Free Akira ransomware decryptor helps recover your files

Cybersecurity firm Avast has released a free decryptor for the Akira ransomware that can help victims recover their data without paying the crooks any money.
Akira first appeared in March 2023 and made a name for itself by quickly amassing victims as it targeted organizations worldwide in a broad range of sectors.
Starting in June 2023, Akira operators began deploying a Linux variant of their encryptor to attack VMware ESXi virtual machines, increasing the exposure to the group’s encryption attacks.
Akira encryption
Avast’s analysis of Akira’s encryption scheme confirms previous reports, describing that the malware uses a symmetric key generated by CryptGenRandom, which is then encrypted by a bundled RSA-4096 public key and appended to the end of an encrypted file.
As the threat actors are the only ones to possess the private RSA decryption key, it should have prevented anyone else from decrypting the files without first paying a ransom.
The Windows and Linux versions of Akira ransomware are very similar in how they encrypt devices. However, the Linux version uses the Crypto++ library instead of Windows CryptoAPI.

Avast does not explain how it cracked Akira’s encryption, but the security firm may have exploited the ransomware’s partial file encryption approach.
Akira on Windows encrypts files only partially for a speedier process, following a different encryption system depending on the file size.
For files smaller than 2,000,000 bytes, Akira will only encrypt the first half of the file contents.
For files larger than 2,000,000 bytes, the malware will encrypt four blocks based on a pre-calculated block size determined by the file’s total size.
The Linux version of Akira gives operators an “-n” command line argument that allows them to determine precisely what percentage of the victim’s files should be encrypted.
Unfortunately, now that a decryptor has been released, the Akira ransomware operation will likely pore over their code to find the flaw in their encryption and fix it, preventing future victims from recovering files for free.
The Avast decryptor
Avast has released two versions of its Akira decryptor software, one for 64-bit and one for 32-bit Windows architectures.
The security firm recommends using the 64-bit version because cracking the password requires a lot of system memory.
Users need to provide the tool with a pair of files, one encrypted by Akira and one in its original plain-text form, to allow the tool to generate the correct decryption key.
“It is extremely important to pick a pair of files that are as big as you can find,” warns Avast.
“Due to Akira’s block size calculation, there may be dramatic difference on the size limit even for files that differ by a size of 1 byte.”
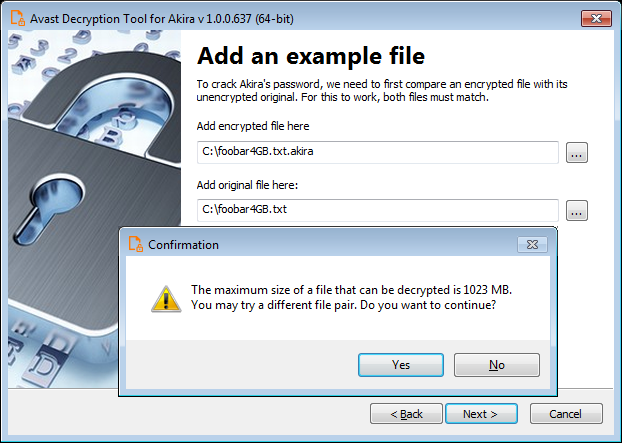
The original file’s size will also be the upper limit of a file that can be decrypted by Avast’s tool, so picking the largest available is crucial for complete data restoration.
Finally, the decryptor offers the option to back up encrypted files before attempting to decrypt them, which is recommended, as your data may get irreversibly corrupted if something goes wrong.
Avast says that they are working on a Linux decryptor, but victims can use the Windows version for now to decrypt any files that were encrypted in Linux.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.


