Hong Kong residents targeted in malvertising campaigns for WhatsApp, Telegram
Malvertising is a powerful malware or scam delivery mechanism that makes it easy to target specific geographies or even users. A recent article from the South China Morning Post discussed an increase in malicious webpages for the popular WhatsApp communication tool, driven via malicious Google ads. The paper described how these ads appeared to be exclusively targeted at people from Hong Kong and have caused losses of about USD$300K last month.
We started investigating this situation and were able to identify what may be a similar campaign. The decoy sites we saw used a similar page than the web version of WhatsApp to trick victims into scanning a QR code to link their new device. Instead, it wasn’t the user’s device that was added to the WhatsApp account, but rather the threat actor’s.
We also found another campaign using an ad for messaging tool Telegram, to lure victims into downloading a malicious version of the program. Again, this attack was targeted at residents of Hong Kong.
We have reported the malicious ads to Google and worked with partners to take down the infrastructure used in these campaigns.
Malicious WhatsApp ad leads to QR code page
Just like the South China Morning Post stated that users were seeing malicious ads for WhatsApp, we were able to find one immediately after switching our online profile to use a Hong Kong IP address:
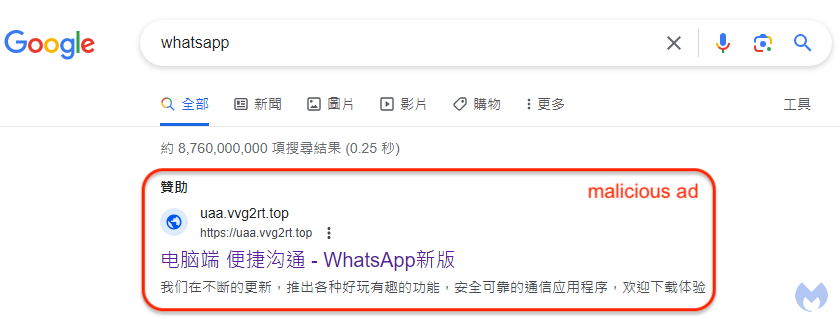
The text of the ad reads as follows (translated from Chinese):
WhatsApp New Version – WhatsApp Official Authorization
We are constantly updating and launching various fun and interesting functions as well as safe and reliable communication applications. Welcome to download and experience it. The cross-platform application brings you a reliable experience, and you can send private messages to your friends at any time.
Clicking on the ad leads to a convincing lookalike site in Chinese that pretends to be WhatsApp Web:
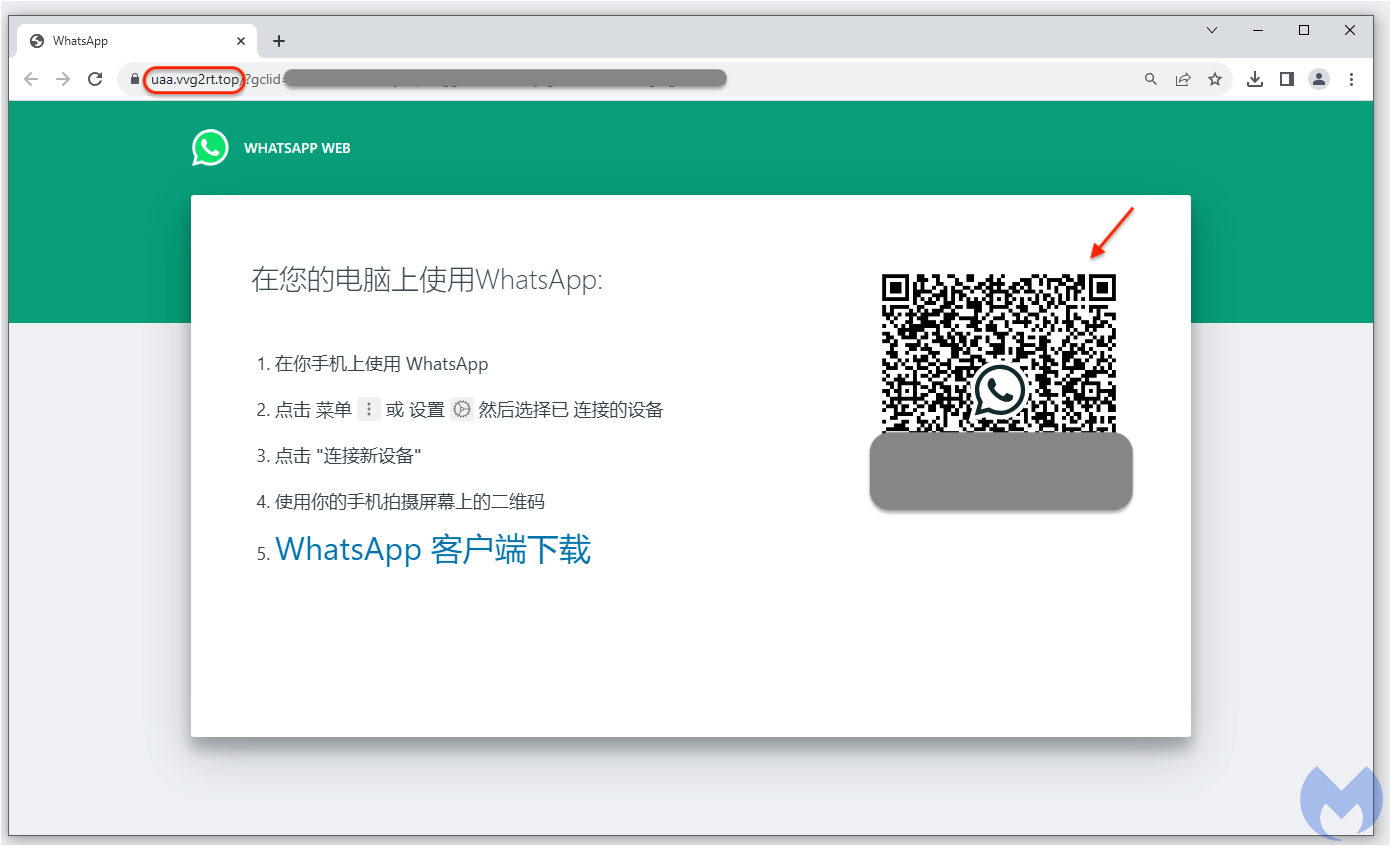
What’s interesting, and works well as a lure, is the fact that WhatsApp is not just a mobile phone app, but does indeed have a web version for computers as well. The real domain for it is hosted at web.whatsapp.com and also uses a QR code to add a linked device to your account. What this means is that you can use WhatsApp on your PC or Mac after you scan the QR code and authorize that new device from your phone.
The issue here is that the QR code you are scanning is from a malicious site that has nothing to do with WhatsApp:
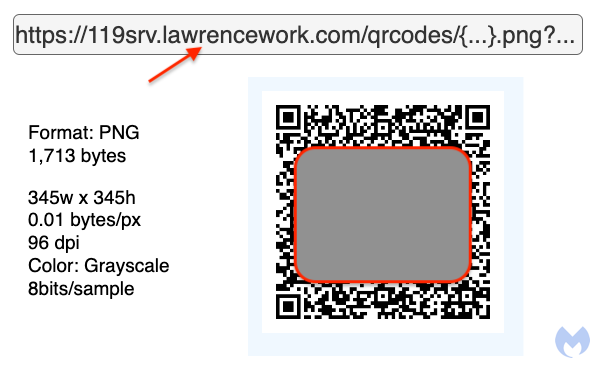
The domain used to generate those QR codes (lawrencework[.]com) was registered just two days ago. A search on urlscan.io reveals that it is associated with several other fake WhatsApp pages. We tested the QR code by adding it from a burner phone with a brand new WhatsApp account without any previous linked devices. A few seconds later, we saw a new device was added (Google Chrome running on Mac OS):

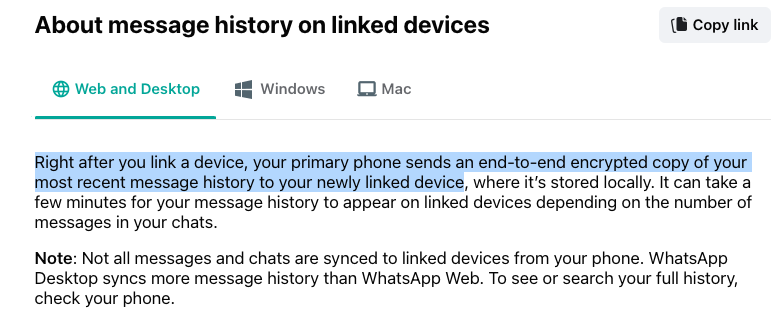
While we could not get more information (IP address, geolocation) about this new device, we knew it was not ours. When you link a new device to your WhatsApp account, the saved chat history is synced to it. This means that an attacker can essentially read your entire past and future conversations and has access to your saved contacts.
Telegram ad links to malware
The second ad we saw related to this campaign was using Telegram as a lure. We know it is related to the above WhatsApp attack because the ad is from the same advertiser.
 The text of the ad reads as follows (translated from Chinese):
The text of the ad reads as follows (translated from Chinese):
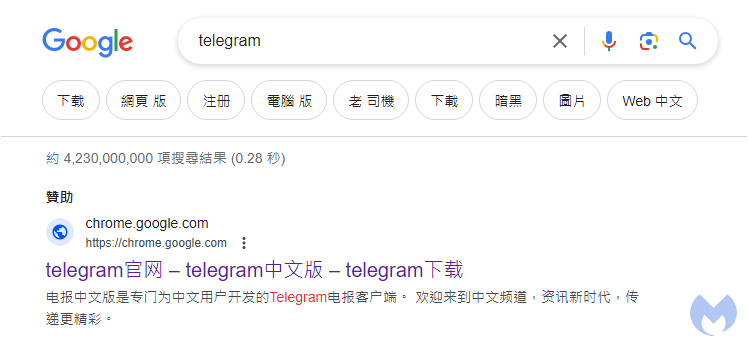
telegram official website – telegram Chinese version – telegram download Telegram Chinese version is a Telegram client specially developed for Chinese users. Welcome to the Chinese channel, a new era of information, delivering more exciting information
It links to a Google Docs page pretending to be a download site:
Telegram instant messaging – simple, fast, secure and syncs across all your devices. It is one of the most downloaded apps in the world, with over 500 million active users. The latest official Telegram Chinese computer version TG-Chinese version: Click to download TG-PC: Click to download
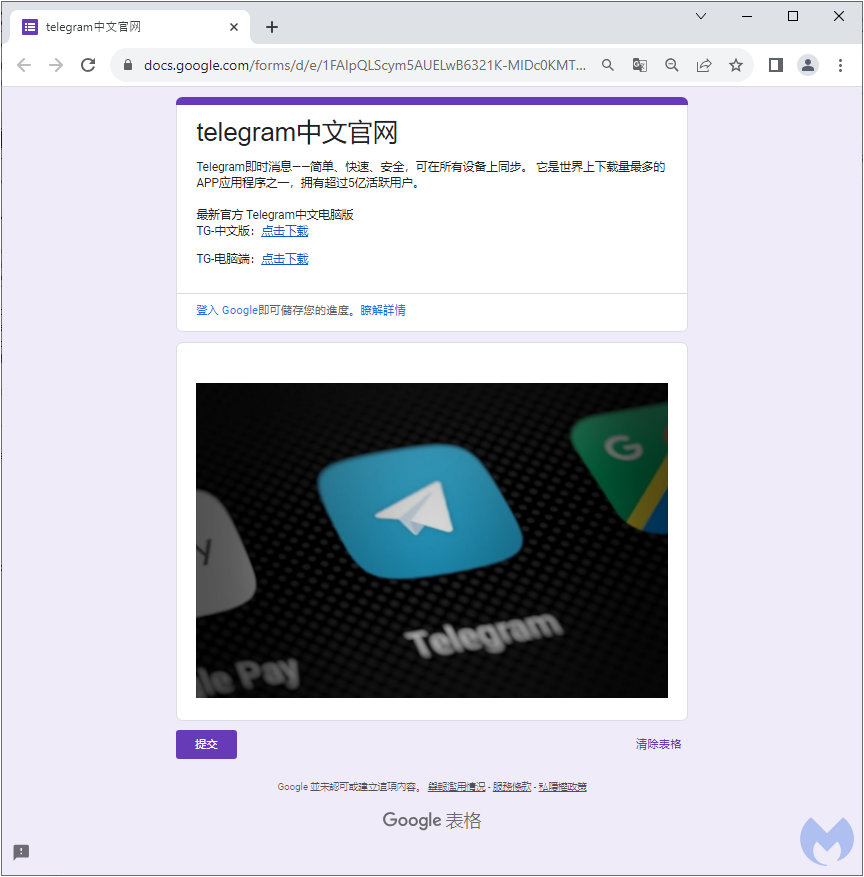
The two links (identical) download an MSI installer from the following URL:
kolunite.oss-ap-southeast-7.aliyuncs[.]com/HIP-THH-19-1.msi
This installer has been injected with malware, which we can see once we execute it:
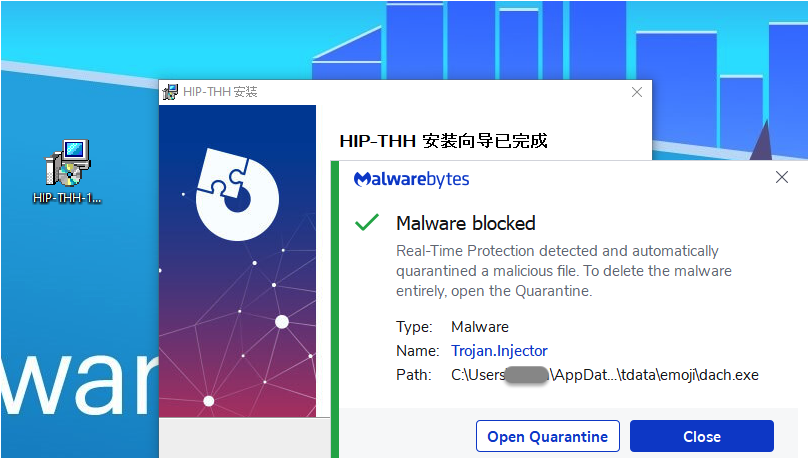
Targeted malvertising and motives
These two campaigns abusing the WhatsApp and Telegram brands could be used for a variety of reasons. We did not investigate further what the ultimate ploy was, although both lead to data theft, impersonation and malware. The threat actor could use any private information from past conversations, phish the victim’s contacts and much more.
This was our first foray into malvertising attacks targeted at Hong Kong. Given that this special administrative region of the People’s Republic of China has a long history of tensions with Beijing, we could not help but think that malvertising campaigns such as these could be used for political reasons, although we saw no evidence of it.
Linking additional devices via QR code is a useful feature but it can also easily be abused. It’s important to be cautious when scanning QR codes by verifying which site is issuing those. It’s a good idea to periodically check which devices have access to your accounts, and revoke any that you don’t recognize.
Thanks to Nathan Collier for the assist with the QR code scanning on Android.
Indicators of Compromise
Malicious WhatsApp domains
uaa.vvg2rt[.]top
wss.f8ddcc[.]com
QR code hostname
119srv[.]lawrencework[.]com
Telegram MSI URL
kolunite.oss-ap-southeast-7.aliyuncs[.]com/HIP-THH-19-1.msi
Telegram MSI
36d11b18d3345ff743f7b003d10a0820c8c1661dd7dc279434e436de798c3a4b
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![[INCRANSOM] - Ransomware Victim: C B King Memorial School(branch) 9 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)



