FBI: Dual ransomware attack victims now get hit within 48 hours

The FBI has warned about a new trend in ransomware attacks where multiple strains are deployed on victims’ networks to encrypt systems in under two days.
FBI’s warning comes in the form of a Private Industry Notification prompted by trends observed starting July 2023.
The federal law enforcement agency explains that ransomware affiliates and operators have been observed using two distinct variants when targeting victim organizations. Variants used in these dual ransomware attacks include AvosLocker, Diamond, Hive, Karakurt, LockBit, Quantum, and Royal.
“This use of dual ransomware variants resulted in a combination of data encryption, exfiltration, and financial losses from ransom payments,” the FBI said.
“Second ransomware attacks against an already compromised system could significantly harm victim entities.”
48 hours between ransomware attacks
In contrast to the past, when ransomware groups typically required a minimum of 10 days to execute such attacks, now the vast majority of ransomware incidents targeting the same victim take place within a mere 48-hour timeframe of each other, according to FBI’s data.
Coveware CEO & Co-Founder Bill Siegel also told BleepingComputer that double-encryption has been a thing for years, with some companies facing re-extortion as the threat actor does not provide decryptors for both ransomware attacks.
“There are some threat actor groups that intentionally use two different variants on every attack. For instance, we regularly see MedusaLocker and Globemposter used at the same time by the same threat actor on a single victim,” Siegel said.
“Situations where the initial access broker sells access to the network to two different ransomware affiliates that use different brands of ransomware. Both affiliates are then in the network, impacting machines in close time proximity to each other.”
Additionally, the FBI says that starting in early 2022, multiple ransomware gangs have begun adding new code to their custom data theft tools, wipers, and malware to evade detection.
In other incidents, malware containing data-wiping functionality was configured to remain dormant on compromised systems until a predetermined time. At that point, it would execute to destroy data on targets’ networks at periodic intervals.
Breached three times in two months
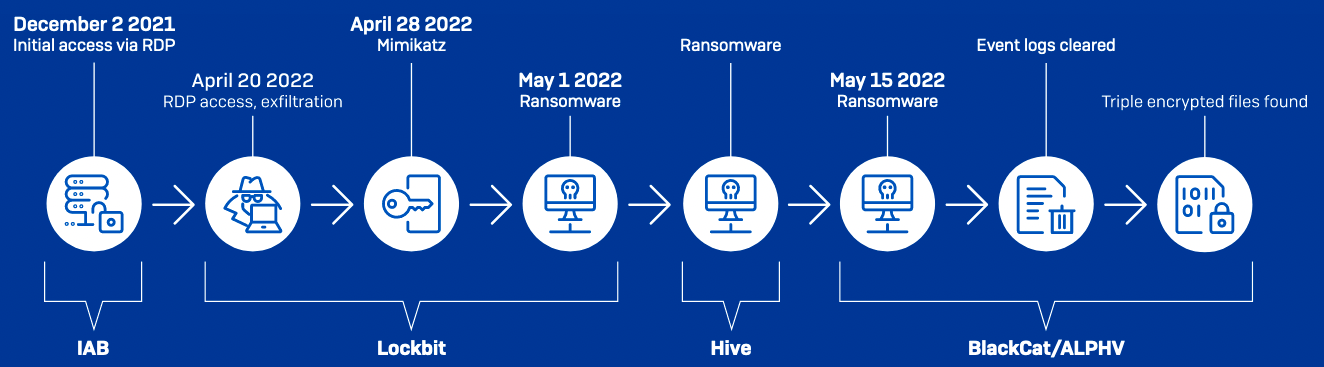
In one such attack that started last year, in April, an automotive supplier was breached three times by LockBit, Hive, and ALPHV/BlackCat affiliates within just two months, according to Sophos X-Ops incident responders.
While the victim organization was busy restoring systems encrypted with LockBit and Hive ransomware after the first breach, an ALPHV/BlackCat affiliate connected to previously compromised devices to steal data and—once again—lock files with their own encrypter.
To make things even worse, the incident responders discovered that some of the victim’s files had been encrypted up to five times.
“Because the Hive attack started 2 hours after Lockbit, the Lockbit ransomware was still running – so both groups kept finding files without the extension signifying that they were encrypted,” the Sophos team said.
How to defend against ransomware attacks
The FBI advises organizations to maintain close connections with FBI Field Offices in their region. These relationships will allow the FBI to aid with the identification of vulnerabilities and the mitigation of potential threat-related activities.
Network defenders are also advised to apply mitigation measures included in the FBI’s Private Industry Notification published on Thursday to limit the attackers’ use of common system and network discovery techniques and reduce the risk of ransomware attacks.
They’re urged to keep all systems up-to-date and conduct thorough scans of their infrastructures to identify potential backdoors or vulnerabilities introduced by the attackers as fail-safes that would enable them to regain access to the network if their access is blocked.
Defenders should also secure services like VNC, RDP, and other remote access solutions accessible from external sources. Access should be restricted solely through VPN and exclusively granted to accounts with strong passwords and enforced multi-factor authentication (MFA).
Another recommended practice includes network segmentation, where critical servers are isolated within VLANs to enhance security. Furthermore, conducting comprehensive scans and audits across the entire network is crucial to identifying devices vulnerable to exploitation due to a lack of necessary patches.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.


