Lazarus hackers breached dev repeatedly to deploy SIGNBT malware

The North Korean Lazarus hacking group repeatedly compromised a software vendor using flaws in vulnerable software despite multiple patches and warnings being made available by the developer.
The fact that Lazarus breached the same victim multiple times indicates that the hackers aimed to steal source code or attempt a supply chain attack.
“This recurring breach suggested a persistent and determined threat actor with the likely objective of stealing valuable source code or tampering with the software supply chain, and they continued to exploit vulnerabilities in the company’s software while targeting other software makers,” explains Kaspersky.
The attack was discovered by Kaspersky in July 2023, which observed Lazarus employing a diverse infection chain and post-compromise toolset.
Kaspersky places this attack within the broader scope of a campaign in which Lazarus targeted various software vendors between March 2023 and August 2023.
The SIGNBT and LPEClient malware
The report mentions that Lazarus targeted legitimate security software used for the encryption of web communications. However, the exact exploitation method the hackers followed remains unknown.
The exploitation led to the deployment of the SIGNBT malware along with shellcode used for injecting the payload into memory for stealthy execution.
Persistence is established by adding a malicious DLL (‘ualapi.dll’) onto Startup to be executed by ‘spoolsv.exe,’ or performing Windows Registry modifications.
The malicious DLL file performs victim ID verification checks before it decrypts and loads the SIGNBT payload from a local filesystem path to ensure the infection proceeds onto the intended targets.
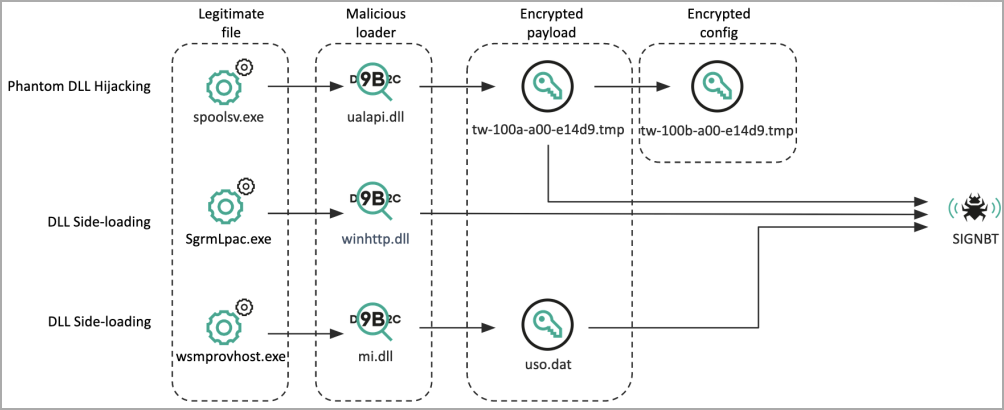
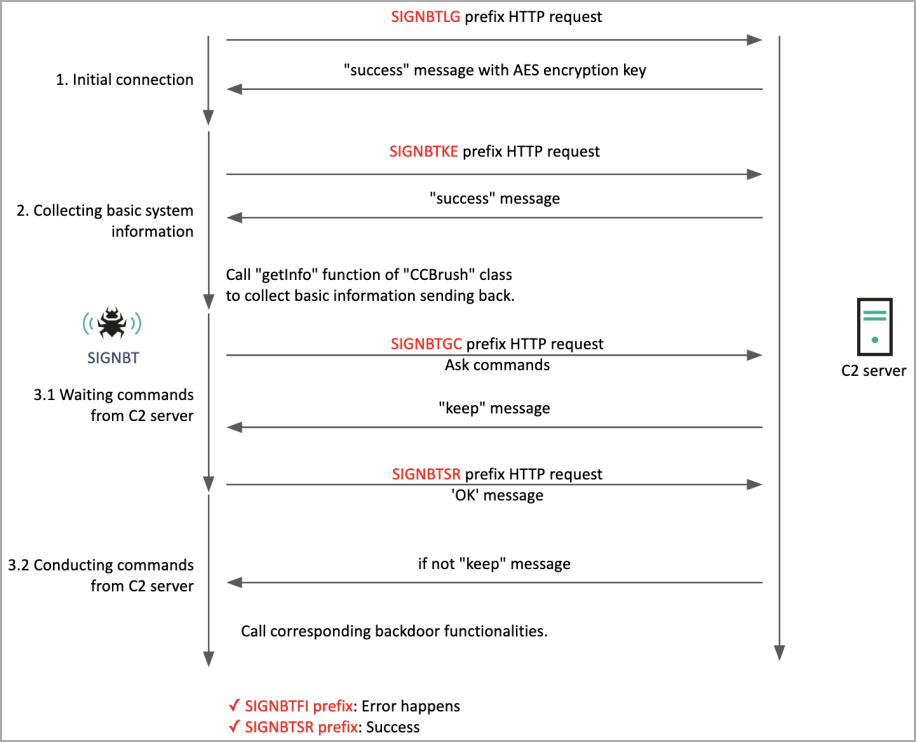
SIGNBT gets its name from the distinct strings it uses for command and control (C2) communications, sending information about the compromised system and receiving commands for execution.
The commands supported by SIGNBT are:
- CCBrush: Handles functionalities like getting information about the system, testing connectivity, and configuring settings.
- CCList: Manages processes, including obtaining a list of running processes, killing processes, running files, and DLL manipulations.
- CCComboBox: Works with the file system, such as obtaining lists of drives, changing file properties, and creating new folders.
- CCButton: Downloads and uploads files, loads into memory, and captures the screen.
- CCBitmap: Implements commonly used Windows commands and utilities.
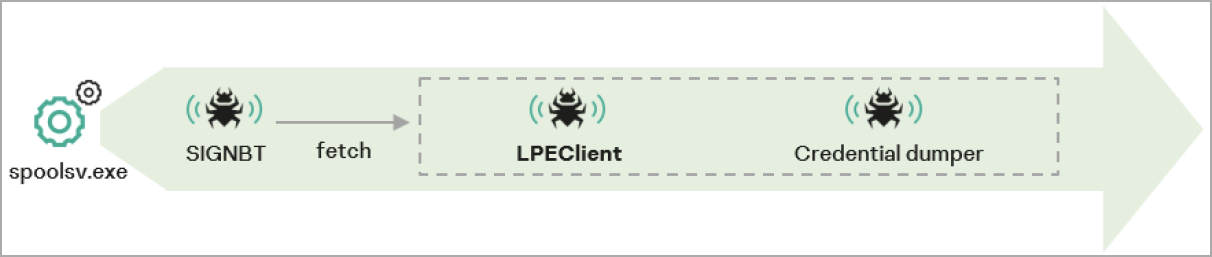
SIGNBT can also fetch additional payloads from the C2 and deploy them on the host, providing Lazarus with operational versatility.
Kaspersky has seen Lazarus leverage that feature on SIGNBT to load credential dumping tools and the LPEClient malware on compromised systems.
LPEClient is an info-stealer and malware loader on itself, which, in its latest versions, Kaspersky says demonstrates significant evolution compared to previously documented samples.
“It now employs advanced techniques to improve its stealth and avoid detection, such as disabling user-mode syscall hooking and restoring system library memory sections,” mentions Kaspersky.
Kaspersky says Lazarus incorporates the LPEClient on other campaigns it ran in 2023, albeit it used the malware at earlier infection phases to inject other payloads.
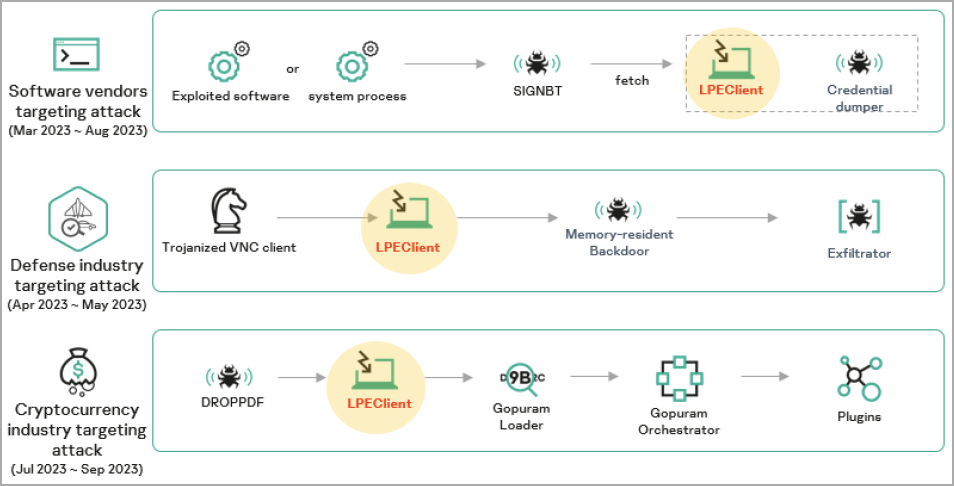
Overall, the Lazarus group remains one of the most active and dangerous threat actors, maintaining a broad targeting scope across regions and industries.
Their recent actions underscore their sophisticated tactics and persistent goals, emphasizing organizations’ need to proactively patch software and prevent easy exploitation of vulnerabilities for initial compromise.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.


