Wall Of Flippers Detects Flipper Zero Bluetooth Spam Attacks

A new Python project called ‘Wall of Flippers’ detects Bluetooth spam attacks launched by Flipper Zero and Android devices.
By detecting the attacks and identifying their origin, users can take targeted protection measures, and culprits can potentially be held accountable for their actions.
Not an innocent prank
The ability to launch Bluetooth LE (BLE) spam attacks using the Flipper Zero portable wireless pen-testing and hacking tool was first demonstrated in September 2023 by security researcher ‘Techryptic.’
At the time, the attack involved spamming Apple devices with bogus Bluetooth connection notifications, so it appeared more like a prank than anything truly dangerous.
The idea was quickly adopted by other developers who created a custom Flipper Zero firmware that could launch spam attacks against Android smartphones and Windows laptops.
Soon after, developer Simon Dankelmann ported the attack to an Android app, allowing people to launch Bluetooth spam attacks without needing a Flipper Zero.
However, people attending the recent Midwest FurFest 2023 conference discovered first-hand that the consequences of these Bluetooth spam attacks can go far beyond the scope of a harmless prank.
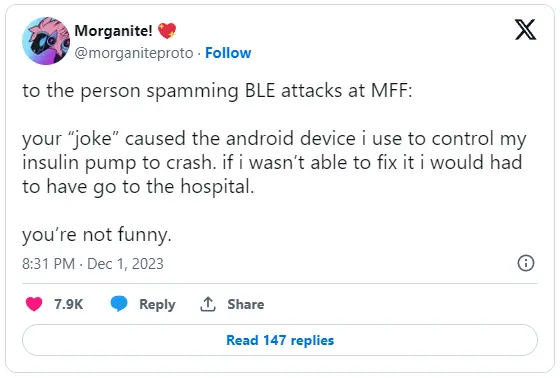
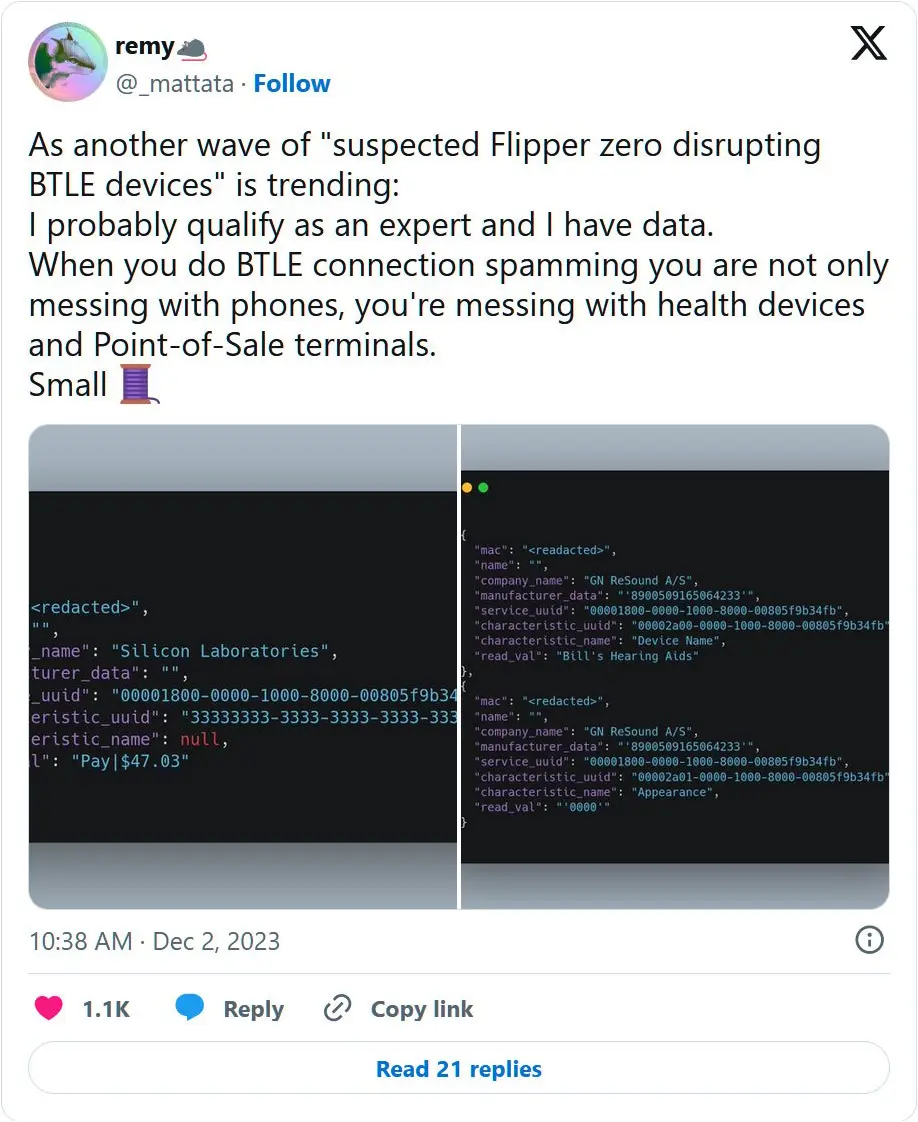
Many reported severe business disruption with their Square payment readers, and others faced more threatening situations, like causing an insulin pump controller to crash.
People using Bluetooth-enabled hearing aids and heart rate monitoring tools also reported disruption, which could put their well-being at risk.
Greynoise vulnerability researcher Remy shaerd a thread on Twitter about the dangers of these types of attacks, warning that conducting BLE spam can have serious health ramifications for those impacted.
“For BTLE enabled medical equipment, at minimum a disruption results in a degraded quality of life for those affected,” warned Remy in a conversation with BleepingComputer about BLE attacks.
“Some conditions may not be life threatening to have disruptions. Others may not be so lucky.”
While some claim that Apple has quietly introduced a mitigation for the BLE attacks in iOS 17.2, the problem has not been addressed in Android at this time.
Furthermore, BleepingComputer’s tests sending BLE spam to iOS devices from an Android app continued to work after installing iOS 17.2.
BleepingComputer contacted Google about their plans for these attacks in Android, but a response was not immediately available.
Wall of Flippers
The Wall of Flippers (WoF) project aims to detect attackers conducting BlueTooth LE spam attacks so people on the receiving end can respond appropriately.
The Python script, which, for now, can run on Linux and Windows, is designed to be run continuously, constantly updating the user with the status of nearby BTLE devices, any potential threats, and general activity.
The main display features an ASCII art header, tables of live and offline devices, and detected BLE attack packets.
The script scans for BTLE packets in the vicinity and analyzes the transmitted packets against a set of predefined patterns considered to be indicative of malicious activity.
Wall of Flippers can currently detect the following at this time, but the project is a work in progress and will continue to get updates:
- Flipper Zero detection (BT must be enabled)
- Flipper archiving (saving past data)
- iOS crash and popup BTLE detection
- Android crash and popup BTLE detection
- Windows Swift Pair BTLE detection
- LoveSpouse BTLE detection
While listening passively, WoF captures the MAC address of the spamming device, which is a primary device identifier, the signal strength, which may be used to determine the attacker’s proximity, and the data contained in the packets.
Instructions on installing WoF and setting up the project can be found on the developer’s GitHub repository.
BleepingComputer has not tested WoF and cannot provide guarantees about the safety of the script, so be sure to inspect the code before installing.