Lazarus Hackers Exploited Windows Zero Day To Gain Kernel Privileges

North Korean threat actors known as the Lazarus Group exploited a flaw in the Windows AppLocker driver (appid.sys) as a zero-day to gain kernel-level access and turn off security tools, allowing them to bypass noisy BYOVD (Bring Your Own Vulnerable Driver) techniques.
This activity was detected by Avast analysts, who promptly reported it to Microsoft, leading to a fix for the flaw, now tracked as CVE-2024-21338, as part of the February 2024 Patch Tuesday. However, Microsoft has not marked the flaw as being exploited as a zero-day.
Avast reports that Lazarus exploited CVE-2024-21338 to create a read/write kernel primitive in an updated version of its FudModule rootkit, which ESET first documented in late 2022. Previously, the rootkit abused a Dell driver for BYOVD attacks.
The new version of FudModule features significant enhancements in stealth and functionality, including new and updated techniques for evading detection and turning off security protections like Microsoft Defender and CrowdStrike Falcon.
Moreover, by retrieving most of the attack chain, Avast discovered a previously undocumented remote access trojan (RAT) used by Lazarus, which the security firm promised to share more details about at BlackHat Asia in April.
Lazarus 0-day exploitation
The malware exploited a vulnerability in Microsoft’s ‘appid.sys’ driver, a Windows AppLocker component that provides application whitelisting capabilities.
Lazarus exploits it by manipulating the Input and Output Control (IOCTL) dispatcher in the appid.sys driver to call an arbitrary pointer, tricking the kernel into executing unsafe code, thus bypassing security checks.
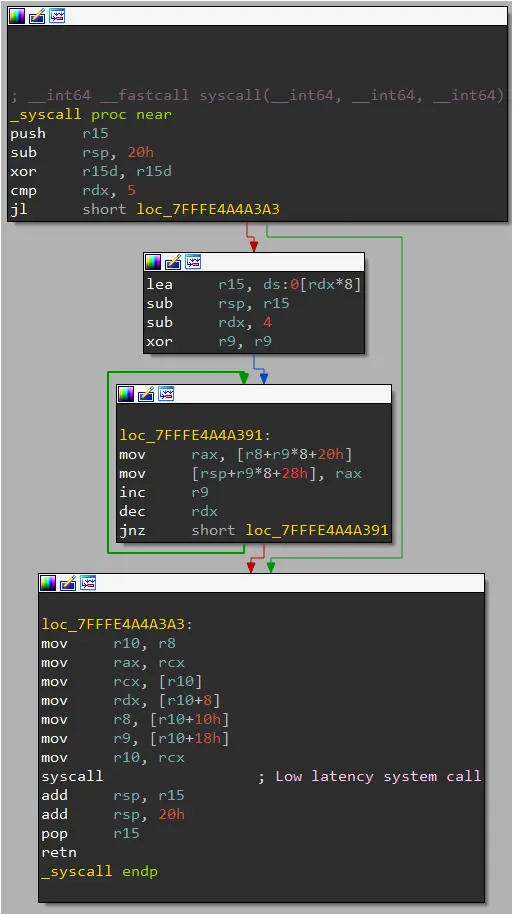
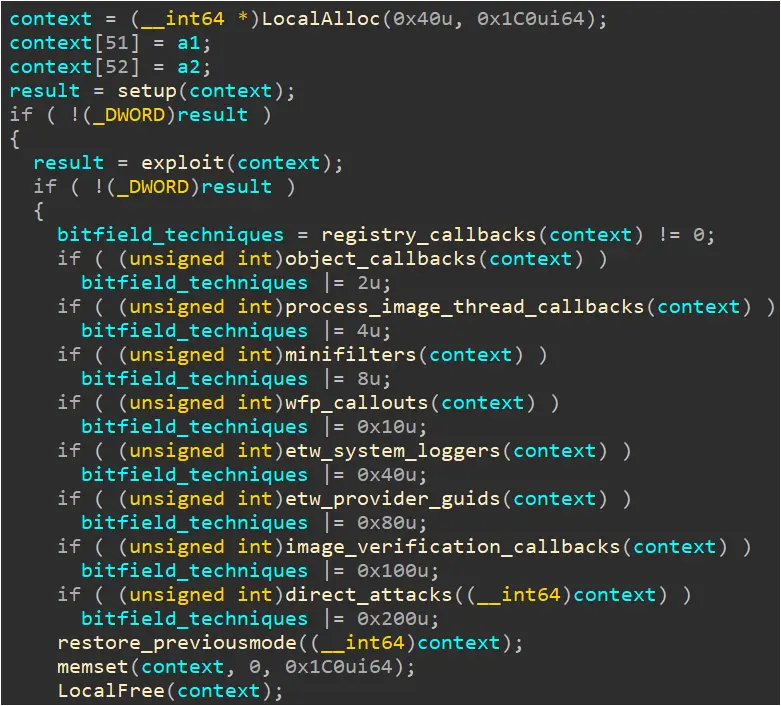
The FudModule rootkit, built within the same module as the exploit, executes direct kernel object manipulation (DKOM) operations to turn off security products, hide malicious activities, and maintain persistence on the breached system.
The targeted security products are AhnLab V3 Endpoint Security, Windows Defender, CrowdStrike Falcon, and the HitmanPro anti-malware solution.
Avast observed new stealth features and expanded capabilities in the new rootkit version, like the ability to suspect processes protected by Protected Process Light (PPL) by manipulating handle table entries, selective and targeted disruption via DKOM, enhancements in tampering with Driver Signature Enforcement and Secure Boot, and more.
Avast notes that this new exploit tactic marks a significant evolution in the threat actor’s kernel access capabilities, allowing them to launch stealthier attacks and persist on compromised systems for longer periods.
The only effective security measure is to apply the February 2024 Patch Tuesday updates as soon as possible, as Lazarus’ exploitation of a Windows built-in driver makes the attack particularly challenging to detect and stop.
YARA rules to help defenders detect activity linked to the latest version of the FudModule rootkit can be found here.
