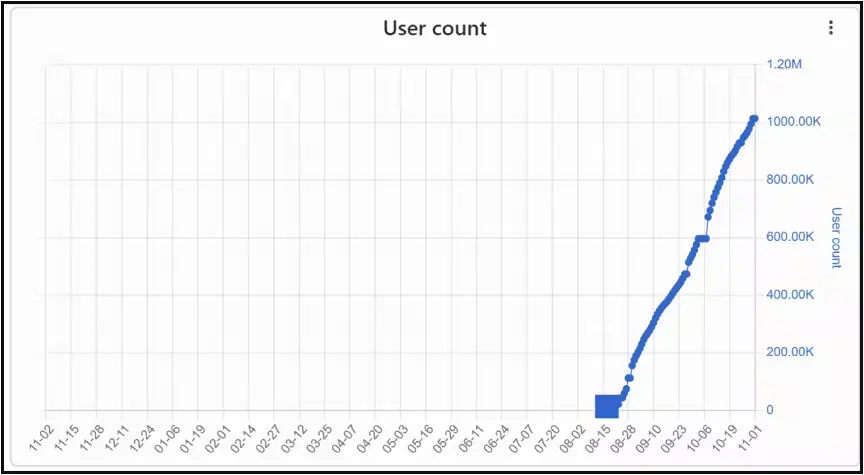
Three malicious Chrome extensions posing as VPN (Virtual Private Networks) infected were downloaded 1.5 million times, acting as browser hijackers, cashback hack tools, and data stealers.
According to ReasonLabs, which discovered the malicious extensions, they are spread via an installer hidden in pirated copies of popular video games like Grand Theft Auto, Assassins Creed, and The Sims 4, which are distributed from torrent sites.
ReasonLabs notified Google of its findings, and the tech giant removed the offending extensions from the Chrome Web Store, but only after those had amassed a total of 1.5 million downloads.
Specifically, the malicious extensions were netPlus (1 million installs), netSave, and netWin (500,000 installs).
Most infections are in Russia and countries like Ukraine, Kazakhstan, and Belarus, so the campaign appears to target Russian-speaking users.
Planting fake VPN extensions
ReasonLabs discovered over a thousand distinct torrent files that deliver the malicious installer file, which is an electron app measuring between 60MB and 100MB in size.
The installation of the VPN extensions is automatic and forced, taking place on the registry level, and does not involve the user or require any action on the victim’s side.
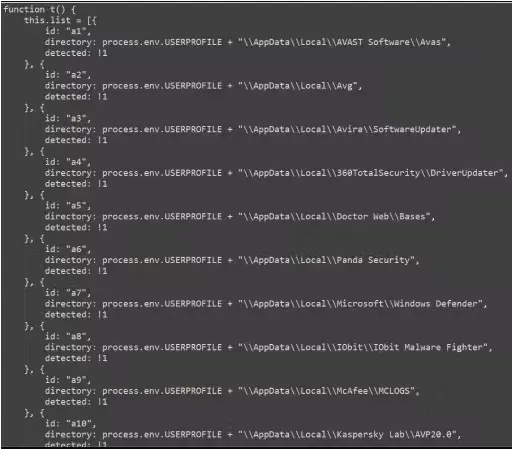
Eventually, the installer checks for antivirus products on the infected machine, then drops netSave on Google Chrome and netPlus on Microsoft Edge, covering either use case.
The malicious extensions use a realistic VPN user interface with some functionality and a paid subscription option to create a sense of authenticity.
Code analysis shows that the extension also has access to “tabs,” “storage,” “proxy,” “webRequest,” “webRequestBlocking,” “declarativeNetRequest,” “scripting,” “alarms,” “cookies,” “activeTab,” “management,” and “offscreen.”
ReasonLabs points out that the abuse of the ‘offscreen’ permission enables the malware to run scripts through the Offscreen API and stealthily interact with the web page’s current DOM (Document Object Model).
This extensive access to the DOM enables the extensions to steal sensitive user data, perform browsing hijacks, manipulate web requests, and even disable other extensions installed on the browser.
Another function of the extension is to disable other cashback and coupon extensions to eliminate competition on the infected device and redirect profits to the attackers.
ReasonLabs reports the malware targets over 100 cashback extensions, including Avast SafePrice, AVG SafePrice, Honey: Automatic Coupons & Rewards, LetyShops, Megabonus, AliRadar Shopping Assistant, Yandex.Market Adviser, ChinaHelper, and Backlit.
The extensions’ communication with the C2 (command and control) servers involves data exchange concerning instructions and commands, IDing the victim, exfiltrating sensitive data, and more.
This report highlights the massive security issues around web browser extensions, many of which are highly obfuscated to make it harder to determine what behavior they exhibit.
For this reason, you should routinely check the extensions installed in your browser and check for new reviews in the Chrome Web Store to see if others are reporting malicious behavior.
