Krasue RAT malware hides on Linux servers using embedded rootkits

Security researchers discovered a remote access trojan they named Krasue that is targeting Linux systems of telecommunications companies and managed to remain undetected since 2021.
They found that Krasue’s binary includes seven variants of a rootkit that supports multiple Linux kernel versions and is based on code from three open-source projects.
According to researchers at cybersecurity company Group-IB, the main function of the malware is to maintain access to the host, which may suggest that it is deployed through a botnet or sold by initial access brokers to threat actors seeking access to a particular target.
The researchers believe that the Krasue remote access trojan (RAT) may be deployed during a later stage of the attack specifically to maintain access to the victim host.
It is unclear how the malware is being distributed but it could be delivered after exploiting a vulnerability, following a credential brute force attack, or even downloaded from an untrusted source as a package or binary impersonating a legitimate product.
Krasue’s targeting appears to be limited to telecommunications companies in Thailand.

Rootkits inside
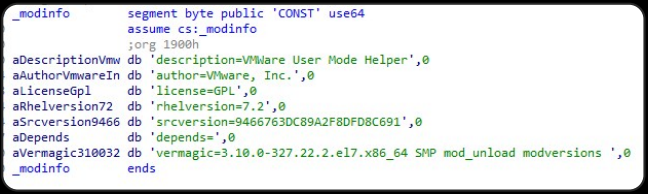
Analysis from Group-IB revealed that the rootkit inside Krasue RAT’s binary is a Linux Kernel Module (LKM) that masquerades as an unsigned VMware driver after being executed.
Kernel-level rootkits are difficult to detect and remove because they operate at the same security level as the operating system.
The rootkit supports Linux Kernel versions are 2.6x/3.10.x, which allows it to stay under the radar because older Linux servers typically have poor Endpoint Detection and Response coverage, the researchers say.
Group-IB found that all seven embedded rootkit versions feature the same system call and function call hooking capabilities and use the same fake “VMware User Mode Helper” name.

Looking at the code, the researchers determined that the rootit is based on three open-source LKM rootkits, specifically Diamorphine, Suterusu, and Rooty, all of them available since at least 2017.
The Krasue rootkit can hide or unhide ports, make processes invisible, provide root privilege, and run the kill command for any process ID. It can also cover its traces by hiding malware-related files and directories.
When communicating with the command and control (C2) server, Krasue can accept the following commands:
- ping – Reply with `pong`
- master – Set the master upstream C2
- info – Get information about the malware: main pid, child pid, and its status such as “root: gained root permissions,” “god: process is unable to be killed,” “hidden: process is hidden,” “module: rootkit is loaded”
- restart – Restart child process
- respawn – Restart main process
- god die – Kill itself
Group-IB discovered nine distinct C2 IP addresses hardcoded into the malware, with one using port 554, which is common in RTSP (Real Time Streaming Protocol) connections.
Using the RTPS application-level network protocol for C2 malware communication is not too common and could be seen as a particularity in the case of Krasue.
RTSP is a network control protocol designed for streaming media servers, helping establish and control media playback sessions for video and audio streams, media navigation, managing conferencing streams, and more.
Although the origin of Krasue malware is unknown, the researchers found in the rootkit portion some overlaps with the rootkit of another Linux malware called XorDdos.
Group-IB believes this is an indication that the two malware families have a common author/operator. It is also possible that the developer of Krasue also had access to the XorDdos code.
At this time, the type of threat actor behind Krause is still a mystery but the cybersecurity company has shared indicators of compromise and YARA rules to help defenders detect this threat and maybe encourage other researchers to publish what they know about the malware.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.


![Sliver C2 Detected - 45[.]140[.]143[.]62:31337 7 Sliver C2](https://www.redpacketsecurity.com/wp-content/uploads/2024/02/Sliver-C2-300x142.jpg)
