Hat trick for Google as it patches two more zero-days in Chrome
Slightly over a week ago we advised you to update your Chrome browser. That warning came only a week or so after we advised you to update your Chrome browser. Things are getting a bit repetitive round here.
Today, we are compelled to repeat that statement as Google has issued patches for two new zero-day vulnerabilities. Someone tipped Google off about them, although the source(s) wish to remain anonymous. Again, the vulnerabilities being zero-days means they are already being used in real life attacks.
Zero-days are a valuable commodity for cybercriminals since there are (until yesterday) no patches for the vulnerability and every unpatched system is another potential victim. Which is exactly why we advise to update your Chrome as soon as possible.
What is the problem that’s being fixed?
Publicly disclosed computer security flaws are listed in the Common Vulnerabilities and Exposures (CVE) list—a dictionary that provides definitions for publicly disclosed cybersecurity vulnerabilities and exposures. The goal of CVE is to make it easier to share data across separate vulnerability capabilities (tools, databases, and services).
In this case, the two vulnerabilities were catalogued as:
CVE-2020-16013: Inappropriate implementation in V8. Sound familiar? V8 was also the subject of CVE-2020-16009 where researchers stated it must have something to do with the way the Chrome browser handles Javascript.
CVE-2020-16017: Use after free in site isolation. Site isolation is the feature that makes every website run in a separate process without interaction with each other. Each will be running in a sandbox which provides an additional line of defense. Use after free may indicate that after closing a site the memory location for it may not be freed up properly.
How do I install Chrome patches?
The easiest way to do it is to allow Chrome to update automatically, which basically uses the same method as outlined below but does not require your attention. But you can end up lagging behind if you never close the browser or if something goes wrong, such as an extension stopping you from updating the browser.
So, it doesn’t hurt to check now and then. And now would be a good time, given the zero-day vulnerabilities. My preferred method, which also allows me to keep track, is to have Chrome open the page chrome://settings/help which you can also find by clicking Settings > About Chrome.
If there is an update available, Chrome will notify you and start downloading it. Then it will tell you all you have to do to complete the update is Relaunch the browser.
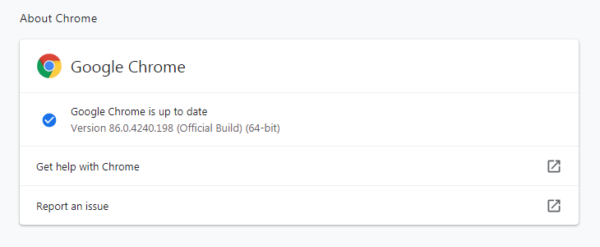
What version do I need?
After the update, your version number should be 86.0.4240.198 or later. You will now be protected against the vulnerabilities. Google states that the stable channel has been updated to 86.0.4240.198 for Windows, Mac, and Linux which will roll out over the coming days/weeks. Also keep an eye on your Chromium based browsers (Opera, Edge, and others) since they may require updates as well.
Stay safe, everyone!
The post Hat trick for Google as it patches two more zero-days in Chrome appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[QILIN] - Ransomware Victim: Culver's Lawn & Landscape, Inc[.] 3 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

