Hackers exploit MinIO storage system to breach corporate networks

Hackers are exploiting two recent MinIO vulnerabilities to breach object storage systems and access private information, execute arbitrary code, and potentially take over servers.
MinIO is an open-source object storage service offering compatibility with Amazon S3 and the ability to store unstructured data, logs, backups, and container images of up to 50TB in size.
Its high performance and versatility, especially for large-scale AI/ML and data lake applications, make MinIO a popular, cost-effective choice.
The two vulnerabilities found chained in attacks by Security Joes’ incident responders are CVE-2023-28432 and CVE-2023-28434, two high-severity issues impacting all MinIO versions before RELEASE.2023-03-20T20-16-18Z.
The two vulnerabilities were disclosed and fixed by the vendor on March 3, 2023.
Evil MinIO attacks
During an incident response engagement, Security Joes analysts discovered that attackers attempted to install a modified version of the MinIO application, named Evil MinIO, which is available on GitHub.
As part of the attack, Evil MinIO chains both the CVE-2023-28432 information disclosure and the CVE-2023-28434 flaws to replace the MinIO software with modified code that adds a remotely accessible backdoor.
The attack started with the attackers doing some social engineering to convince a DevOPS engineer to downgrade to an earlier version of the MinIO software that is impacted by the two vulnerabilities.
Once installed, the hackers exploited CVE-2023-28432 to remotely access the server’s environment variables, including the MINIO_SECRET_KEY and MINIO_ROOT_PASSWORD variables.
These administrative credentials allow the hackers to access the MinIO admin console using the MinIO client. Using this client, the threat actors modify the software update URL to one they crontrol, to push a malicious update.
As part of this process, the exploit chain uses the CVE-2023-28434 flaw to replace the legitimate .go source code file with a tampered one.
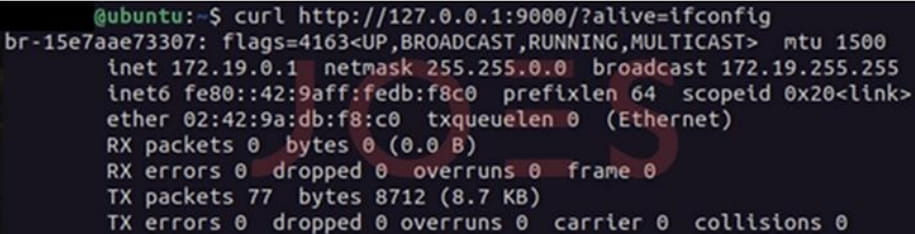
This malicious update is identical to the legitimate MinIO app but features additional code that allows executing commands remotely to a compromised server through the following URLs:
http://vulnerable.minio.server/?alive=[CMD_TO_EXECUTE]
http://vulnerable.minio.server/anything?alive=[CMD_TO_EXECUTE]
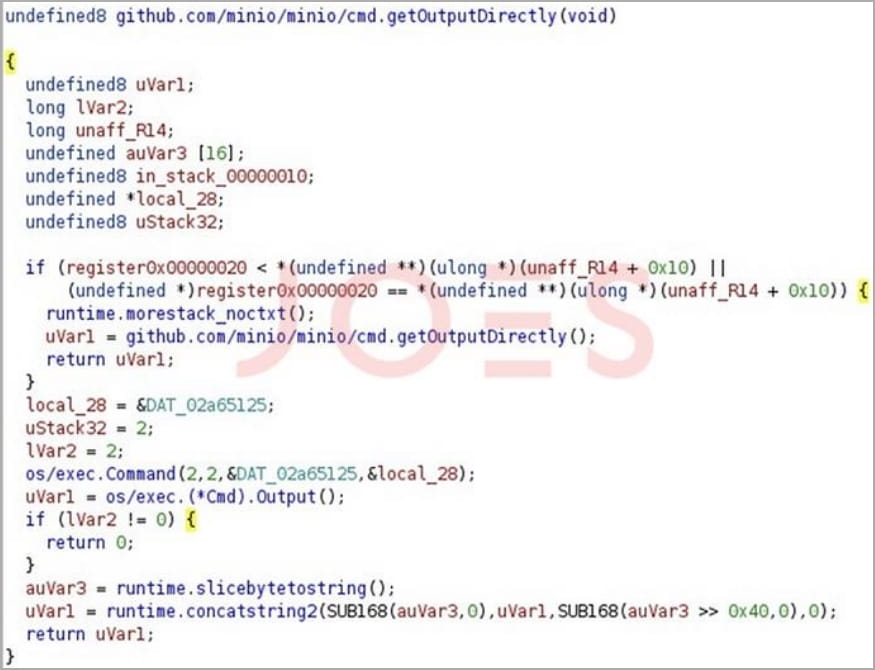
In the incident seen by Security Joes, analysts saw the threat actors using this backdoor to run Bash commands and download Python scripts.
“This endpoint functions as a built-in backdoor, granting unauthorized individuals the ability to execute commands on the host running the application,” explain the researchers.
“Notably, the executed commands inherit the system permissions of the user who initiated the application. In this instance, due to inadequate security practices, the DevOps engineer launching the application held root-level permissions,” the analysts added.
Security Joes reports that the backdoor in Evil MinIO is not detected by engines on the Virus Total scanning platform, despite the tool being published a month ago.
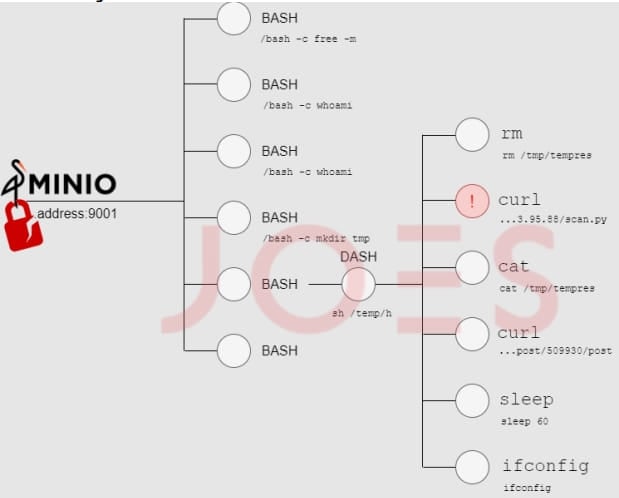
Post-compromise activity
Having breached the object storage system, the attackers establish a communication channel with the command and control (C2) server from where it fetches additional payloads that support post-compromise activity.
The payloads are downloaded on Linux via ‘curl’ or ‘wget’ and on Windows via ‘winhttpjs.bat’ or ‘bitsadmin,’ and include the following:
- System profiling script – collects system information like user details, memory, cronjobs, and disk usage.
- Network reconnaissance script – identifies accessible network interfaces, hosts, and ports.
- Windows account creation script – creates user accounts on the compromised systems named either “support” or “servicemanager.”
- PING scan script – identifies accessible assets within the compromised network using the asyncio Python module.
- China Chopper-like webshell – a one-line webshell that features similarities to China Chopper.
Security Joes warns that there are 52,125 MinIO instances exposed on the public internet and about 38% of them were confirmed to run a non-vulnerable software version.
That said, cloud system admins should move quickly to apply the available security update to protect their assets from Evil MinIO operators.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![[GLOBAL] - Ransomware Victim: loraincountyauditor[.]gov 5 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

