Hackers mostly targeted Microsoft, Google, Apple zero-days in 2022

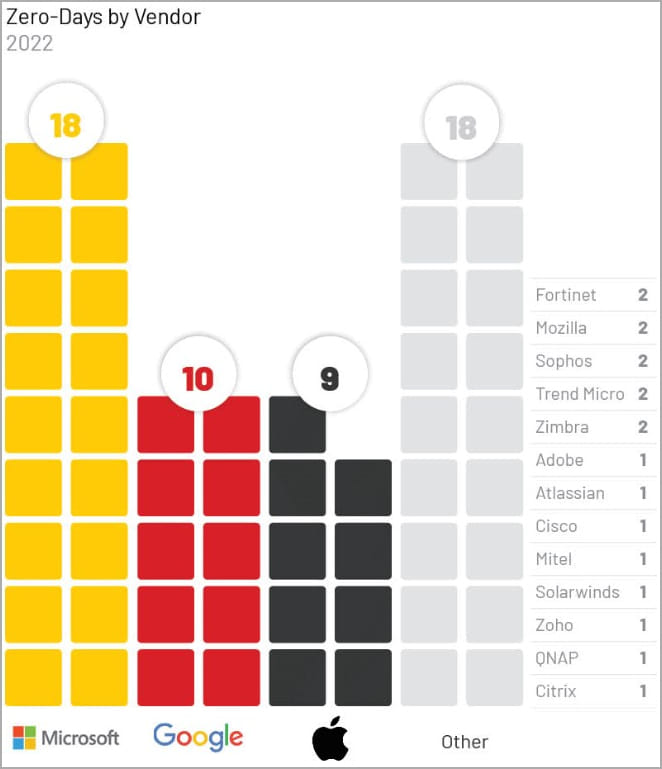
Hackers continue to target zero-day vulnerabilities in malicious campaigns, with researchers reporting that 55 zero-days were actively exploited in 2022, most targeting Microsoft, Google, and Apple products.
Most of these vulnerabilities (53 out of 55) enabled the attacker to either gain elevated privileges or perform remote code execution on vulnerable devices.
Zero-day vulnerabilities are security weaknesses in software products that are publicly disclosed or exploited before a developer knows about it or releases a fix.
They are considered extremely valuable for hackers because exploiting them is easy and stealthy since there are no protection measures or specific monitoring to track and stop the attacks.
According to Mandiant, most of last year’s zero-day flaws were exploited by Chinese state-sponsored actors and most concerned operating systems, web browsers, and network management products.

In 2021, threat actors exploited 80 zero-day flaws in various products to perform security breaches, so the last year shows a slight decline. Still, 2022 surpasses all other years regarding the number of zero days flaws actively exploited.
Mandiant says 2021 was a particularly exceptional year for zero-day exploitation, and the cybersecurity company expects the trend to continue upward for 2023.
However, the ongoing migration to cloud services may reduce the number of disclosed zero-day flaws, as cloud vendors follow a different approach in security reporting.
2022 zero-day landscape
Out of the 55 zero-day flaws exploited in 2022, 13 were exploited by cyber-espionage groups, while Chinese cyberspies leveraged 7.
Russian threat actors exploited two flaws, with one overlap, North Koreans another two, while Mandiant couldn’t determine the origin of the espionage attacks in three cases.
Cyberespionage groups have preferred targeting “edge infrastructure” products as those usually lack detection solutions and are less likely to raise alarms.
Also, their exploitation does not require interaction with the victim and can facilitate lateral movement within the compromised network.
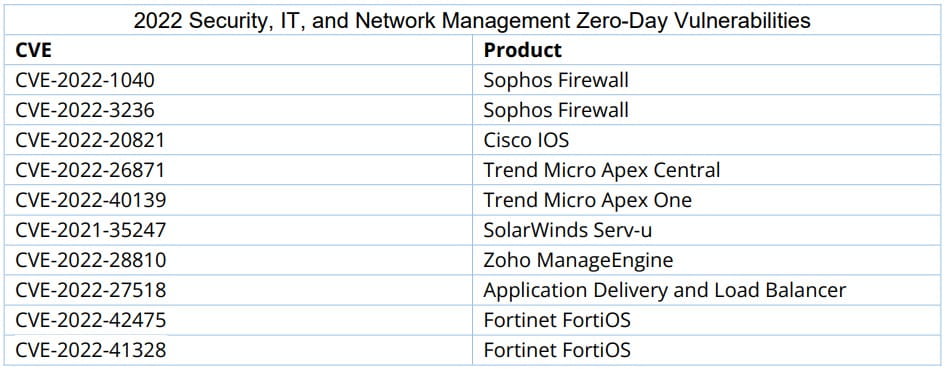
Financially motivated threat actors are considered responsible for exploiting four zero-day vulnerabilities last year, with three attributed to ransomware actors.
Mandiant says it could not infer the exact motivation for exploiting 16 zero-day vulnerabilities.
Despite the efforts of Western governments to curb the problem of commercial spyware, Mandiant reports it continued to be a problem in 2022, with at least three zero-days discovered by semi-legal malware vendors.
Regarding the targeted products, Windows was affected by 15 zero-day flaws in 2022, Chrome comes second with nine actively exploited vulnerabilities, iOS third with 5 zero days, and macOS fourth with four zero-day problems.
Protecting systems from zero-day exploitation can be challenging since no patches exist for the targeted vulnerabilities; however, organizations can still take steps to mitigate the impact of such attacks:
- Do not expose internal devices to the Internet unless necessary, and if doing so, implement allow lists based on IP addresses.
- Utilize private tunnels or VPNs to access servers rather than exposing them to the Internet.
- Apply the principle of least privilege to limit user access rights to the minimum necessary.
- Implement network segmentation to limit the spread of an attack in the case of a breach.
- Use network monitoring, firewalls, email and web filtering products, and endpoint security tools.
It is also advised that admins subscribe to product announcements or security bulletins from their vendors to stay on top of new updates as they are released.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.





![[NITROGEN] - Ransomware Victim: Progressive Auto Group 12 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

